CVE-2023-1281 and CVE-2023-1829 are two serious vulnerabilities that have been discovered in the Linux kernel. Both vulnerabilities have the potential to enable local attackers to gain root access by elevating their privilege level.
The Race Condition to Privilege Escalation, also known as CVE-2023-1281 (with a CVSS score of 7.8)
CVE-2023-1281 is a race situation vulnerability that may result in a use-after-free when upgrading faulty hash filters. It has been present in all Linux Kernel versions released since 4.14. The problem is caused by an imperfect hash area that is modified while packets are in transit via the network. Because of this, a use-after-free error occurs if the function tcf exts exec() is called when the tcf ext being used has been destroyed. Those who exploit this vulnerability have the opportunity to raise their privileges all the way up to root.
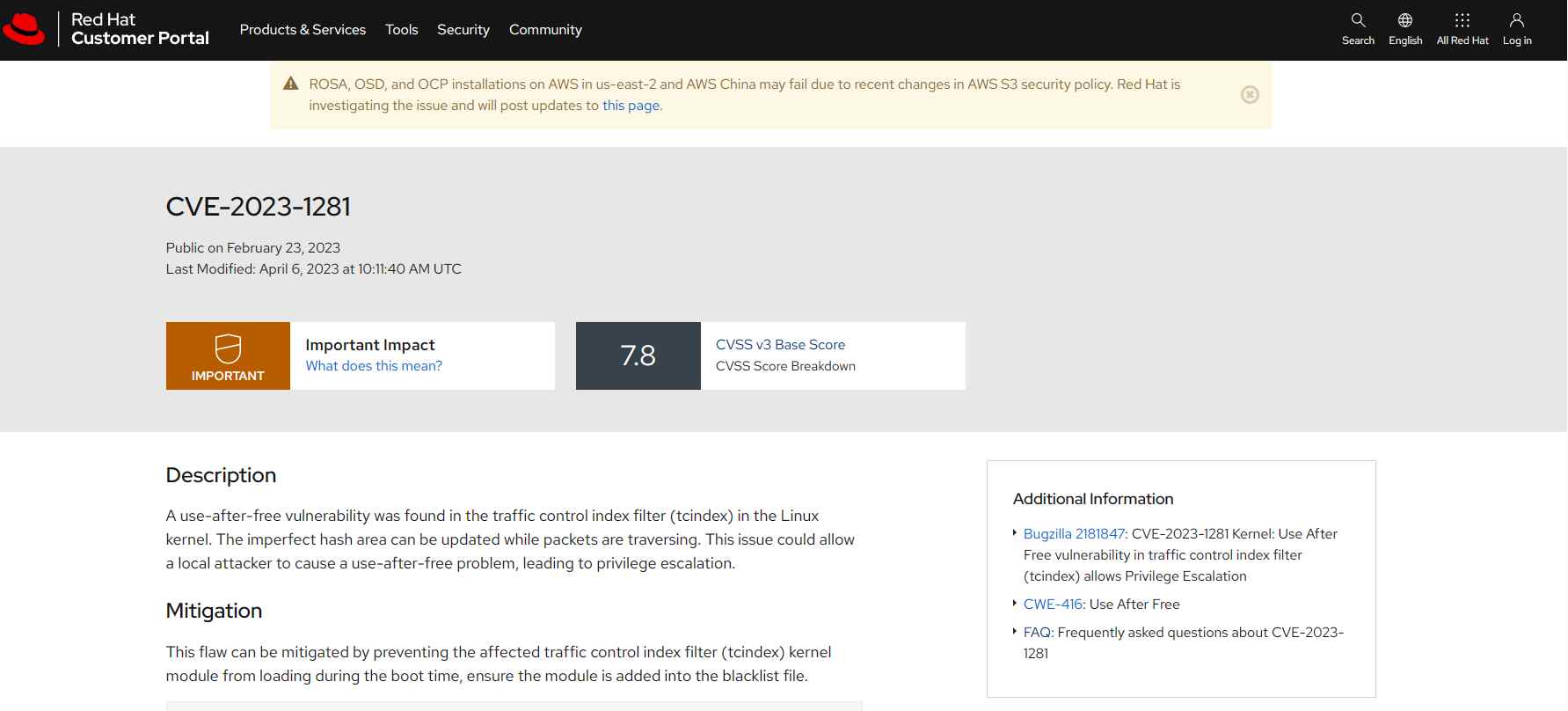
It is necessary to disable unprivileged user namespaces in order to mitigate CVE-2023-1281, since attackers need the CAP NET ADMIN permission in order to create or alter classifiers. This vulnerability has been corrected by the Linux kernel maintainers in the git commit.
CVE-2023-1829, also known as “A Perfect Storm for Privilege Escalation,” has a CVSS score of 7.8.
