There have been efforts made to exploit CVE-2022-31678 and CVE-2021-39144 in the wild, as discovered by the Wallarm Detect team. The first vulnerabilities were discovered in VMware NSX Manager towards the tail end of the previous year. These vulnerabilities may result in remote code execution (RCE) if an authorized attacker exploits them. When paired with the CVE-2021-39144 vulnerability, which affects a third party library called XStream, this may lead to attacks with a large effect. The vulnerability was discovered in VMware NSX Manager and exposes software to XXE (XML External Entity Injection) attacks.
The software system known as VMware NSX Manager is used for the purposes of network virtualization and security. It offers a single administration platform for setting and monitoring the various security and virtualization components of a network. It is customary for organizations that utilize VMware NSX Manager to demand an exceptionally high degree of security for their network infrastructure. Businesses in the healthcare industry, retail and online commerce, traditional retail, and government institutions are all included in this category.
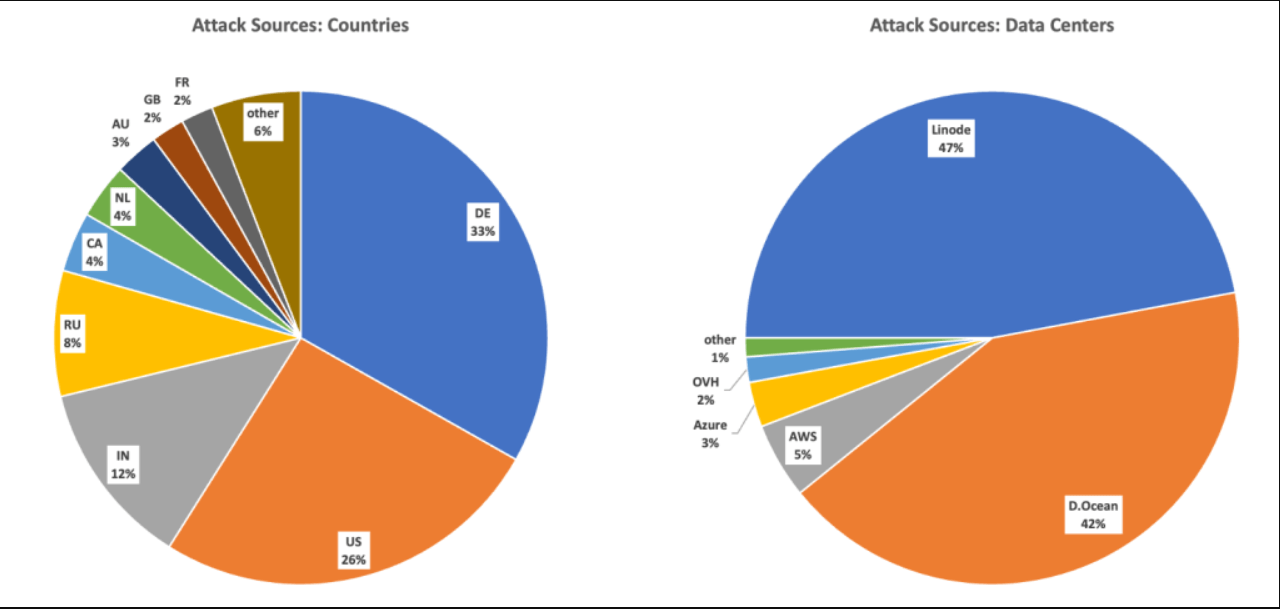
The CVE-2022-31678 vulnerability leaves software open to XXE attacks, but the CVE-2021-39144 vulnerability affects the XStream library that is provided by a third party. These vulnerabilities, when combined, might result in attacks with a significant effect. Over the course of the last two months, the Wallarm Detect team has logged over forty thousand attempts to take advantage of these vulnerabilities. More than ninety percent of these attacks have originated from well-known data centers such as Linode and Digital Ocean.
The CVE-2022-31678 issue, which is caused by poor processing of XML external entity declarations, makes it possible for an off-site attacker to get sensitive information. A remote attacker might exploit this issue to get sensitive information or trigger a situation that results in a denial of service by delivering material that has been carefully designed in XML.
The CVE-2021-39144 vulnerability, on the other hand, is caused by an unsafe deserialization error and enables an authorized remote attacker to execute arbitrary instructions on the system. This flaw allows for the vulnerability. An adversary might exploit this vulnerability to execute arbitrary instructions on the system by altering the processed input stream in some way.
In the event that these vulnerabilities are effectively exploited, the potential fallout might be very damaging. Attackers have the potential to steal data, seize control of the network infrastructure, and execute arbitrary code if they are successful. This is a significant risk that might put sensitive information at risk as well as violate individuals’ right to privacy.
The Wallarm Detect team saw that the highest number of scanning attempts occurred at the end of December, when Wallarm was thwarting an average of over 1,750 per day and a maximum of over 4,600 attacks per day. The pace, which is still about 500 tries per day, indicates that these vulnerabilities are still a risk.
Keeping their software up to date is one of the best ways for businesses to defend themselves against exploits and vulnerabilities of this kind. VMware has made patches available to fix these vulnerabilities, but according to their research, there are no additional solutions available.
In addition, it is strongly suggested that businesses put in place the appropriate security precautions, carry out routine security audits, and make use of API security solutions like Web Application Firewalls (WAFs) and vulnerability scanners.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
