After a researcher detected a specially crafted Word file to run arbitrary PowerShell on Windows systems, Microsoft confirmed that its operating system is affected by a zero-day vulnerability tracked as CVE-2022-30190, quite possibly exploited in the wild.
The malicious document was published on VirusTotal from Belarus and, so far, does not appear to have been detected in many active exploitation attempts.
The expert Kevin Beaumont was one of the first to analyze this exploit, dubbing it as Follina because the malicious file detected refers to 0438, the code area of a small Italian city. Microsoft confirmed that they received a flaw report by security researcher known as “CrazymanArmy” in April.
While Microsoft initially classified this report as “not a security-related issue,” active exploitation attempts were already known. In addition, although Microsoft responded to the report assuring that the flaw would be corrected, no patch has been issued related to this problem.
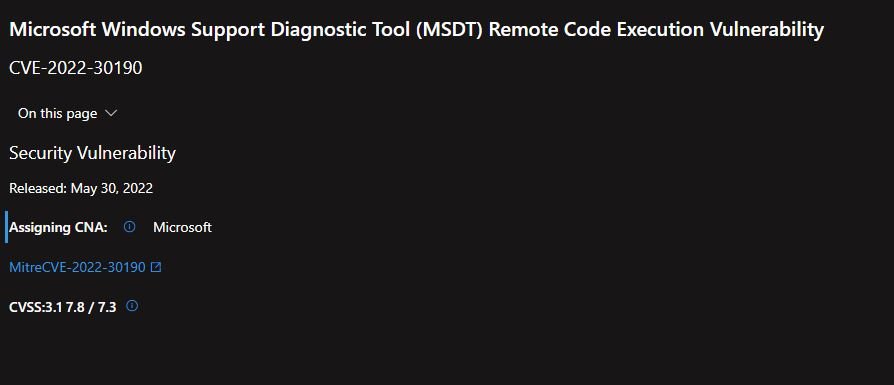
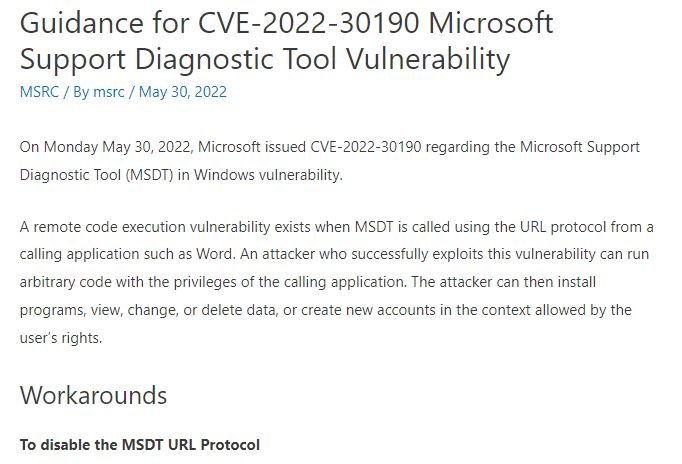
According to Microsoft’s report, Follina resides in its Support Diagnostic Tool (MSDT), which collects information to send to the company’s support area: “An attacker could execute arbitrary code with MSDT privileges to install programs, view, change and modify data, and even create new accounts on the affected system.” This is an unusual attack variant, as it seems not to rely on the use of macros like other attacks using Microsoft Office files.
On the attempts at active exploitation, a report by NCC Group notes that some attacks for extortion purposes have been detected, while Beaumont mentioned having detected an attempted attack against users in Russia using as a decoy an alleged job interview with Sputnik Radio.
The attack attempts so far detected have targeted Deployments of Office Pro Plus, Office 2013, Office 2016, Office 2019, and Office 2021.
Microsoft released security guidance, including some workarounds and information about new Microsoft Defender updates, designed to detect and block files and behaviors associated with the threat.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
