OpenSSL project managers have issued a security alert regarding the finding of two critical vulnerabilities tracked as CVE-2021-3449 and CVE-2021-3450. As you may remember, OpenSSL is a commonly used software library for creating servers and network applications for establishing secure connections.
The following is a brief description of the reported flaws:
- CVE-2021-3449: This is a denial of service (DoS) vulnerability that exists due to null pointer dereference that only affects OpenSSL server instances, not clients
- CVE-2021-3450: An incorrect Certification Authority (CA) certificate validation vulnerability that affects both the server and client instances
On the first flaw, the developers mentioned that an OpenSSL TLS server can cause the server to crash if during the course of client negotiation it sends a specially designed message: “If this process ignores the signature_algorithms extension, but includes a signature_algorithms_cert extension, a null pointer dereference will occur, resulting in a denial of service condition”, the experts mention.
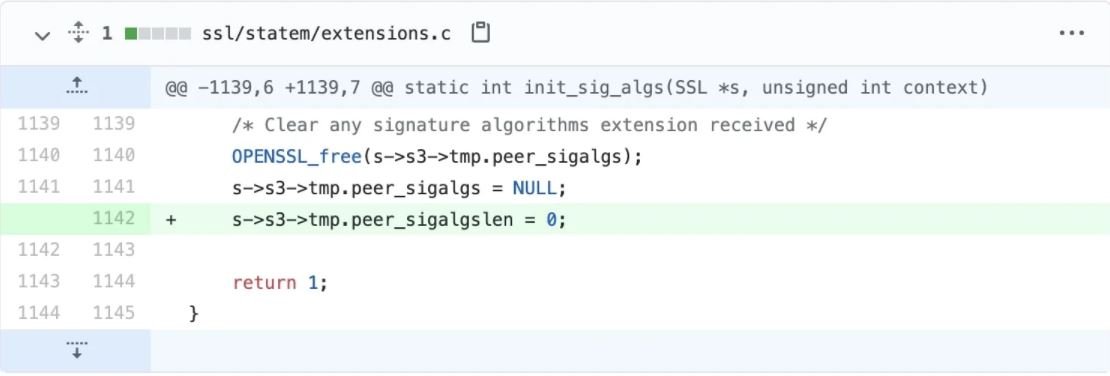
The flaw appears to only affect OpenSSL servers with versions between 1.1.1 and 1.1.1j, which have TLSv1.2 and the default enabled renegotiation feature, which could put multiple active servers at risk. The flaw was corrected just by adding a line to peer_sigalgslen.
On the other hand, the second reported flaw was related to the X509_V_FLAG_X509_STRICT indicator: “OpenSSL uses this flag to prevent the use of temporary solutions for expired certificates, forcing developers to adhere to X509 rules,” the report says.
Due to a regression error, OpenSSL versions 1.1.1h and above are affected by this flaw, as this flag is not configured by default in these versions. Starting with OpenSSL version 1.1.1h, a check was added to prevent the use of certificates in the chain that have elliptical curve parameters explicitly encoded as an additional protection mechanism.
The flaw was reported to OpenSSL by Akamai’s Benjamin Kaduk on March 18. Both flaws were fixed in OpenSSL 1.1.1k, so users of affected deployments are advised to upgrade to this release as soon as possible to prevent mitigation risks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
