Chipmaker NVIDIA announced the fix of some security flaws that could impact millions of Internet of Things (IoT) devices running Jetson chips. According to the report, exploiting these flaws would allow the deployment of denial of service (DoS) attacks or the interception of sensitive data.
The company released updates for a total of 9 critical security flaws, in addition to fixing eight low-severity flaws. These patches will address all sorts of flaws in NVIDIA’s most popular developments, usually employed in embedded computing systems, machine learning systems, and autonomous devices.
Affected products include the Jetson family of chips, AGX Xavier, Xavier NX/TX1, Jetson TX2, and Jetson Nano devices, which reside in the NVIDIA JetPack software development kit. The patches were delivered as part of NVIDIA’s latest security update.
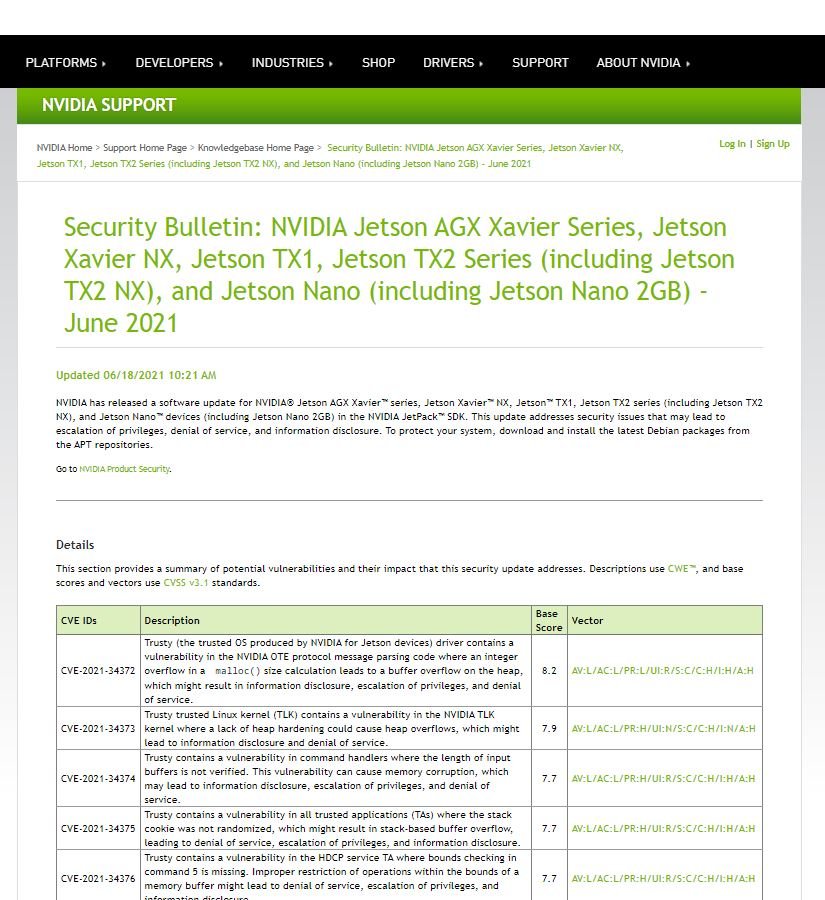
Of all the flaws reported, the most critical was tracked as CVE-2021-31372 and would allow threat actors to deploy a buffer overflow on affected systems. The company’s report added that hackers would require access to a system’s network to carry out the attack, although deploying the attack is relatively easy. The flaw has not received a score according to the Common Vulnerability Scoring System (CVSS).
A successful attack would allow threat actors to gain persistent access to vulnerable components, as well as allowing hackers to manipulate or disable affected devices. The security report goes on to mention that “the Jetson driver contains a flaw in the message parsing code of the NVIDIA OTE protocol, where an integer overflow leads to buffer overflow, leading to privilege escalation and denial of service (DoS) scenarios.”
Another of the severe flaws that were corrected affects Jetson’s trusted Linux kernel and allows heap-based buffer overflow attacks. This type of attack targets the chip heap’s data memory frame, where the component is manipulated to generate risk scenarios.
NVIDIA concluded its report by recalling that the flaws could lead to DoS conditions, privilege escalations, and leaking of sensitive information, so it’s recommended to install updates as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
