Research presented during the Black Hat USA event indicates that some of the world’s leading technology companies could be exposed to severe cyberattacks due to errors in the implementation of the HTTP/2 specification. This investigation was presented by James Kettle of the security firm PortSwigger.
The researcher demonstrated that deploying desynchronization attacks against HTTP/2 systems would allow a threat actor to steal sensitive information from websites using Amazon Application Load Balancer, as well as poison all Bitbucket pages and force Atlassian to sign any user outside of Jira.
Given the protocol’s improvements, the cybersecurity community assumed that it was very complicated to deploy such an attack, at least until Kettle’s research: “Most HTTP/2 servers actually rewrite requests like HTTP/1 to communicate with the backend server, allowing for the smuggling of requests. This is a very common practice.”
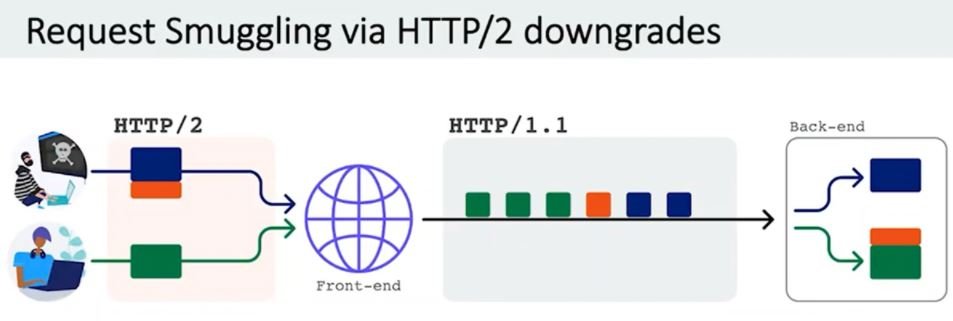
The attack scheme, described by Kettle as a “degradation of HTTP/2”, completely eliminates all the advantages that the use of HTTP/2 represents for administrators in terms of security.
The researcher presented his findings on Netflix, for which he earned a $20,000 USD reward as part of the streaming company’s rewards program: “Netflix used Netty’s Java library for HTTP/2 support, which stopped verifying that the length of the content was correct.
Successful exploitation of this vulnerability would allow threat actors to redirect users to malicious websites to run JavaScript on Netflix’s main website and even hijack accounts of affected users.
In a world where all systems employ HTTP/2, most of these request smuggling attacks would fail, although there is a long way to go. According to a recent report from W3techs, HTTP/2 currently supports only 46% of all websites, and it is not known how many of these perform behind-the-scenes degradations.
As part of its investigation, Kettle released an open source tool to help security teams test their own systems for HTTP/2 request smuggling flaws.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
