An attack has been discovered that can expose developers, it was discovered that nearly a third of the packages in PyPI, the Python Package Index, can automatically cause code execution when downloaded.
“A concerning feature in pip/PyPI allows code to be executed automatically when developers simply download a package.”
Yehuda Gelb, a researcher at Checkmarx, in a white paper published this week.
One of the ways to install Python packages is by running the “pip install”, calling the “setup.py” that is included with the module. This script is used to specify the metadata associated with a package, including its dependencies.
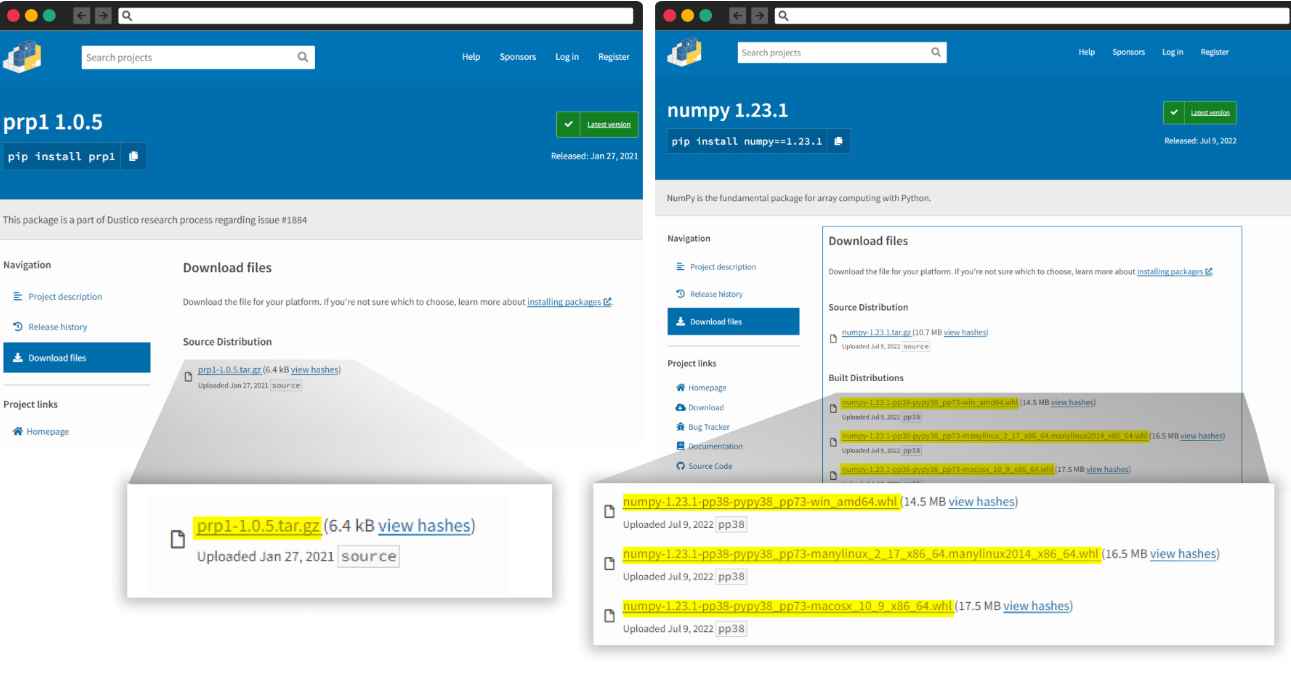
While attackers have resorted to embedding malicious code in the “setup.py” script, Checkmarx found that they could accomplish the same goals by running the “pip download” command. This function does the same download as “pip install”, but it does not install the dependencies, it only downloads them. This download command also executes the “setup.py” script, thus executing the malicious code it contains.
Note that the problem only occurs when the package to be installed or downloaded contains a tar.gz file instead of a .whl file, which prevents “setup.py” from running.
This feature is alarming because most of the malicious packages found use this code execution technique when they are installed, thus achieving higher infection rates.Although pip uses .whl instead of .tar.gz, an attacker could exploit this behavior to intentionally publish python packages without a .whl, leading to malicious code execution.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
