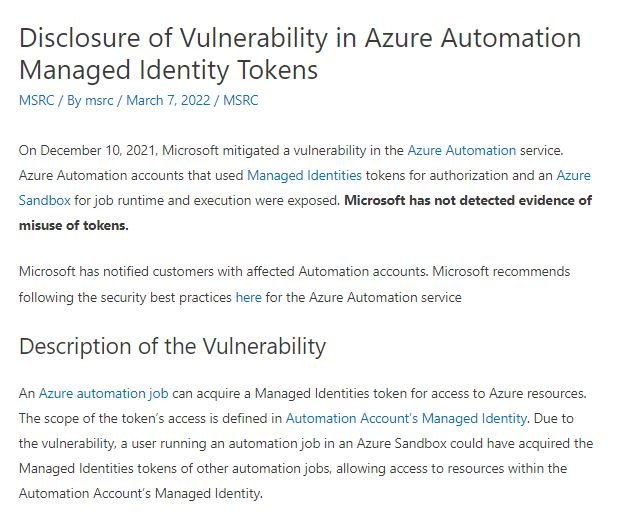
In its latest security alert, Microsoft reports a bug in its Azure cloud platform that allowed users full access to other users’ accounts. The flaw, dubbed as “AutoWarp”, was reported by Orca Security investigators. Apparently, the flaw only affects users of Azure Automation Service, which allows Azure users to use PowerShell or Python to write runbooks and automate functions on the platform.
The Automation service does not allow any user to initiate actions on your Azure computer, so you must link them to an identity with the relevant permissions. However, Microsoft confirmed that its service would allow users running an automation job in Azure Sandbox to acquire managed identity tokens from other automation jobs, allowing access to resources within the managed identity of the automation account.
During their tests, Orca Security researchers were able to access multiple tokens, plus they discovered that it was possible to access an Azure account controlled by an international telecommunications firm, two automakers, a banking institution, and various accounting firms.
These tests and the report took place in late 2021, so Microsoft was able to address the flaws in mid-December. This error was publicly disclosed on Monday, once the deadlines set by the cybersecurity community were met.
The company also ensured that managed identity tokens do not allow the involvement of threat actors. Microsoft should learn a big lesson from this incident, as security is a fundamental principle for its cloud computing systems and such a mistake could prove disastrous even for its largest enterprise customers.
This is the third time severe security flaws have been found in Azure in less than six months. In September 2021, Microsoft unveiled what they described as an “OHMIGOD remote code execution bug,” while last December the NotLegit flaw was discovered, which would have allowed the download of unauthorized files for about four years.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
