SAP security teams have revealed the finding of at least 15 vulnerabilities discovered in some of their products. The company recommends that customers verify the presence of these flaws and update their products if necessary.
These vulnerabilities were detected and reported between March and August 2020.
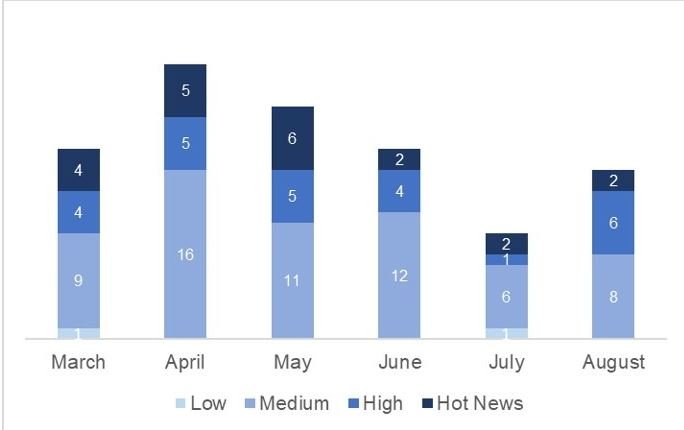
Below is a brief summary of the reported flaws, in addition to their identification keys according to the Common Vulnerability Scoring System (CVSS).
- CVE-2020-6287: Multiple flaws in SAP NetWeaver AS JAVA (LM Configuration Wizard)
- CVE-2020-6284: Cross-Site script vulnerability (XSS) in SAP Netweaver
- CVE-2020-6294: No authentication verification on SAP BusinessObjects Business Intelligence platform
- CVE-2020-6298: Missing authorization check in SAP Banking Services
- CVE-2020-6296: Code injection vulnerability in SAP NetWeaver and the ABAP platform
- CVE-2020-6309: No authentication verification in SAP NetWeaver AS JAVA
- CVE-2020-6293: No file upload controls on SAP NetWeaver
- CVE-2020-6295: Information disclosure vulnerability in SAP Adaptive Server Enterprise
- CVE-2020-6297: Information disclosure vulnerability in SAP Data Intelligence
- CVE-2020-11022, CVE-2020-11023: Cross-Site scripting vulnerabilities (XSS) in jQuery, included with SAPUI5
- CVE-2020-9281, CVE-2019-11358: Two vulnerabilities in open source libraries used in SAP Commerce
- CVE-2020-6301: No authorization check in SAP ERP
- CVE-2020-6300: Cross-Site scripting vulnerability (XSS) on SAP Business Objects Business Intelligence Platform
- CVE-2020-6273: No authorization check in SAP S/4 HANA
- CVE-2020-6299: Information disclosure vulnerability in SAP NetWeaver and the ABAP Platform
- CVE-2020-6310: Information disclosure flaw in SAP NetWeaver and ABAP platform
As can be seen, most of these flaws relate to cross-site scripting (XSS) attacks and sensitive information exposure. The most severe of these vulnerabilities (CVE-2020-6287) received a CVSS score of 10/10, so it is considered a critical flaw. The next 7 flaws received scores between 9/10 and 8/10. The score for the rest of the reports ranges from 3/10 to 4/10.
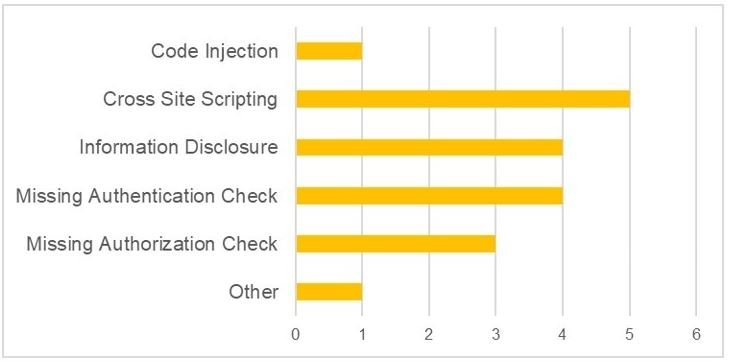
Customers who want to learn more about reported flaws can view the full report on SAP’s official platforms. Updates should be installed as soon as possible to fully mitigate any attempts to exploit.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
