Cybersecurity specialists report the discovery of two critical vulnerabilities in the CCTV cameras of the technology firm Dahua Technology for which a proof of concept (PoC) exploit is already available. Identified as CVE-2021-33044 and CVE-2021-33045, the flaws can be exploited remotely to evade authentication mechanisms on the affected devices.
The announcement comes just weeks after Dahua asked its customers to install the latest firmware update, although due to the poor cybersecurity culture of thousands of users, updates are always slow to arrive. In other words, the vast majority of users are still running vulnerable versions.
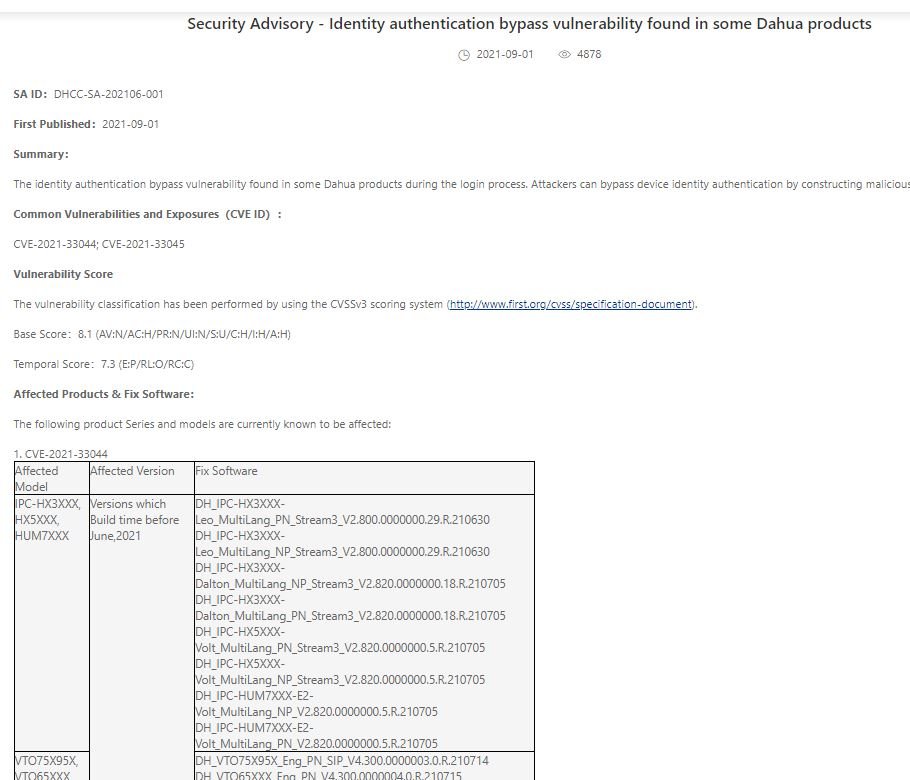
On the affected models, the faults reside in most of Dahua’s products, present in all kinds of environments. Using Shodan, the researchers detected more than 1.2 million potentially vulnerable Dahua devices around the world.
It is important to mention that, since October 2019, Dahua cannot sell its products in the United States, since it is one of the Asian companies vetoed by the U.S. Department of Commerce. However, there are still thousands of Dahua devices active in this country, as they were activated before the ban. In addition, other manufacturers such as Honeywell use Dahua hardware and software.
In addition to installing available updates, cybersecurity experts recommend resetting the passwords of vulnerable devices, preferably using a new and sufficiently secure security key. Enabling WPA2 encryption on wireless cameras is also recommended.
The vulnerabilities were detected on June 13, 2021, so some Dahua cameras remained vulnerable to unauthenticated access for nearly three months, even for owners who applied the firmware update as soon as it became available.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
