McAfee security teams announced the correction of a critical vulnerability in McAfee Agent for Windows software that would allow threat actors to perform privilege escalation and remote code execution (RCE) attacks with SYSTEM privileges. This software is a client-side component for downloading and enforcing endpoint policies, deploying antivirus signatures, and new enterprise endpoint products.
Tracked as CVE-2022-0166, the flaw was described as a local privilege escalation, discovered by vulnerability analyst Will Dormann. All McAfee Agent versions prior to 5.7.5 are vulnerable to attack.
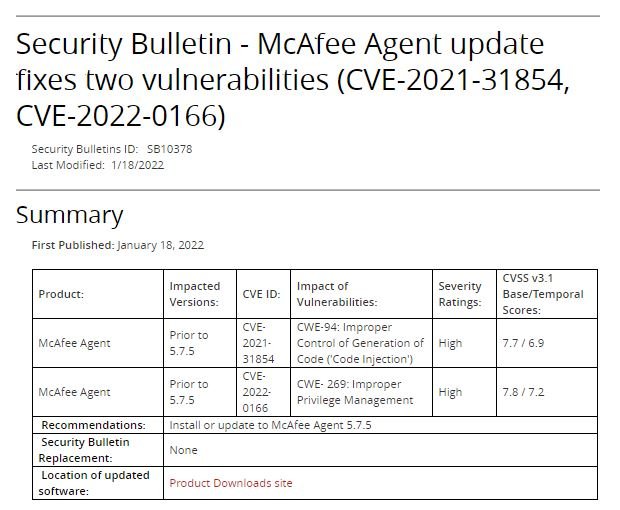
According to the researcher, this product includes an OpenSSL component that specifies a OPENSSLDIR variable as a subdirectory that can be controlled by an unprivileged user in Windows, placing a specially crafted openssl.cnf file in a path suitable for executing arbitrary code with SYSTEM privileges.
A successful attack would allow threat actors to execute malicious payloads and even evade detection during attacks. Although the flaw must be exploited locally, hackers can execute this type of flaw during later stages of other attacks, after infiltrating the target system to escalate privileges on the affected system.
This is not the first time security flaws have been detected in McAfee products for Windows. In September 2021, the company’s security teams announced the fix of CVE-2020-7315, a flaw in McAfee Agent that would have allowed threat actors to execute arbitrary code and even remove security software on the affected system.
A couple of years earlier, McAfee addressed a severe vulnerability in all editions of its antivirus for Windows systems that opened the door to remote code execution and privilege escalation attacks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