CVE-2023-1829 is a use-after-free vulnerability that has been present from the beginning of the git history (2.6.12-rc2) and became exploitable with net/sched netlink interface expose to user namespaces in version 3.8. It takes place in the tcindex delete() function whenever a perfect hash filter is removed from the index.
In the event when perfect hashes are present, the tcindex delete function does not disable filters in the correct manner. As a consequence of this, the underlying structure has been double-freed, which gives local attackers the ability to elevate their privileges and take control of the system.
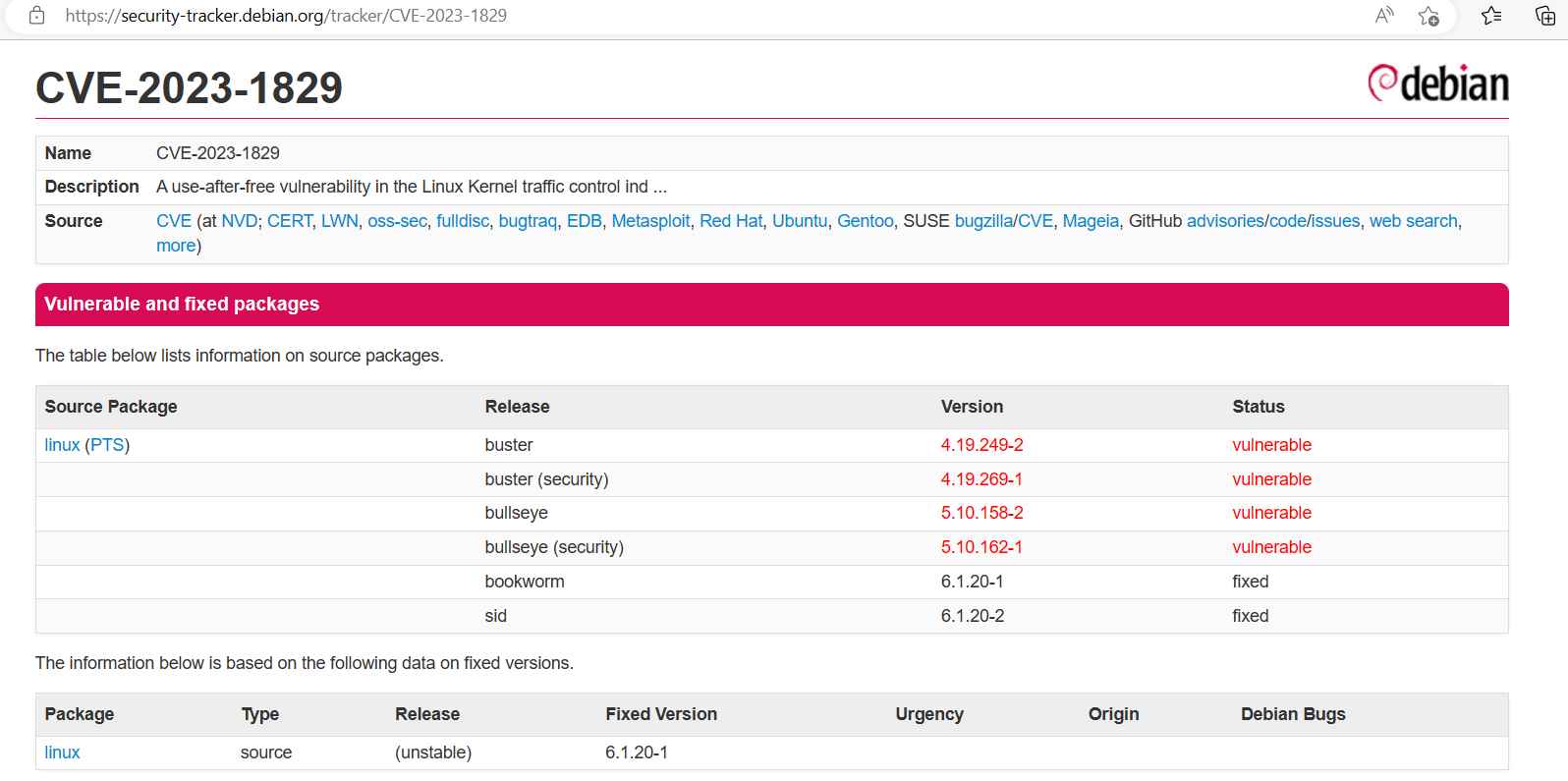
Since there aren’t very many people who use the tcindex classifier and there are a lot of bugs in the code, the people who maintain the kernel have chosen to do rid of it entirely as a precaution against CVE-2023-1829. It’s also a good idea to disable unprivileged user namespaces, since an attacker needs CAP NET ADMIN in order to make changes to classifiers or create new ones.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
