Cybersecurity specialists developed a code for the exploitation of CVE-2022-24086, a dangerous vulnerability in AdobeCommerce and Magento Open Source. Adobe security teams reported that some isolated cases of exploitation of this flaw have been detected, which would allow the deployment of remote code execution (RCE) attacks.
Just a couple of days ago, Adobe issued a security update, modifying the tracking key for this flaw and specifying that it was assigned a score of 9.8/10 according to the Common Vulnerability Scoring System (CVSS).
Shortly after the publication of this alert, researchers at Positive Technologies announced the creation of a functional exploit for this vulnerability.
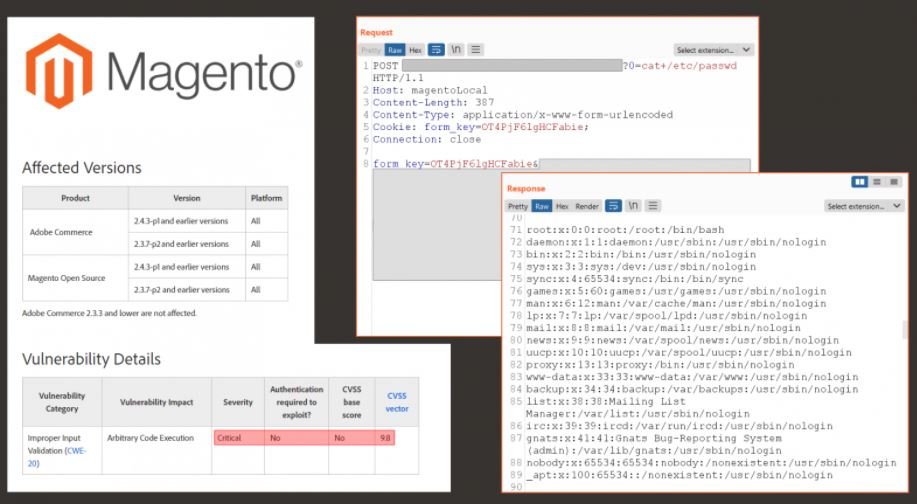
The researchers mention that threat actors can exploit the flaw to gain full access to the target system with web server privileges, further ensuring that enabling a web application firewall (WAF) does not mitigate the risk of exploitation because there are multiple attack vectors.
The main target in a potential exploitation campaign would be e-commerce websites, as threat actors could take advantage of this bug to extract sensitive information, including payment card details. Positive Technologies estimates that there could currently be as many as 17,000 websites vulnerable to exploitation of this flaw, including online stores owned by large companies.
The good news is that the exploit code will not be published for the time being due to the latent security risk, as thousands of AdobeCommerce and Magento implementations will continue to operate without the necessary security measures. Still, they recommend that administrators of affected instances check the availability of update patches.
Although the researchers consider that the development of a similar exploit could be a highly complex task, they recommend not underestimating hacking groups and trying to mitigate the risk of exploitation, since it is not impossible to think of a group of attackers capable of developing another exploit.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
