For web hosting and data center providers, Plesk is a very well-liked administrative tool. The web interface is typically used by users to manage their file servers and websites. This interface has undergone extensive testing and has been fixed for security flaws.
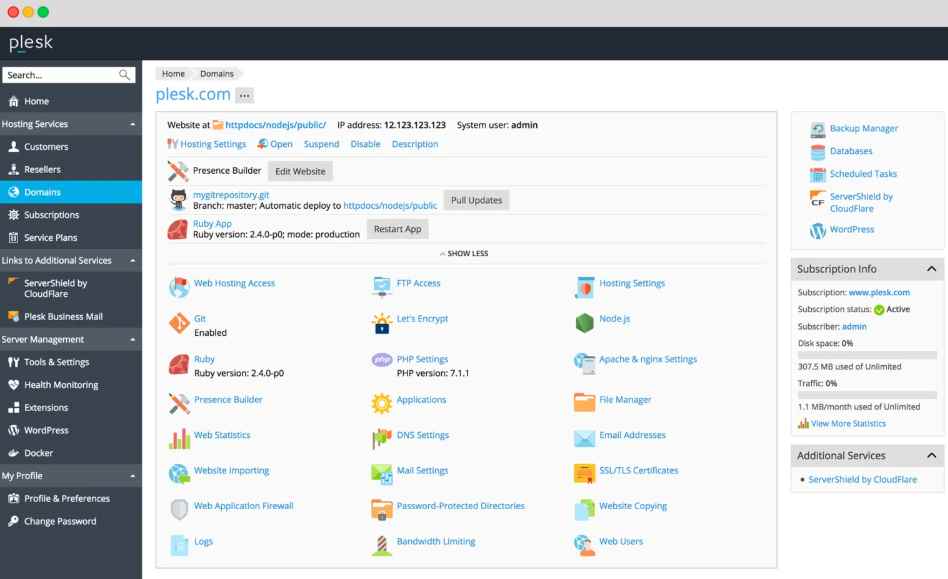
The REST API, which gives other applications access to Plesk’s capabilities, is not as secure as its online user interface equivalent, according to Adrian Tiron’s findings, a security expert at Fortbridge.
He found that there are no CSRF protections when an administrator is signed in and calling the REST API from their browser. Due to this flaw, an attacker might launch cookieless CSRF attacks against the server if they managed to convince the Plesk admin to visit a malicious website. The cookieless CSRF vulnerability might be used to target several API endpoints. The endpoint that permitted various instructions, including altering the administrator’s password, was the most intriguing, according to Tiron. The researcher successfully took over the admin user account and took complete control of the host by using this URL.
The Authorization header is used by Plesk’s web interface to guard against unauthorized access to the management tool’s pages.
The browser automatically adds the necessary headers to requests after a user inputs their credentials, allowing the server to identify between authorized users.
Additionally, authorization headers stopped arbitrary, untrusted access to the REST API endpoints. But HTML-based CSRF attacks have the ability to get around all of this.
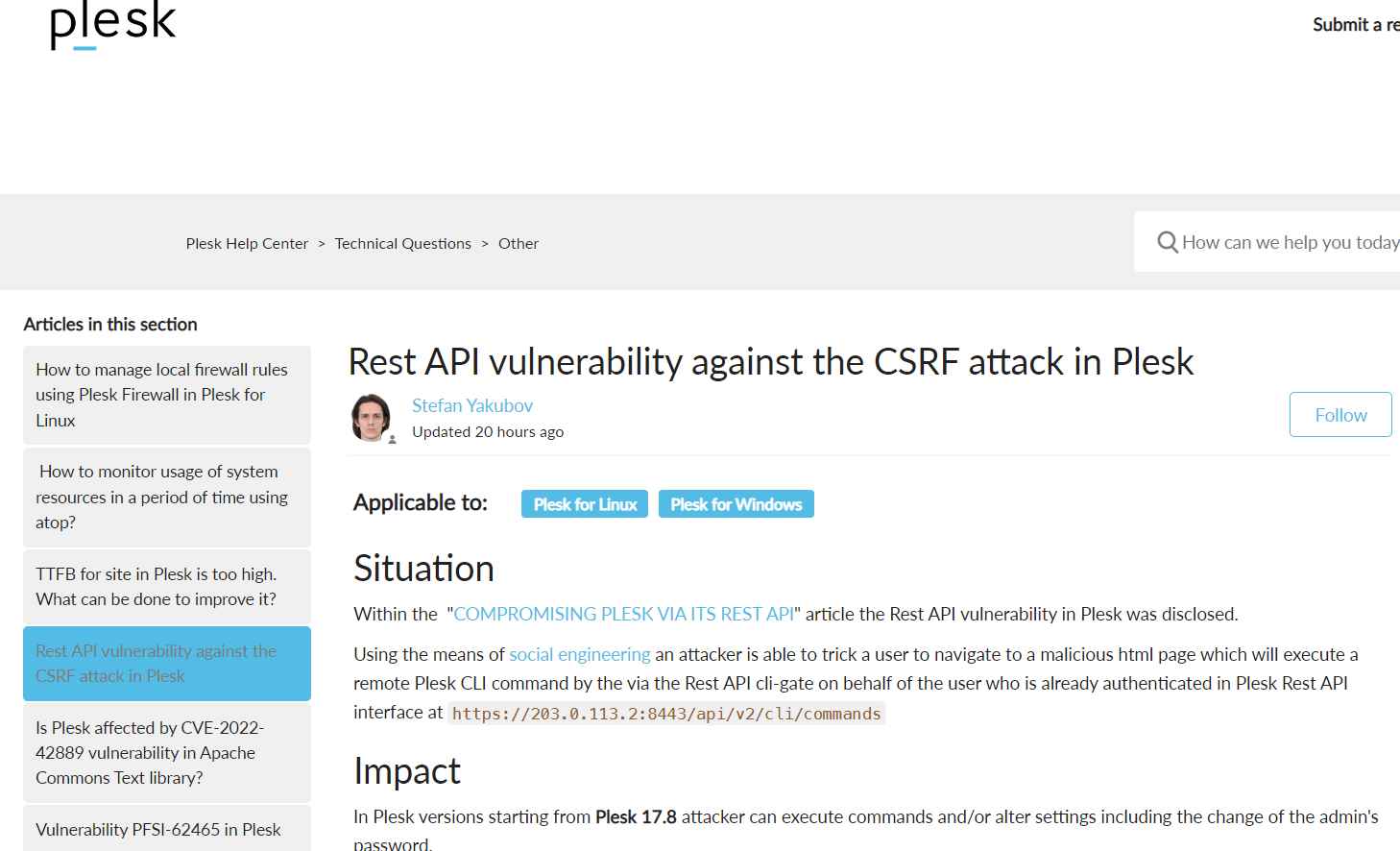
Impact
Beginning with Plesk 17.8, an attacker can run commands and/or change settings, including changing the admin password.
98.4% of the Plesk servers immediately updated the addon and were unaffected.
The following fixes were delivered:
on July 5, 2022, for Plesk versions 18.0.26 and beyond
late September 26, 2022 for Plesk versions 17.8.10 to 18.0.25.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
