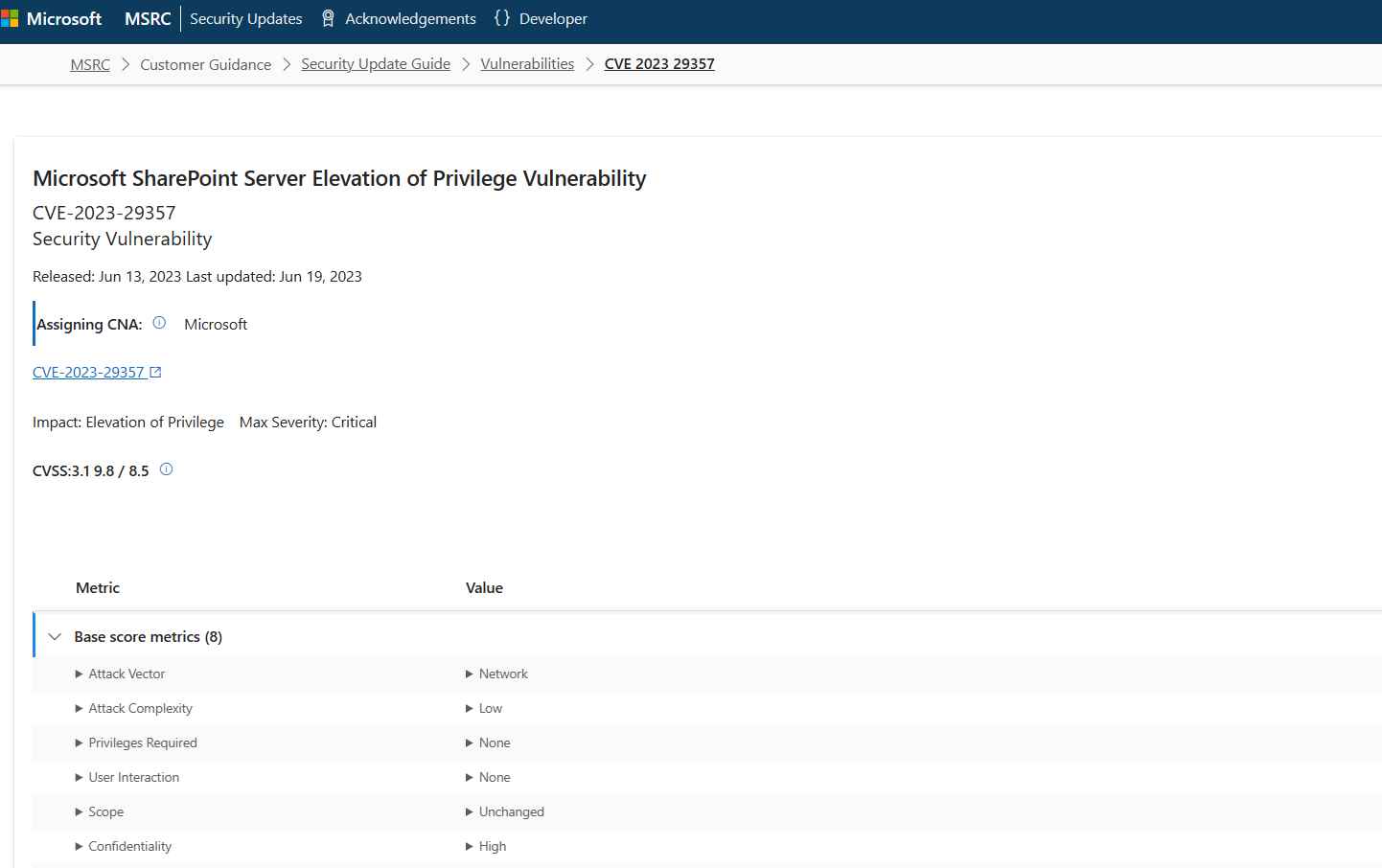
The proof-of-concept (PoC) attack code for a major vulnerability known as CVE-2023-29357 has been made public. This vulnerability allows users to get elevated privileges in Microsoft SharePoint Server products without first authenticating themselves. This vulnerability, which has an alarming CVSS score of 9.8, is not simply another ordinary fault; rather, it is a “critical” vulnerability that presents a significant danger to enterprises who are using Microsoft SharePoint. Why is it so important to point out that this issue exists? It gives malicious actors the opportunity to get elevated privileges on a system without requiring them to first authenticate themselves. Attackers might possibly obtain administrator credentials by just submitting a well prepared request. This provides the attackers with the golden key that allows them to enter the data vault of your firm.
The method of attack behind this vulnerability is detailed in an official warning issued by Microsoft. The text goes as follows: “An attacker who has gained access to spoofed JWT authentication tokens can use them to execute a network attack which bypasses authentication and allows them to gain access to the privileges of an authenticated user.”
This very much underscores the extreme threat that is presented by the vulnerability, since it allows attackers to function behind the façade of authorized users.
It is very important to express gratitude to the folks who are responsible for maintaining the safety of the digital domain. Jang (Nguyn Tin Giang), a member of StarLabs SG, is the savior in shining armor who discovered this vulnerability. On September 25th, Jang revealed all of the complex technical particulars of this vulnerability.
