Chris Williams, an independent cybersecurity specialist, recently published a report detailing the method he used to successfully exploit the flaw identified as CVE-2020-6418 residing in the Chromium-based web browser included in Tesla Model 3 cars.
In late 2019 and after purchasing his own Tesla Model 3, Williams began to learn about safety in automotive applications, tracking safety updates and patches for the V8 engine. It was not until February 2020 that he began publishing his astonishing findings on the safety of this advanced vehicle.
Williams notes that the problem is related to a patch-gapping condition, which occurs when threat actors can exploit known vulnerabilities in the period that developers delay in releasing security patches to the general public: “After Tesla released its 2020.4.1 software version, its implementation of Chromium operated with version 79.0.3945.88, which had not been corrected, which makes it highly likely that the browser used at that time was vulnerable,” the expert notes.
To determine the scope of the vulnerability, Williams used the debugged version of the JavaScript engine, which allowed him to identify the V8 project commits for the Chromium version of interest by entering the version number in the desired OmahaProxy console window: “First we need to configure the development environment and build V8 on this commitment. The repository depot_tools contains everything you need to build Chromium and all its components into a standard virtual machine on amd64 Ubuntu 18.04.”
Williams then took about 30 minutes to build the d8 in debug mode on a MacBook Pro computer to launch a primary version of a known exploit, modifying it to run on d8 and not on a web browser, but without getting the desired results.
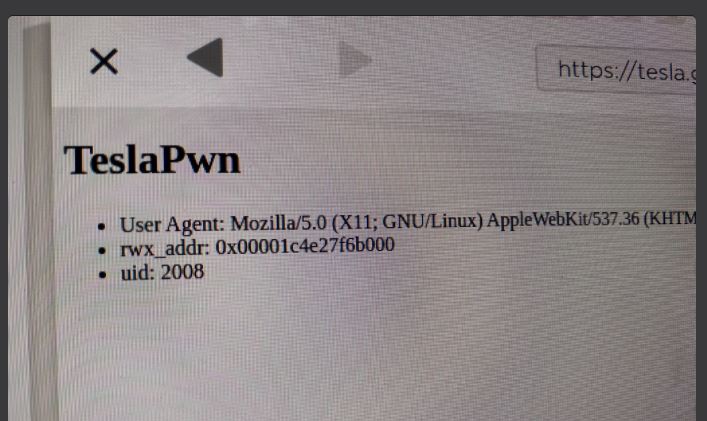
Williams used git bisect to find out the reason for his flaw and implemented addrof on March 6. After implementing fakeobj he obtained privileges to read and write data, and a day later, the researcher was able to run the shell code and understand that it was a sandbox.
After receiving the security report, Tesla fixed the vulnerability in early April 2021. To learn more about information security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security websites (IICS).
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
