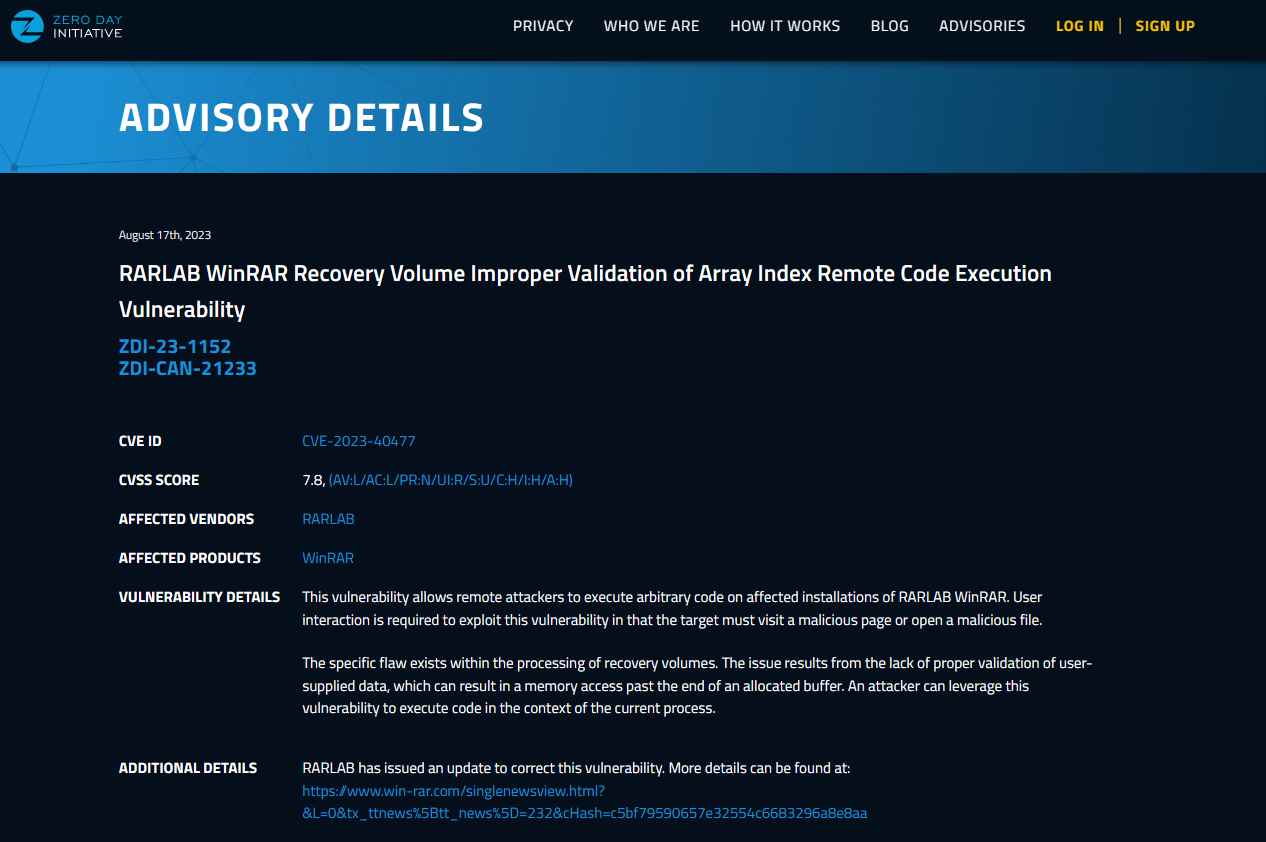
An arbitrary code execution vulnerability was found in WinRAR, and it is possible to exploit this issue by opening a RAR file that has been carefully prepared. According to the Zero Day Initiative, this vulnerability has been assigned the CVE identifier CVE-2023-40477, and the severity rating is 7.8 (High). The security researcher known as “goodbyeselene” brought this issue to the attention of WinRAR. It is an archive manager for the Windows Platform that is used by millions of people all around the globe.
WinRAR is capable of compressing and decompressing archive files in the following formats: AR, ZIP, CAB, ARJ, LZH, TAR, GZip, UUE, ISO, BZIP2, Z, and 7-Zip.
CVE-2023-40477 is a vulnerability that allows remote code execution.
This vulnerability arises as a consequence of faulty validation of user-supplied input, which may lead to accessing memory that occurs after the end of the buffer that has been created.This vulnerability may be exploited by an adversary by having them create a specially constructed file with the intention of using the currently running process as a means to execute arbitrary instructions on the system.
According to reports from ZDI, exploitation of this vulnerability needs some activity on the part of the user. The user has to either visit a malicious website or open a malicious file in order for this particular issue in the processing of recovery volumes to manifest itself.
In order to address this security flaw, WinRAR has issued a patch that is included in their most recent version, 6.23. They have also issued a security alert that discusses the new features and security updates. According to the information provided in the security advisory published by WinRAR, “a security issue involving out-of-bounds write is fixed in RAR4 recovery volumes processing code.”In addition to this, new features have been added, and WinRAR has also corrected another vulnerability that was found by Group-IB. This vulnerability was described as “a wrong file after a user double-clicked an item in a specially crafted archive,” and it was one of the vulnerabilities that was fixed.
Users of WinRAR are strongly encouraged to update to the most recent version in order to stop others from taking advantage of this vulnerability.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
