Maintainers of Argo CD, the continuous delivery (CD) tool for Kubernetes, announced the fix of a vulnerability that would have allowed threat actors to spoof JSON Web Tokens (JWTs) and take control of affected deployments. According to the report, the flaw exists because GitOps trusts invalid JWT tokens if anonymous access is enabled.
The bug allowed unauthenticated malicious hackers to send a specially crafted JWT to a vulnerable implementation, leading to a privilege escalation attack on the cluster that the Argo CD instance. A successful attack would allow threat actors to manipulate and remove any resource from the cluster.
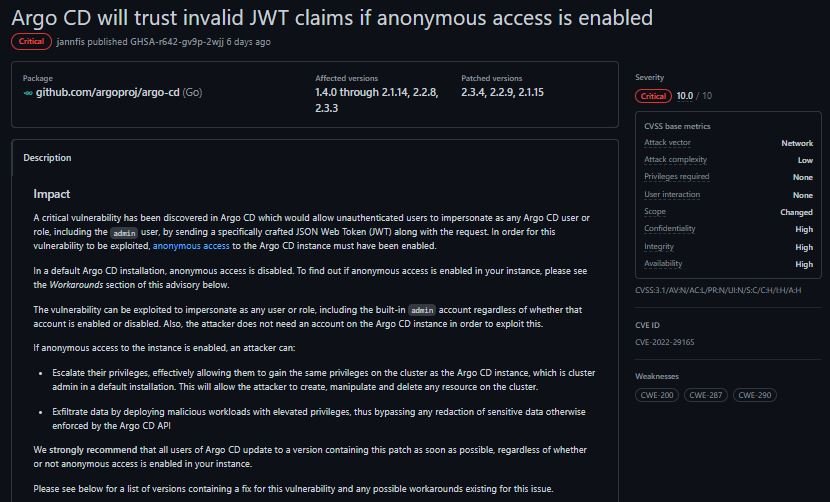
The flaw received a score of 10/10 according to the Common Vulnerability Scoring System (CVSS), so its potential exploitation is considered a critical security risk. The good news is that the anonymous access required for exploitation is disabled by default.
The flaw affects versions 1.4.0 through 2.1.14, 2.2.8 and 2.3.3, and was corrected in versions 2.3.4, 2.2.9 and 2.1.15, so users of affected deployments are advised to update immediately. Verifying that anonymous access is disabled is also recommended. To define if this setting is disabled, refer to the ConfigMap argocd-cm in the namespace of your installation.
The corrected versions also include a patch for a medium-severity vulnerability that would allow threat actors with write access to extract sensitive files from the Argo CD repository server.
This flaw was first identified as part of a Trail of Bits audit published in March. Software engineer Michael Crenshaw independently identified it again before the critical patches were released.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
