Patch Tuesday for the month of April 2023 has here, and with it comes a torrent of new security updates designed to patch a total of 97 vulnerabilities, including one zero-day vulnerability that is being actively exploited. Patches are available for Microsoft Windows and Windows Components, Microsoft Office and Office Components, Windows Defender, SharePoint Server, Windows Hyper-V, PostScript Printer, and Microsoft Dynamics. These updates address security flaws.
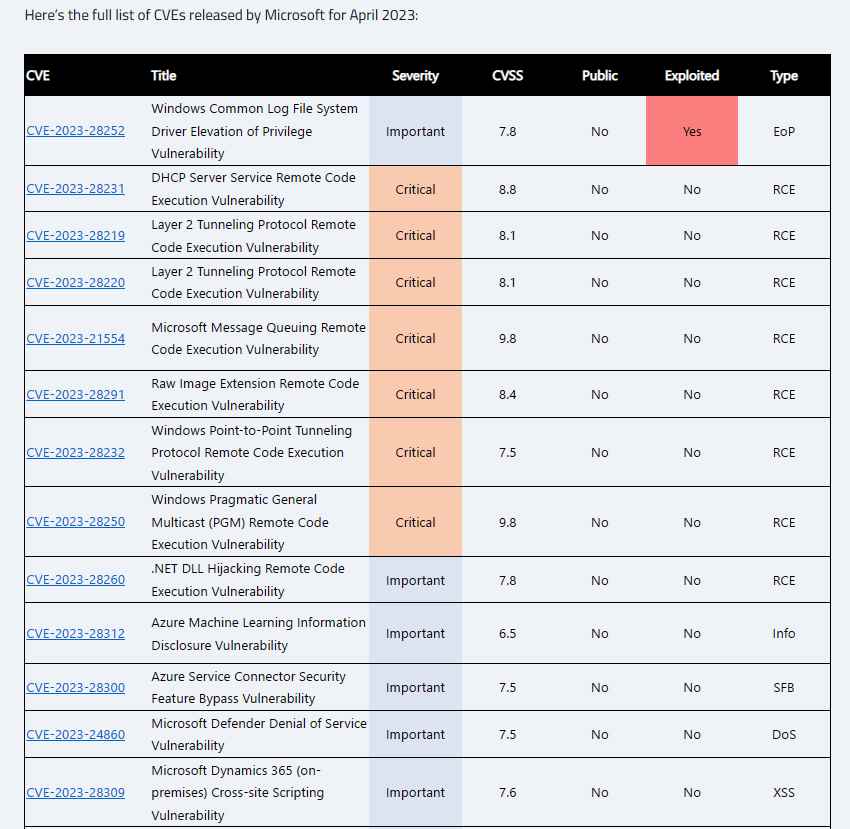
At the time of the publication, it is reported that one of the new CVEs is already the target of an attack. This vulnerability, which has been assigned the tracking number CVE-2023-28252 and has a CVSS score of 7.8, affects the Windows Common Log File System Driver component. This zero-day vulnerability is being actively exploited right now, and it seems to be frighteningly identical to another weakness that was fixed in the same component only two months ago. This points to the fact that the first remedy not only was inadequate but also that attackers have discovered a way to get around it. There is no information available on the scope of these attacks; nonetheless, vulnerabilities of this kind are frequently combined with code execution issues in order to spread malicious software or ransomware. It is of the utmost importance to test and implement this fix as quickly as feasible.
Microsoft said in its warning that an attacker who successfully exploited this issue may acquire SYSTEM rights if the vulnerability was exploited. The corporation has given credit for discovering and reporting the CVE-2023-28252 vulnerability to the security researcher Genwei Jiang of Mandiant and Quan Jin of DBAPPSecurity WeBin Lab.
This month brings us an intriguing upgrade that is being monitored as CVE-2013-3900. This patch, which was first released ten years ago, is being republished since it was recently used by threat actors in the 3CX attacks. The new patch, which had previously been a “opt-in” remedy, contains updates for more systems and includes additional advice for organizations. It is critical to evaluate all of the advice, including the information on the Microsoft Trusted Root Program, and take the appropriate measures to safeguard your environment. Reviewing all of the suggestions is a good place to start.
The most serious of these flaws, which goes by the name QueueJumper (CVE-2023-21554), might make it possible for unauthorized attackers to execute arbitrary code remotely in the context of the Windows service process mqsvc.exe. With the version that was released on April Patch Tuesday, Microsoft included a fix for this vulnerability.
MSMQ is a message infrastructure and development platform for the Microsoft Windows operating system that allows developers to create distributed messaging applications with loose coupling using a message broker. MSMQ is still accessible on all Windows operating systems, including the most recent Windows Server 2022 and Windows 11, and it is supplied as an optional Windows component. Despite the fact that it is considered a “forgotten” or “old” service, MSMQ is still available.
Reaching TCP port 1801 enables an attacker to possibly execute malware remotely and without authorisation thanks to the QueueJumper vulnerability, which is tracked under the CVE identifier CVE-2023-21554. An adversary might take control of the process by sending only one packet to the 1801/tcp port while using the exploit, which would then cause the security vulnerability to be exploited.
CheckPoint advises all administrators of Windows systems to examine their servers and clients to see whether or not the MSMQ service has been installed.
Users or administrators may check to see whether a service on the computer called “Message Queuing” is now active and whether or not TCP port 1801 is waiting for incoming connections. If it is already installed, you should check to see whether you really need it.
It is almost always a very excellent practice for security to close off any superfluous attack surfaces. Users should apply the official patch from Microsoft as soon as possible in order to protect themselves against this specific vulnerability. As a workaround, if a company needs MSMQ but is unable to deploy the fix that Microsoft has released right now, the company might use its firewall rules to prevent incoming connections for port 1801/tcp from coming from untrusted sources.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
