Information security specialists report the detection of a severe vulnerability in the TP-Link TL-WR840N EU routers. According to the report, successful exploitation of this flaw would allow threat actors to run shell commands on affected implementations.
Tracked as CVE-2022-29402, the vulnerability exists due to insecure protections for UART console, which would allow malicious hackers to run arbitrary OS commands after gaining physical access to vulnerable devices.
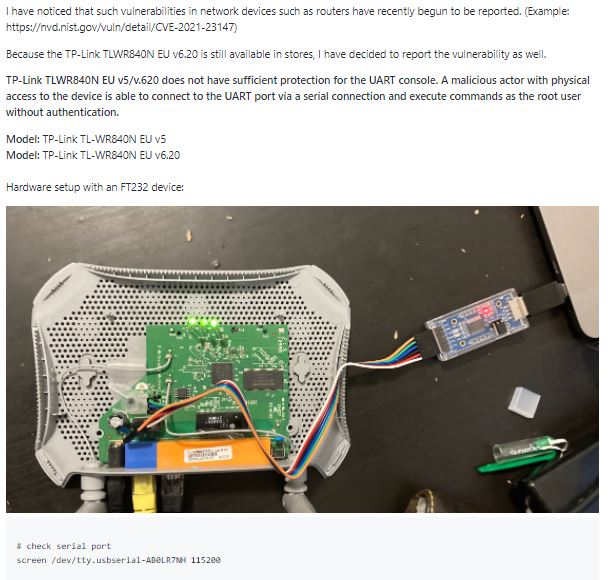
This is a low-severity vulnerability and received a 6.2/10 score as per the Common Vulnerability Scoring System (CVSS). As mentioned above, its successful exploitation may result in complete compromise of the target system.
The flaw resides in TP-Link TL-WR840N EU versions between v5 and v6.20.
Attackers must send specially crafted requests to exploit the vulnerability; however, the fact that the vulnerability requires physical access to affected devices greatly limits the potential for exploitation.
Even so, TP-Link reminds users of affected devices that there are still no patches to correct the error, so improving access policies to these devices is a recommended security measure while the corresponding patches are issued.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
