In its latest security update, Apple included fixes for a zero-day vulnerability that would have allowed threat actors to hack iPhone, iPad and Mac devices. The flaw was tracked as CVE-2022-22620 and was described as a use-after-free error in WebKit that would allow code execution on vulnerable devices.
Apple addressed the flaw by applying an improvement in memory management on iOS 15.3.1, iPadOS 15.3.1 and macOS Monterey 12.2.1 systems: “We are aware of a report on the active exploitation of this vulnerability,” mentions a security alert from the company.
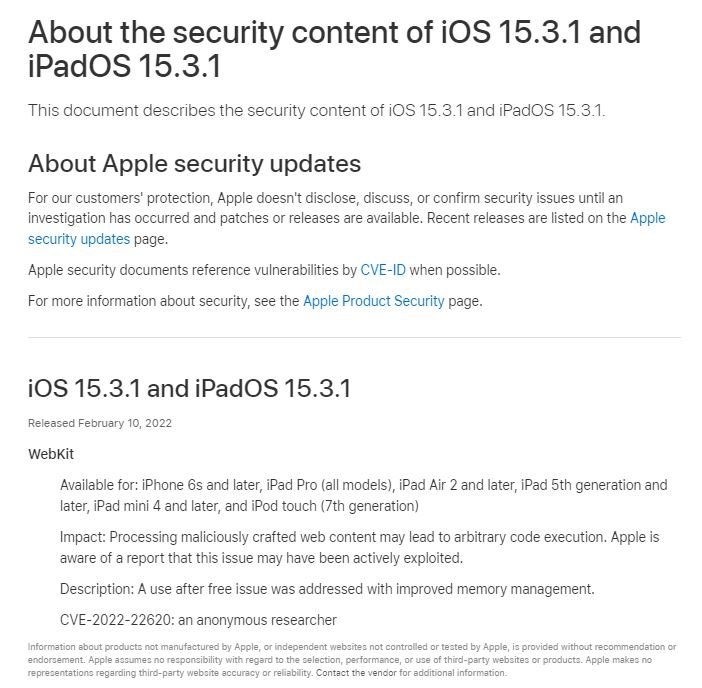
The full list of affected devices is huge because the vulnerability affects even the company’s oldest devices; among the affected devices are:
- iPhone 6s and later
- iPad Pro; iPad Air 2 and later; Fifth-generation iPad
- iPad mini 4 and later; iPod Touch 7th generation
- macOS Monterey
This vulnerability could have been exploited in highly targeted attacks, considerably limiting the scope of the incident. However, the company strongly recommends users of vulnerable devices to update as soon as possible to mitigate the risk of exploitation.
A couple of weeks ago, Apple released updates for two other actively exploited zero-day vulnerabilities. Identified as CVE-2022-22587 and CVE-2022-22594, the flaws would have allowed arbitrary code execution with kernel privileges and traced the identity of users online.
These vulnerabilities affected iPhone devices, Macs running macOS Monterey, and several old and current iPad models. While Apple has patched just three zero-day vulnerabilities this year, the company had to deal with all sorts of critical flaws over the past year in its products, so more similar flaws are expected to appear in the remainder of the year.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
