Although they may no longer be as popular as they were a couple of years ago, e-reader security analysis remains a field of interest to several cybersecurity experts. A recent report mentions the finding of a set of vulnerabilities in Amazon Kindle that could be exploited to run remote code on an affected device. The attack was dubbed ‘KindleDrip’.
The report, published by Readlmode Labs, details how a group of experts managed to access a compromised Amazon account using only an e-reader and its email address. The flaw was fixed during the latest Kindle updates (firmware version 5.13.4).
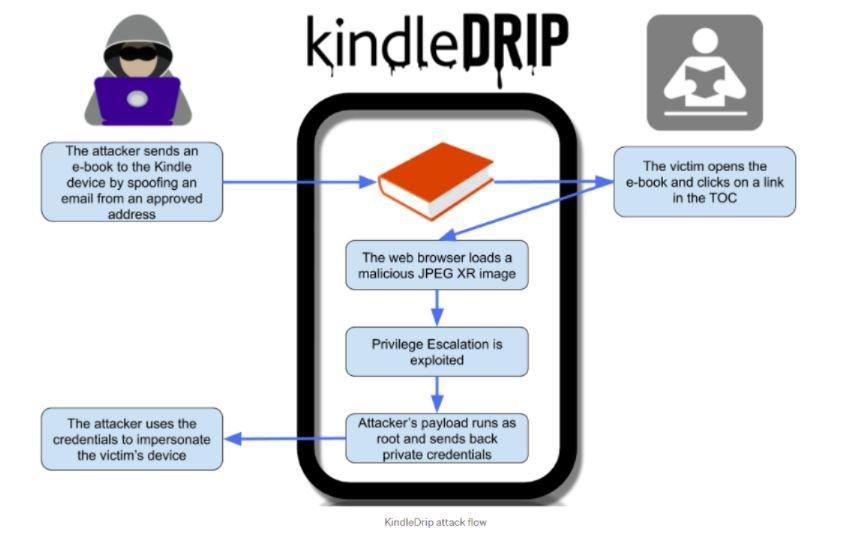
The operation of KindleDrip is based on three flaws found in these tablets; the first flaw allows a forged email address to bypass authentication checks on Kindle, which threat actors could take advantage of by sending a hidden malicious file disguised as an e-book.
On the other hand, Amazon’s “Send to Kindle” feature provides the ability to send a purchase information document directly to the users’ e-reader through a list of pre-approved senders, including each user’s Kindle email address, automatically generated by Amazon.
Experts managed to copy a user’s Kindle email address to send an e-book to their device without having to go through Amazon’s authentication process: “There is no indication of this malicious e-book origin, and it even appears on the home page of the affected device with a cover image that can be edited by the attackers”, mentions the report.
The second flaw exploited by researchers exists due to the way Kindle analyzes the JPEG XR image format, which can be loaded through a conventional browser: “If users click on a link in the e-book, a browser window containing the malicious JPEG XR image will open, thus initiating arbitrary code execution in the context of an exposed user”.
Eventually the third vulnerability is exploited. This is a privilege escalation flaw that, in conjunction with the remaining two errors, can lead to private credential theft and remote code execution.
Investigators who filed the report with the company’s vulnerability bounty program received an $18,000 USD payment. Amazon announced that the flaw was fixed on December 10, meeting deadlines set by the cybersecurity community. On the attack, the experts only added that the flaws were not easy to find, although once this step was resolved the rest of the process was very simple.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
