At least one sophisticated hacking group has been exploiting a critical remote code execution (RCE) vulnerability in VMware Workspace ONE Access. Tracked as CVE-2022-22954, the flaw was addressed in a recent security update, which also included fixes for CVE-2022-22957 and CVE-2022-22958, flaws in VMware Identity Manager, VMware vRealize Automation, VMware Cloud Foundation, and vRealize Suite Lifecycle Manager.
Shortly after these vulnerabilities were revealed, a proof-of-concept (PoC) code was publicly disclosed, so reports began to emerge about various hacking groups exploiting these flaws to take control of vulnerable VMware deployments. The company also confirmed that CVE-2022-22954 was being actively exploited.
According to a report by the security firm Morphisec, at least one group of threat actors has been linked to some cases of exploitation of this flaw. This is an advanced persistent threat (APT) group identified as Rocket Kitten or APT35 and its center of operations would be in Iran. This hacking group has been linked to other malicious campaigns exploiting vulnerabilities in VMware.
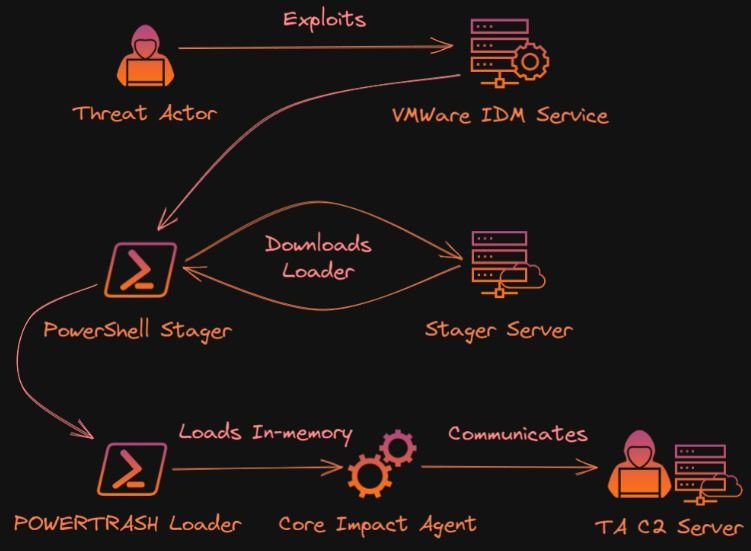
Malicious hackers gain initial access to the target environment by exploiting CVE-2022-22954, the only one of the three flaws fixed by VMware that does not require administrative access to the affected server and for which there is a known PoC exploit.
The attack continues with the execution of a PowerShell command in Identity Manager, which is the vulnerable service. The organizer then obtains the PowerTrash loader from the C&C server in a much obfuscated way to load a Core Impact agent into the memory of the affected system. Core Impact is a legitimate pentesting tool that can be abused for malicious purposes similar to Cobalt Strike.
Michael Gorelik, director of Morphisec, mentions that threat actors have tried to use this flaw to perform side-moving attacks on affected networks: “With privileged access, these types of attacks can easily evade typical defenses, including antivirus and endpoint detection and response,” he says.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
