GitHub has fixed a flaw that might have allowed hackers to take over one of its repositories and possibly infect all the software and other programs that depended on it.
On June 13, investigators from the security firm Checkmarx contacted the platform. GitHub confirmed the problem, rated it as “high” severity, and gave the researchers an unknown bug bounty. Checkmarx researchers noted in their paper on the problem that malicious actors may take advantage of it by “Repojacking” genuine, frequently-used namespaces on GitHub.
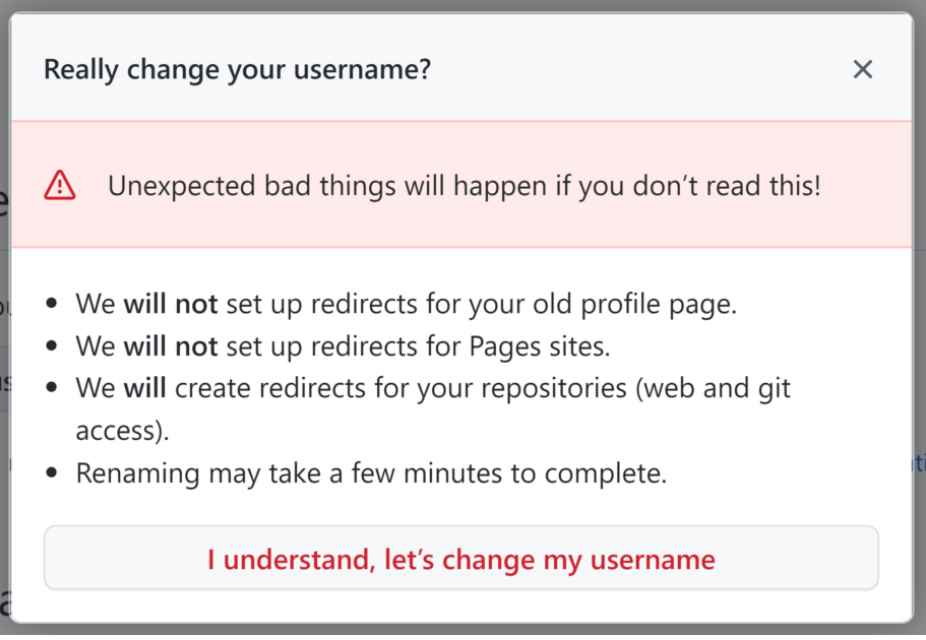
The username and repository name are typically combined to form the namespace on GitHub. Example-user/example-repo is one instance. According to the researchers, “A namespace is subject to Repojacking in case the original name of the user was changed utilizing the ‘user rename’ option GitHub provides. “Changing your username is an easy and quick process. You are informed in advance that all traffic to the old repository’s URL will be sent to the new one.
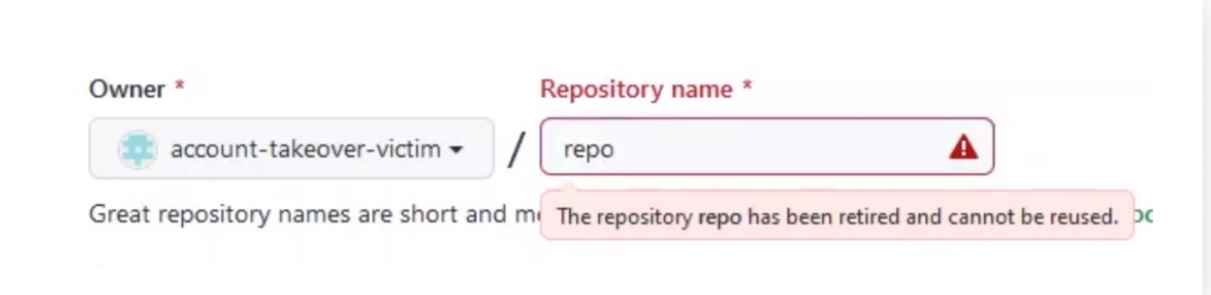
As soon as you change your username, anyone can use the previous one. The namespace can be taken over by an attacker by opening a repository with the same name.
To solve the problem, GitHub developed a feature that prevents other users from using any repository that fulfills a set of requirements. GitHub users should refrain from utilizing retired namespaces even after the problem has been resolved because “additional vulnerabilities in this approach may still exist,” according to experts.
The protection offered by the platform to remedy the issue, according to their report on the flaw, “is enabled based on internal metrics and offers the users no indication if a particular namespace is protected by it or not,” despite their collaboration with the firm on the matter.
According to the researchers, this may unwittingly put some repositories and packages at danger.
As a result of the vulnerability’s significance and the fact that hundreds of programs rely on open source libraries and code repositories, which makes attacks on them potentially disastrous, other cybersecurity experts concurred with this.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
