Cybersecurity specialists report the detection of an out-of-bounds read flaw in the popular Squirrel programming language whose exploitation would allow threat actors to evade security restrictions and execute arbitrary code on a Squirrel virtual machine, compromising the affected system completely.
As some users will recall, Squirrel runs primarily on online video games and Internet of Things (IoT) devices, so the commitment of this implementation could put millions of users at risk each month.
The vulnerability, tracked as CVE-2021-41556, was described as an out-of-bounds read flaw that can be exploited when a Squirrel Engine is used to execute unverified code, as occurs in implementations such as Twilio Electric Imp or with specific video games.
According to researchers Simon Scannell and Niklas Breitfeld, responsible for the finding, threat actors could embed a malicious Squirrel script in a map created by users of some video games and distribute it through mod sharing tools such as Steam Workshop.
When a user downloads and runs the mod on their own system, the malicious script will trigger its functions, exiting the virtual machine and taking full control of the affected server. Among the video games that use Squirrel for mod creation are popular titles such as Counter-Strike: Global Offensive and Portal.
In their proof of concept (PoC), the researchers showed how the Squirrel interpreter will create a null and segfault pointer dereference because the array _defaultvalues has not yet been assigned.
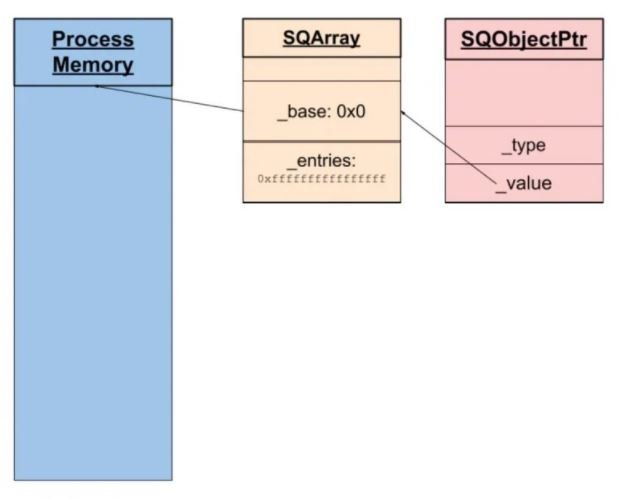
Threat actors could set up a fake array to read and write values, eventually allowing them to hijack the control flow of the target program and gain full control of the affected virtual machine by overwriting the function pointers.
Squirrel’s maintainers were notified through their GitHub repository last August, announcing the release of a patch to address this issue in mid-September. However, the changes were not automatically applied, so users of the latest version of Squirrel will need to verify their implementation manually.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
