Section 52, the Microsoft group specializing in Internet of Things (IoT) security research, reported the finding of a set of critical flaws in the memory allocation process on IoT and OT devices that threat actors could exploit to evade security controls and run remote code on affected systems. The experts found at least 25 vulnerabilities in industrial, medical, and enterprise IoT/OT deployments.
These flaws reside in the standard memory allocation functions used in real-time operating systems (RTOS), software development kits (SDKs), and standard C library implementations. The vulnerabilities, dubbed BadAlloc, were reported to the Microsoft Security Response Center (MSRC).
All BadAlloc vulnerabilities stem from the use of vulnerable memory functions such as malloc, calloc, realloc, memalign, valloc, and pvalloc, among others. Microsoft’s report shows that memory allocation implementations written over the years as part of IoT devices and integrated software have not incorporated the proper input validations, making them highly vulnerable to threat actors.
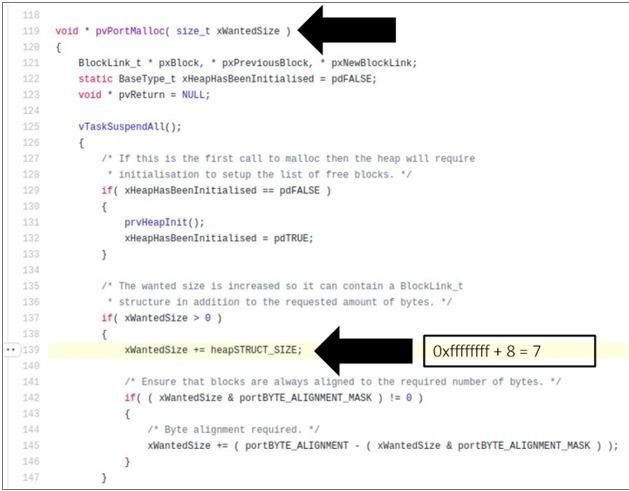
The researchers mention that vulnerabilities can be invoked by calling the affected memory allocation function with the VALUE parameter dynamically derived from an external input; this must be large enough to trigger an integer overflow condition.
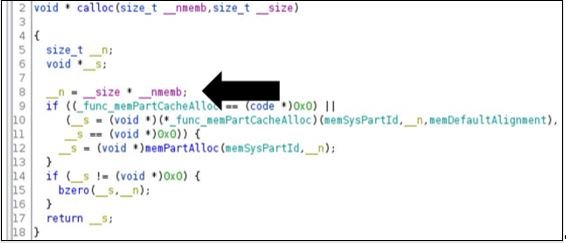
By sending this value, the return result is a newly allocated memory buffer. Even though the size of the allocated memory is still small, the payload associated with the memory allocation exceeds the actual allocated buffer, resulting in a heap overflow that in turn would allow threat actors to execute malicious code on the affected device.
The standardized use of these implementations makes the successful exploitation of these vulnerabilities a risk for organizations across multiple industries. While Microsoft has not detected any active exploit attempts, vendors are encouraged to release patches to address these flaws as soon as possible. If you are unable to upgrade, Section 52 recommends that you implement one of the following measures:
- Monitoring and supervision: Most IoT and OT devices do not support agents, so device administrators can employ a network discovery and response (NDR) solution with IoT/OT recognition
- Reduced the attack surface: Admins can also eliminate unnecessary Internet connections to OT control systems and implement VPN access with multi-factor authentication to reduce exposure of vulnerable systems
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
