On Tuesday, the OpenSSL Project released a significant security update in order to address at least eight identified security weaknesses. These flaws leave OpenSSL users vulnerable to hostile hacker assaults.
Users of OpenSSL have also been made aware of the vulnerabilities CVE-2022-4304, CVE-2022-4203, CVE-2022-4450, CVE-2023-0216, CVE-2023-0217, and CVE-2023-0401. These are six vulnerabilities of moderate severity that can be exploited for denial-of-service attacks (DoS) and possibly for the disclosure of private memory contents, such as private keys.

The availability of OpenSSL 3.0, 1.1.1, and 1.0.2, each of which fixes a high-severity vulnerability that might enable an attacker to access the contents of memory or conduct denial-of-service attacks.
The vulnerability, which has been assigned the tracking number CVE-2023-0286, is known as a type misunderstanding in X.509 GeneralName. A type misunderstanding issue exists in X.509 GeneralName processing when an X.400 address is being processed inside the GeneralName. However, the public structure definition for GENERAL NAME mistakenly listed the type of the x400Address field as ASN1 TYPE, therefore X.400 addresses were processed as an ASN1 STRING. Following that, the OpenSSL function GENERAL NAME cmp will treat this field not as an ASN1 STRING but rather as an ASN1 TYPE.
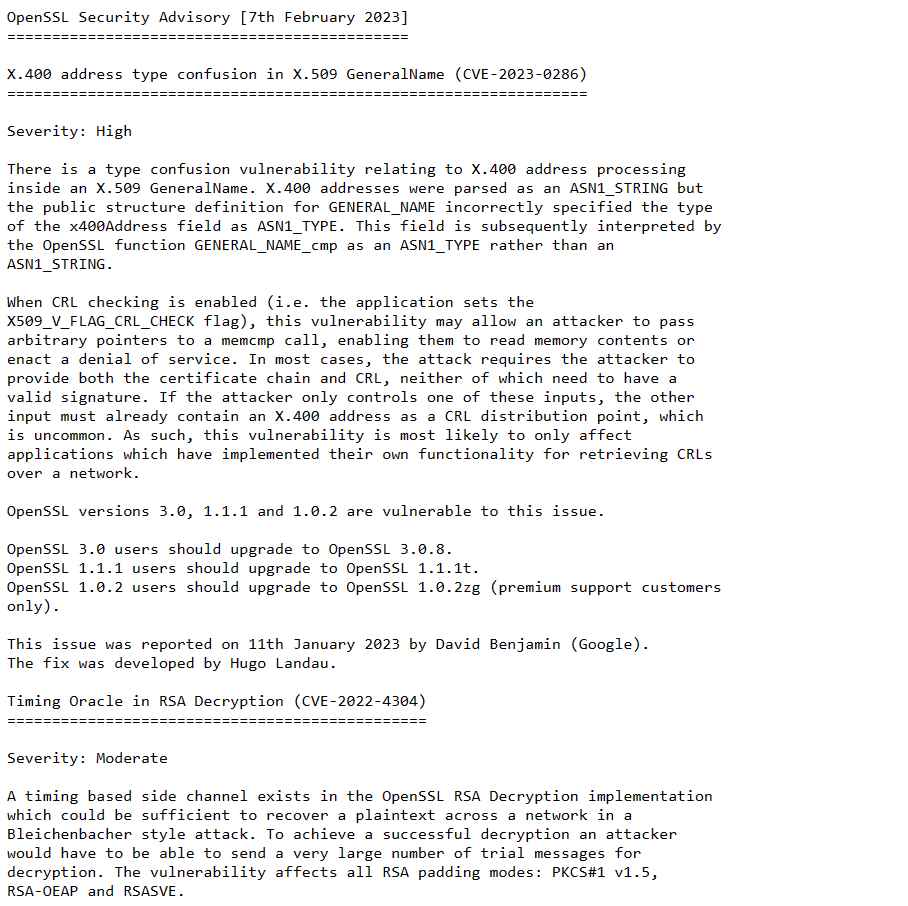
This vulnerability may allow an attacker to supply arbitrary pointers to a memcmp call when CRL checking is enabled (i.e. when the application sets the X509 V FLAG CRL CHECK flag). This gives the attacker the potential to access memory contents or cause a denial of service.
Organizations running OpenSSL versions 3.0, 1.1.1 and 1.0.2 are urged to apply available upgrades immediately.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
