Cisco security teams recently announced that they will not issue a security patch for critical flaw detected on three of their SOHO router models even though it received a score of 9.8/10 according to the Common Vulnerability Scoring System (CVSS). The company argues that these devices have reached the end of their useful life and do not require the release of security updates, although it recommends that users replace them with newer versions.
Experts add that this flaw exists due to incorrect validation of user-provided entries in the web management interface of these devices: “Threat actors could take advantage of these flaws by sending specially designed HTTP requests, which would allow arbitrary code to run as a root user on the affected operating system.”
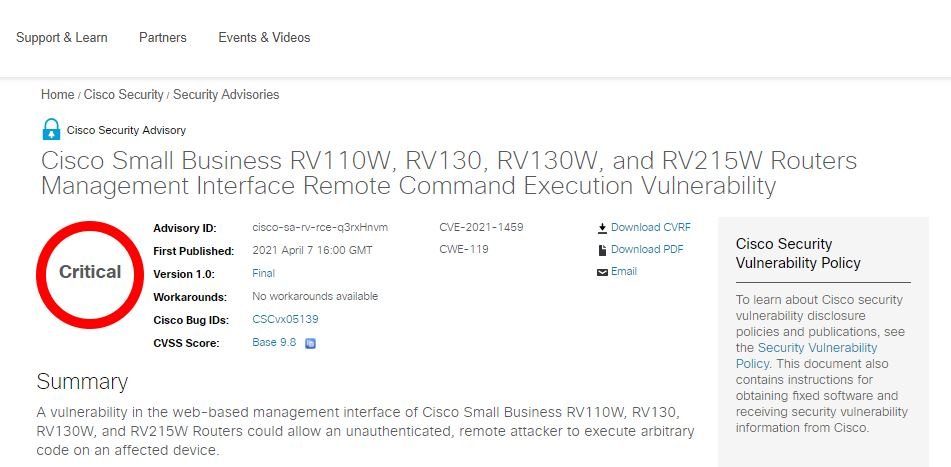
At the moment there are no workarounds for this flaw: “The web management interface is available over a local connection that cannot be disabled, although the remote management feature is disabled by default.”
Affected router models (RV110W, RV130, and RV215W) have faced frequent security issues over the past couple of years. In 2019 it was discovered that a hacking group was actively exploiting a critical flaw due to the use of an insecure programming language.
As if that wasn’t enough, Cisco reported detecting a second critical vulnerability by affecting some versions of its SD-WAN vManage software: “Successful exploitation of this flaw would allow unauthenticated remote hackers to execute arbitrary code on the target system and even perform privilege escalation attacks.”
Each of these flaws is independent and does not require chaining up for exploitation: “These vulnerabilities do not depend on each other; exploiting one of the vulnerabilities is not necessary to exploit the remaining flaws.” The most serious of these flaws was identified as CVE-2021-1479 would allow threat actors to launch buffer overflow attacks.
Cisco decided to release security patches for flaws residing in vManage SD-WAN, as these systems continue to be widely used. The company adds that so far no security incidents related to exploiting these flaws have been detected.
To learn more about computer security risks, malware, vulnerabilities and information technologies, feel free to access the International Cyber Security Institute (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
