A cybersecurity expert published a report that chronicles, in broad detail, how he managed to hack the systems of renowned technology companies such as Apple, Microsoft or PayPal using a sophisticated software supply chain attack. Alex Birsan, a vulnerability bounty hunter, says he managed to complete this attack by exploiting a flaw he identified as dependency confusion.
The concept of dependency confusion refers to vulnerabilities that allow threat actors to deploy and run malware on an organization’s networks by overriding private use dependency packages using malicious public packages labeled with the same name. There are few organizations that use public and private dependencies in their source code, so these attacks are highly feasible.
The expert mentions that this idea came to mind when analyzing a Node.js file designed for internal use in PayPal. A later detailed analysis revealed that some of the private package names did not exist in the NPM public registry: “What happens if malicious code is loaded into NPM using the same name as a legitimate file? Is it possible that some of the projects in these companies use them by default without first checking if everything is in order?”, Birsan thought.
To solve his approach, Birsan uploaded malicious code to public NPM dependency records using private package names available on GitHub, hosting sites, and online forums. During this process, the expert discovered that if a dependency package includes the same name in public and private repositories, the system will favor the use of the public version.
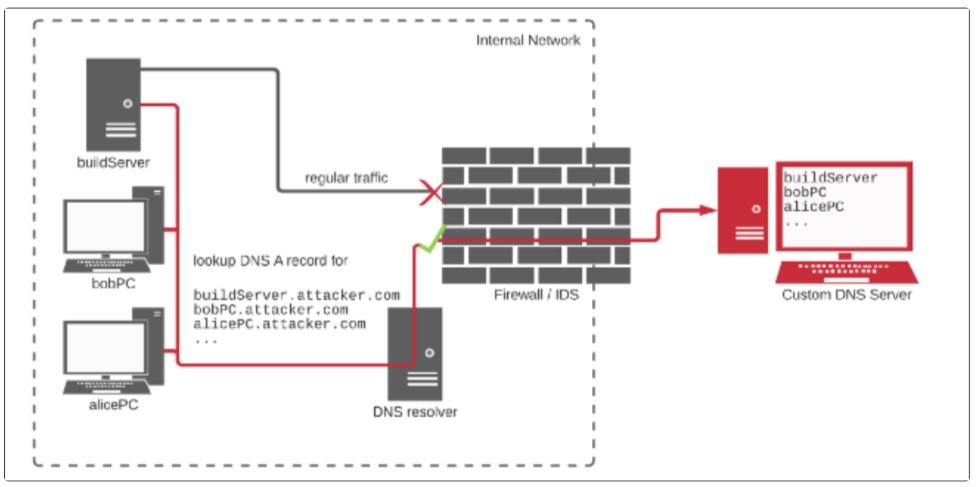
The expert mentions that this attack requires no interaction from the victims to succeed, as it only requires automatically replacing private packages with audiences: “NPM allows arbitrary code to run automatically when installing the package, allowing me to easily create a Node package that collects basic information about each machine on which it is installed through its preinstallation script”. The Expert Advisor then sent the information to itself using a DNS extraction technique to prevent security mechanisms from detecting malicious activity.
In his report, Birsen mentions that the flaw was successfully exploited in the systems of the aforementioned companies, as well as affecting other companies such as Shopify, Netflix, Tesla and Uber, accumulating rewards of more than $130,000 USD.
This issue was reported to companies, which rushed to fix the vulnerabilities. Microsoft issued a security alert to ensure that all private packages are restricted in public sources. The company awarded the investigator a $40,000 USD reward for his report.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
