Every day, tons of new security flaws are discovered in multiple technology implementations, although sometimes these findings are found for the dozens of times. Using a new tool specifically designed for security testing on USB drivers, a group of cybersecurity specialists discovered 26 new security flaws present in various operating systems.
Researchers Hui Peng and Mathias Payer described their finding in a recently published document: “The tool, called USBFuzz, discovered 26 new flaws, including 16 memory errors considered serious for some Linux subsystems (USB core, USB sound, and network), one fault in FreeBSD, three on macOS, four on Windows systems, and one linux USB host driver security flaw.”
While 11 of the vulnerabilities found have already been fixed, the rest of the bugs still need to be addressed by the developers.
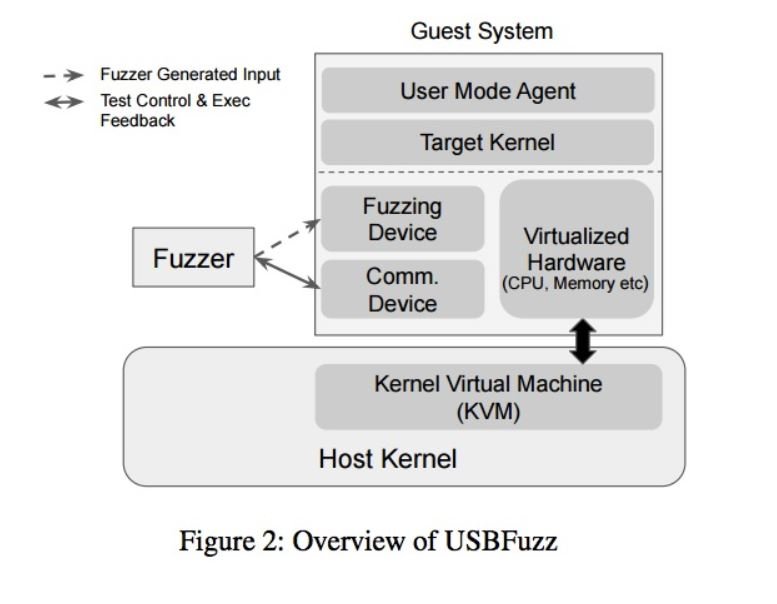
USBFuzz is a modular security testing framework that can be connected to a USB controller on different cores of an operating system. Researchers plan to make USBFuzz an open source tool available on GitHub in the short term.
The implementation of this type of tests (known as fuzzing) require the entry of invalid, unsolicited and random data into the scanned software (in this case, USB drivers), allowing to analyze its behavior and detect possible collapses, memory leaks, among other exploitable scenarios for malicious purposes.
“This is a challenging process due to the difficulty of providing random information to devices. Dedicated programmable hardware devices are expensive and inaccurate, and automating a fuzzing test is highly complex,” the researchers say.
The intention of the researchers was to make the fuzing device cost-effective, hardware-independent and capable of operating on different operating systems and platforms: “In essence, USBFuzz uses a software-emulated USB device to provide random device data to drivers (when performing IoT operations). Because the emulated USB device works at the device level, porting it to other platforms is simple.”
USBFuzz works on Linux, FreeBSD, macOS, and Windows, and can be used for silly fuzzing, focused fuzzing, and coverage-guided fuzzing (where coverage collection is supported).
Alternative solutions are currently not known to mitigate the risk of exploiting these security flaws, so affected deployment administrators should remain aware of the release of required updates.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
