Hacking groups keep playing a key role in the conflict between Ukraine and Russia almost a month after the start of the military invasion ordered by the government of Vladimir Putin. This time, a group allegedly affiliated with Anonymous claims to have hacked the systems of Transneft, the state-owned company responsible for the operation of Russian pipelines and one of the most important worldwide in its field.
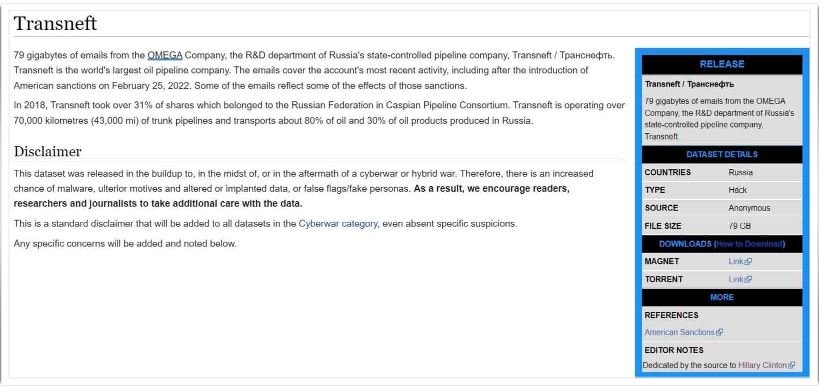
Last Thursday, Distributed Denial of Secrets (DDoSecrets), a non-profit organization, reportedly received about 79 GB of emails belonging to Omega, Transneft’s research and development division. Subsequently, the @YourAnonNews Twitter account also confirmed the incident, attributed to an Anonymous-linked group.
Representatives of DDoSecrets mention that the leaks of this information contain the data of the email accounts of the company’s employees, in addition to some confidential files and multiple reports on shipments, operations and staff.
Cybersecurity specialists have analyzed the leak, finding recent messages that would have been sent just a week ago, although they do not rule out that some of these files may be infected with malware. DDoSecrets continues to investigate the exposed information in search of any useful records for hacktivist groups.
Hacktivism has taken a very clear stance since the beginning of the war, with various groups attacking the computer systems of public and private organizations in Russia in retaliation for the invasion of Ukraine. Government websites, TV channels, streaming services and other Russia-based online platforms have all come under attack in recent weeks.
One of the most devastating incidents was the cyberattack against the Federal Communications, Information Technology and Media Supervision Service, whose systems were compromised by Anonymous hackers. After the attack, hacktivists shared some 360,000 sensitive files with DDoSecrets.
Another notorious attack was reported just a few days ago, when Anonymous managed to take control of some 400 CCTV systems in Russia, removing the original videos to instead convey a message against Putin and his so-called “special military operation in Ukraine.”
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
