Cybersecurity specialists reported the detection of two zero-day flaws residing on QNAP Systems TS-231 network-attached storage (NAS) hardware. Tracked as CVE-2020-2509 and CVE-2021-36195, the flaws reside on legacy systems and even some non-legacy NAS computers; it should be mentioned that the flaws have already been fixed and must be downloaded from QNAP’s official platforms.
The flaws were reported a few days ago by SAM Seamless Network experts, who added some technical details about the attack. The vulnerabilities were detected in October 2020 and experts waited for the deadline to be met to reveal the flaws.
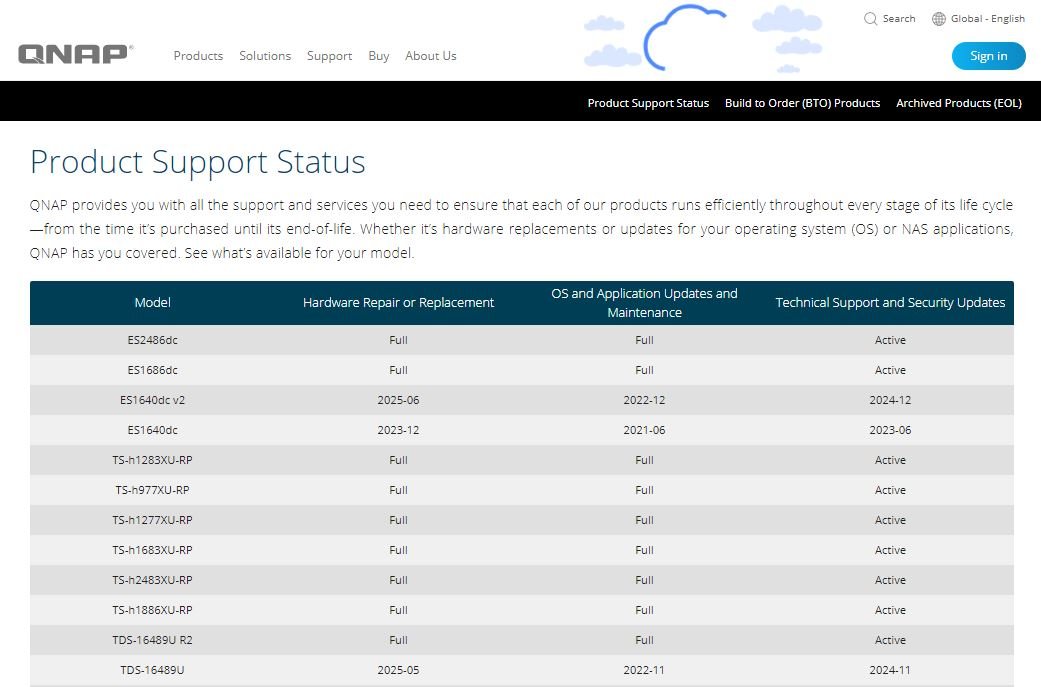
At the moment it was not specified which legacy NAS devices might be affected by these flaws: “There are many NAS hardware models that could be affected; you can find more information about models, repair periods and updates on our official sites. The report also mentions that for most models, the security update might reach the latest version (QTS 4.5.2), although some older hardware models have firmware update limits.
On the first flaw (CVE-2020-2509), experts report that this is a remote code execution error linked to the firmware of vulnerable devices: “Firmware versions prior to QTS 4.5.2.1566 and QTS 4.5.1.1495 are affected by the flaw, so users of these versions require updating their systems,” the experts mention.
If you are not able to upgrade at this time, experts report that it is possible to add an input disinfection stage in some central processes as a workaround, although it is best to install the updates.
On the other hand, CVE-2021-26195 is a remote code execution and arbitrary file write flaw that resides in the latest version of QNAP TS-231 firmware (4.3.6.1446).
Experts developed a proof of concept (PoC) to exploit the flaw in their research: “Using a Python script we managed to take full control of the device using the reverse shell technique; Afterwards, we managed to access a file stored on QNAP systems, which is available in a similar way to any other stored file.”
The report concludes by noting that the latest firmware version is now available for download, recommending users of affected versions to install as soon as possible: “This is a high severity flaw, so we are committed to releasing updates for legacy versions. This set of solutions should be available from next week.”
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
