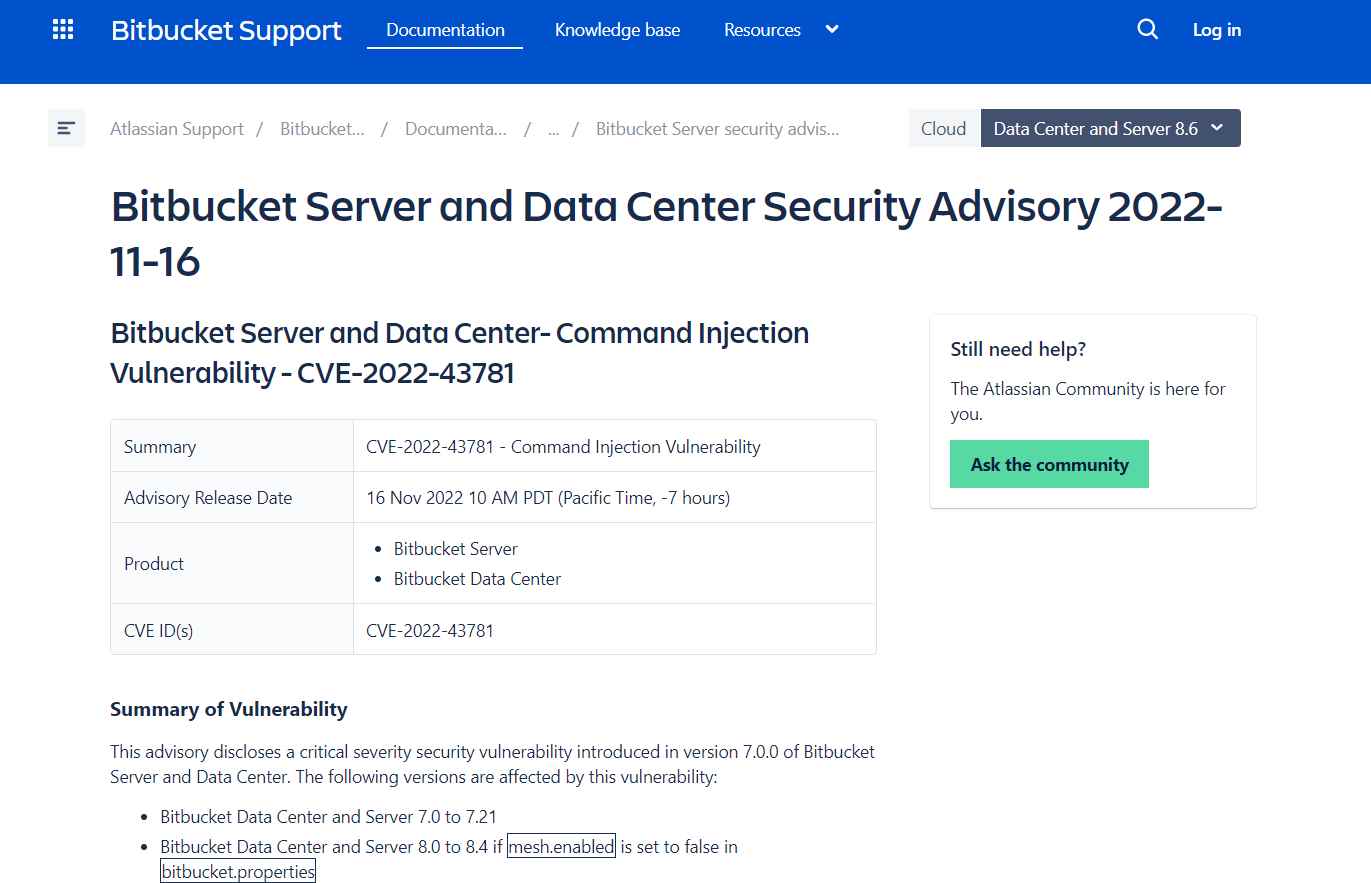
For its Bitbucket Server and Data Center offering, Atlassian has released updates to address a significant security flaw.
The flaw, identified as CVE-2022-43781, has been described as a command injection weakness utilizing environment variables that might be exploited through specifically constructed queries.
This vulnerability affects the following versions:
Server and Data Center for Bitbucket 7.0 through 7.21
If mesh.enabled is set to false in bitbucket.properties, Bitbucket Data Center and Server versions 8.0 to 8.4 will not function.
According to the scale that has been disclosed, Atlassian classifies the severity level of this vulnerability as critical.
Bitbucket Server and PostgreSQL-powered Data Center instances, according to the business, are unaffected by this problem.
“The Bitbucket Server and Data Center have a command injection vulnerability that makes use of environment variables. An attacker who has access to their login can take advantage of this flaw to get code execution and run code on the system, according to a statement from Atlassian.
The Bitbucket Server and Data Center have a command injection vulnerability that makes use of environment variables. An attacker who has access to their login can take advantage of this flaw to get code execution and run code on the system, according to a warning from Atlassian.
Instead, it advises users to either turn off “Public Signup” or update to the newest version of the software. The danger of exploitation would decrease if public registration was disabled since it would convert the attack from an unauthenticated attack to an authenticated assault. Clear the Allow public sign up option under Administration > Authentication to deactivate this setting.
When public signup is turned off, the vulnerability can still be used by ADMIN or SYS ADMIN authorized users.
The business issued a warning in its advisory addressing CVE-2022-43781, saying, “For this reason, this mitigation should be viewed as a temporary measure and clients are urged to update to a corrected version as soon as feasible.”
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
