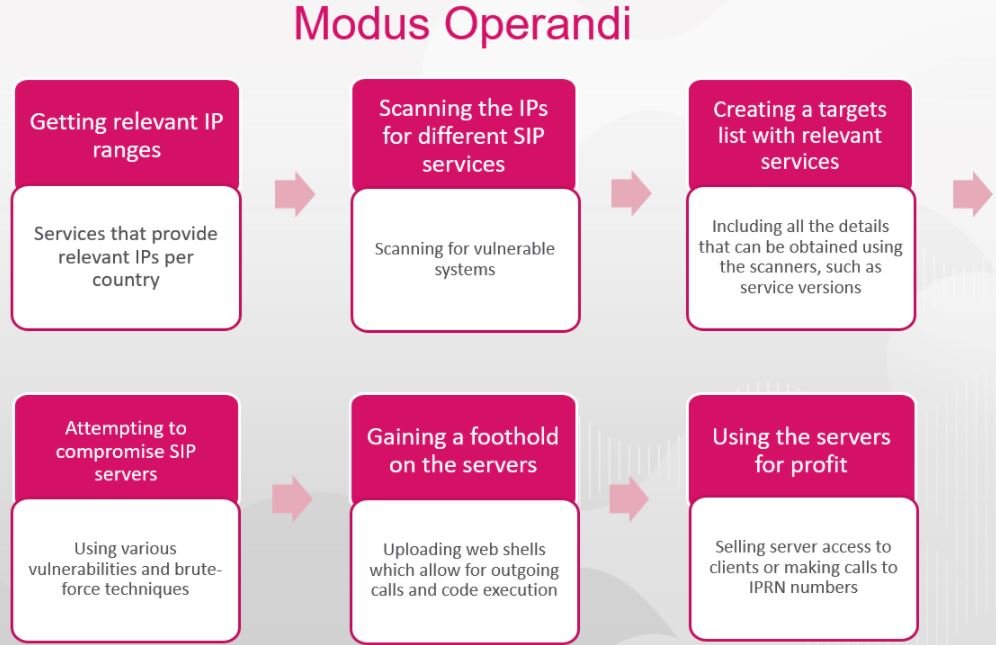
A hacking campaign has compromised voice over Internet protocol (VoIP) phone systems used in more than 1,000 companies around the world in order to make illicit profits from the sale of compromised accounts.
In addition to trading VoIP fraud, threat actors could also be operating espionage campaigns, cryptocurrency mining and even the use of affected systems as an entry point for the deployment of subsequent attacks.
According to Check Point specialists, a hacking group has compromised the VoIP networks of nearly 1200 organizations in more than 20 countries by exploiting a dangerous vulnerability, accumulating more than 500 victims in the UK alone. Experts believe industries such as government, army, insurance, finance and manufacturing have been victims of the campaign. Other countries where similar attacks have been detected include Belgium, the United States, Colombia, the Netherlands and Germany.
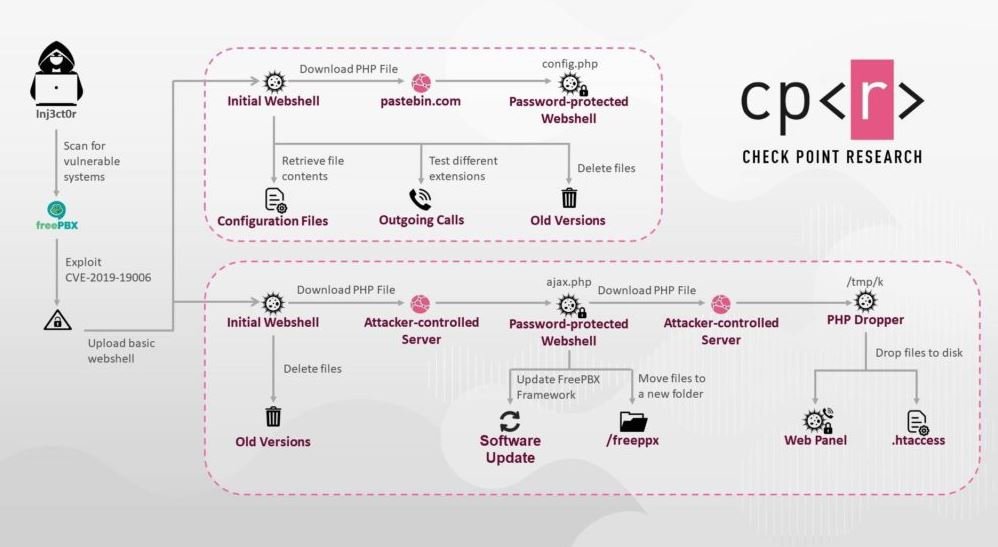
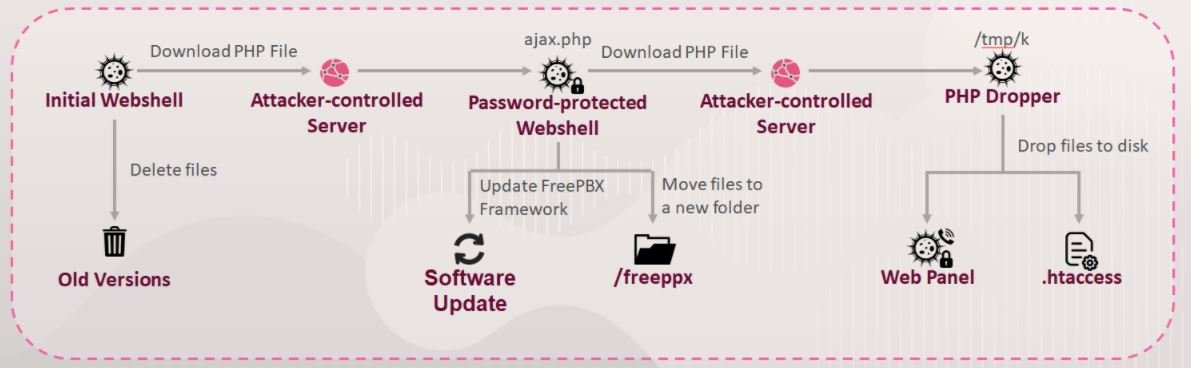
This attack exploits the CVE-2019-19006 vulnerability, a critical failure in the Sangoma and Asterisk VoIP systems, allowing external users to access remotely without authentication. A security patch was released a few months ago to fix this vulnerability, but many organizations have not yet installed it, exposing them to threat actors.
One of the most common means of exploiting these systems is to make outgoing calls without the VoIP system being able to log this action, allowing threat actors to secretly dial the configured premium rate numbers in order to generate money at the expense of the affected organizations.
Threat actors also generate profits by selling access to these systems on the black market, which could expose victims to all kinds of attacks: “These criminals are likely to expose organizations to other attacks by selling their compromised information on hacking forums,” the security report adds.
It is recommended that potentially affected organizations change their default usernames and passwords on VoIP devices in order to prevent them from being easily compromised. In addition, if possible, system administrators should establish VoIP security controls to identify any anomalous behavior in their deployments.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
