An Intel security report points to the detection of various memory errors in the firmware of microprocessors used in hundreds of its products. According to the company’s report, these are high-risk flaws and received scores above 7/10 according to the Common Vulnerability Scoring System (CVSS).
Specifically, the flaws reside in some versions of Intel Optane SSD and Intel Optane Data Center, and their malicious exploitation would lead to the deployment of denial of service (DoS), privilege escalation, and sensitive information leaking attacks.
The company released corresponding firmware updates and additional guidance on how to address bugs in Optane SSD. This is an acceleration solution used to increase response time to end-user requests, and experts say, optane memory stores commonly used data and programs closer to the processor.
On the other hand, Intel Optane Data Center SSD eliminates data center storage bottlenecks, providing storage for large data sets and improving overall system performance.
This patch set released by Intel includes fixes for the following bugs in Intel Optane SSD and Intel Optane Data Center:
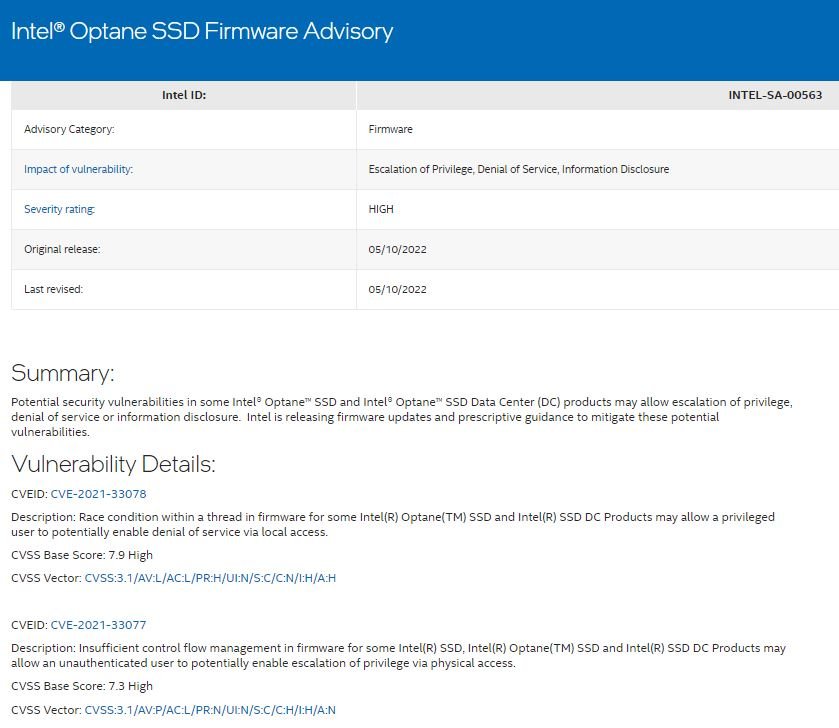
CVE-2021-33078: A race condition within a thread on affected products would allow threat actors to deploy DoS attacks through local access. The flaw received a CVSS score of 7.9/10.
CVE-2021-33077: Inadequate control flow management in the firmware for affected products would allow unauthenticated users to escalate their privileges on the affected system. The flaw received a CVSS score of 7.3/10.
CVE-2021-33080: Threat actors can disclose sensitive information or escalate privileges through physical access to affected products. This flaw received a CVSS score of 7.3/10.
Affected products include all versions of Intel Optane SSD DC D4800X and P4800X/P4801X, including the previous version E2010600. As for the Intel Optane SSD P5800X products, all versions prior to vL3010200, as well as the 905P/900P series, are affected.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
