The Tor browser has become one of the most used tools by users concerned about government surveillance and their privacy. However, like other technological developments, this tool is affected by severe security flaws.
Tor uses 3 different nodes or ‘relays’ to handle any communication produced to hide the actual source of traffic; the latter is an output node that has access to information about where the data is actually directed, although sometimes this output node can act maliciously.
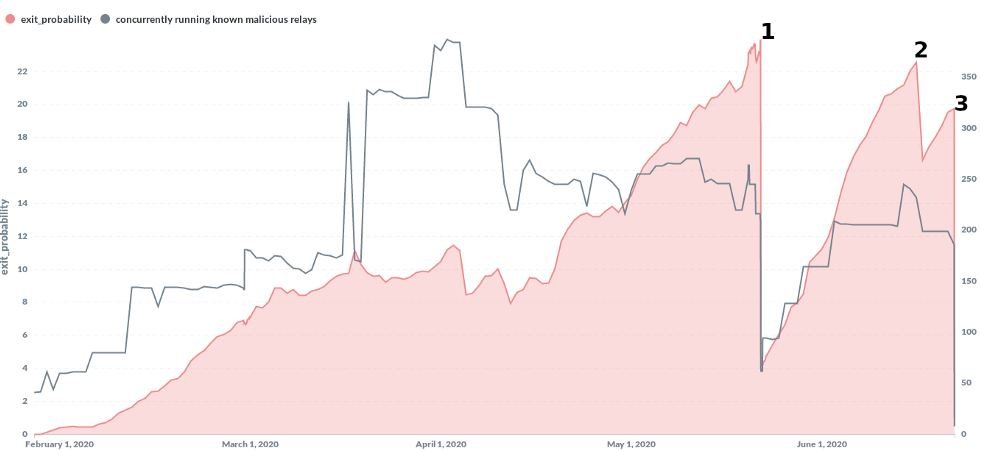
An investigator has released a report describing malicious behavior on a Tor node, which could be controlled by threat actors to deploy all kinds of attacks against anonymous network users.
Specifically, the researcher refers to a malicious hacker who was able to access data transmitted by a user in an unencrypted form, allowing him to alter the information that passed through the private network. Apparently, the attacker’s main goal was to modify exposed Bitcoin addresses and replace them with their own, stealing the transferred virtual assets.
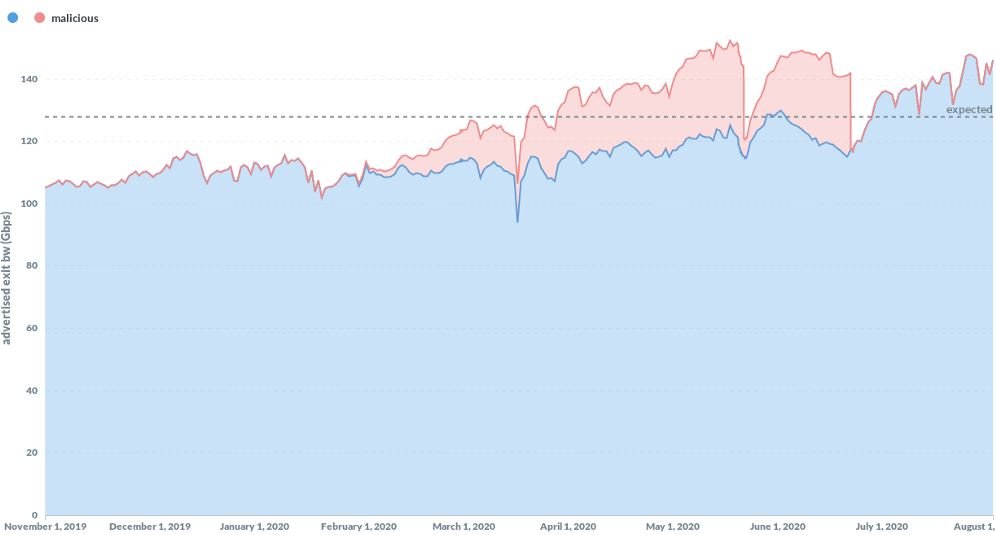
In the report, the researcher explains that: “threat actors deploy Man-in-The-Middle (MiTM) attacks against Tor users by manipulating traffic as it flows through the output nodes.” It appears that hackers remove HTTP redirects to HTTPS to gain full access to unencrypted HTTP traffic without generating TLS certificate warnings.
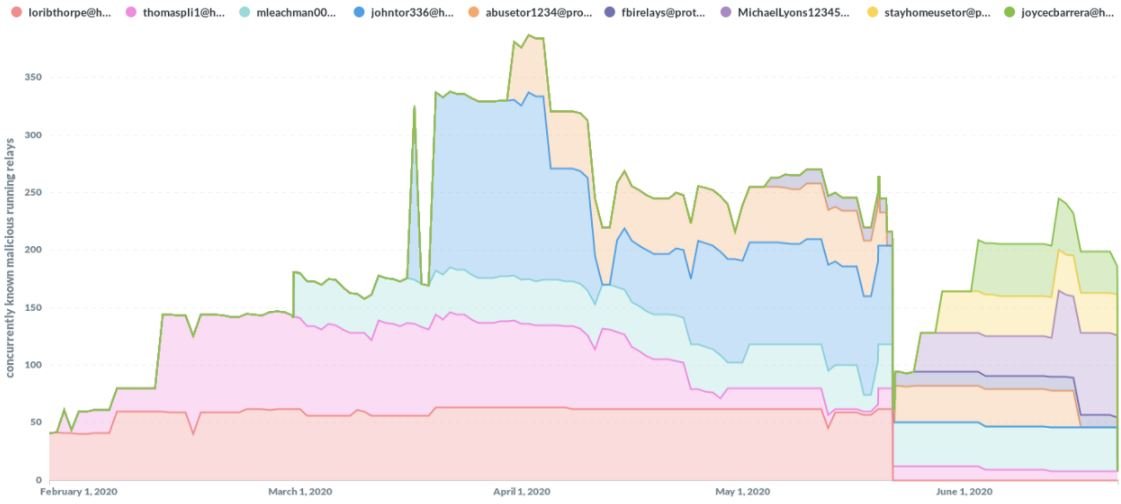
Browser developers were notified about these attacks, so a considerable portion of the malicious nodes have already been removed. However, it should be mentioned that about 10% of malicious nodes are still active, so developers will need to continue working to eliminate potential security risks.
This report took many by surprise, as the attacks significantly compromised the privacy offered by the platform, so users and developers are already thinking about the best ways to fix these flaws and prevent similar incidents in the future.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