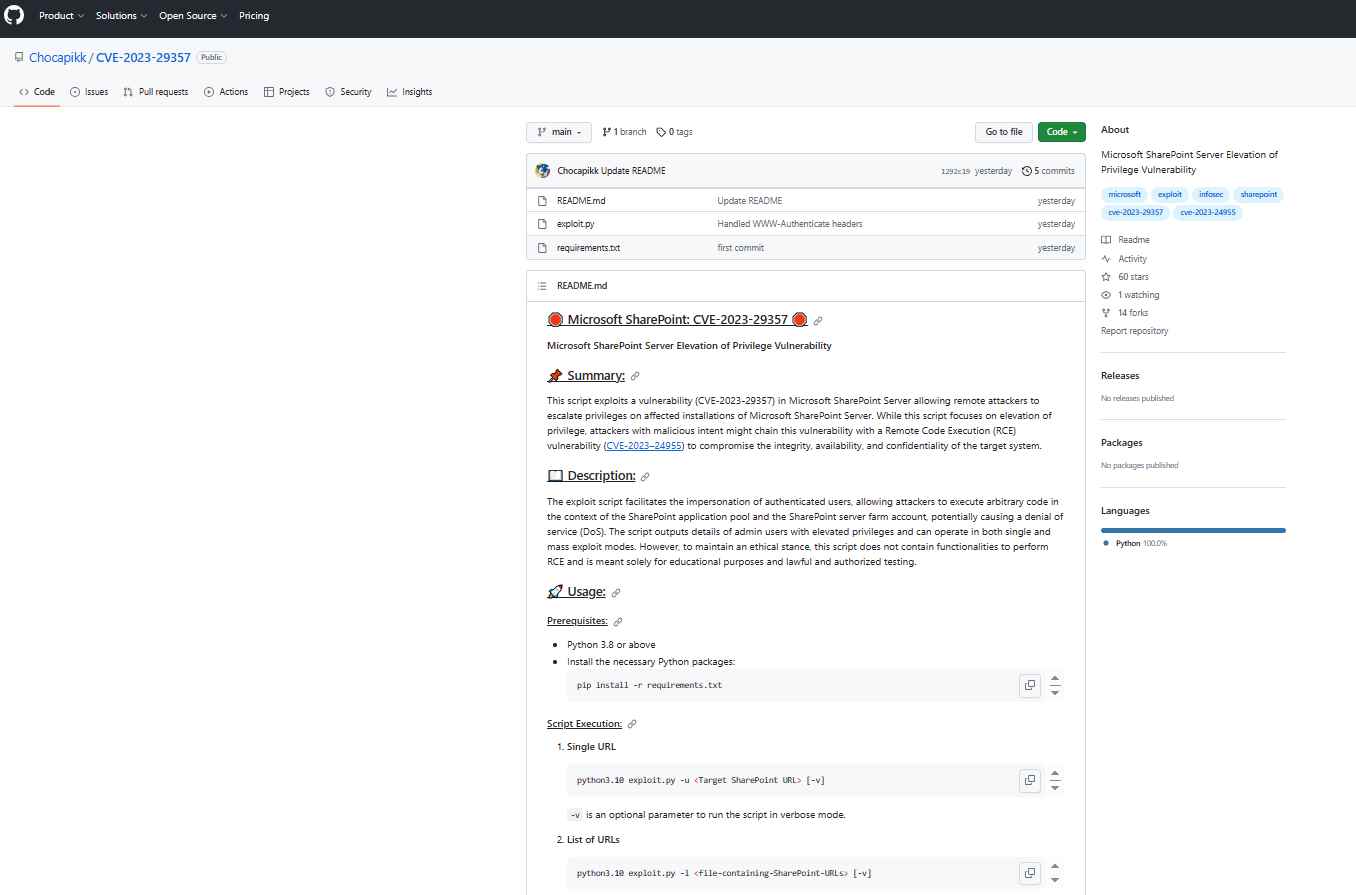
A well-known security researcher by the name of Chocapikk sent an urgent warning to all SharePoint administrators today, informing them that he has developed a proof-of-concept (PoC) attack for the CVE-2023-29357 vulnerability. This script is specifically geared at taking advantage of the vulnerability in Microsoft SharePoint Server that allows for the elevation of privilege. The possibility of combining this flaw with another vulnerability, known as the Remote Code Execution (RCE) CVE-2023–24955, is what makes the situation even more precarious. This lethal combination has the potential to completely destroy the three pillars of security, which are integrity, availability, and secrecy.
Particularly noteworthy about Chocapikk’s exploit script is that it enables the impersonation of authorized users, which has the potential to result in the execution of arbitrary code inside the SharePoint framework. Because of this, a full-fledged denial of service (DoS) attack may occur. However, it’s worth noting the script’s intended use. According to what Chocapikk says, “This script does not contain functionalities to perform RCE and is meant solely for educational purposes as well as lawful and authorized testing.”
The vulnerability has been recognized by Microsoft, and a fix has been made available. On the other hand, it is essential to keep in mind that potential attackers may already be aware of the vulnerability and may start using it even before a fix is made available. As a result, it is essential for users to take precautions in order to reduce the possibility of being exploited.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
