A cybersecurity specialist reports the detection of a dozen vulnerabilities in myPRO, a product developed by industrial automation firm mySCADA. Among the reported flaws, the expert highlighted an error considered as critical. A first set of vulnerabilities was addressed in July with the release of myPRO v8.20.0, while the second set of flaws was fixed in early November with myPRO v8.22.0.
In this regard, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) also issued two alerts to inform organizations about these vulnerabilities. While the first warning was published in August, the second security alert arrived on December 21.
Researcher Michael Heinzl mentioned that myPRO is a human-machine interface (HMI) and supervisory control and data acquisition (SCADA) system designed to visualize and control industrial processes. This solution can run on Windows, macOS, and Linux systems.
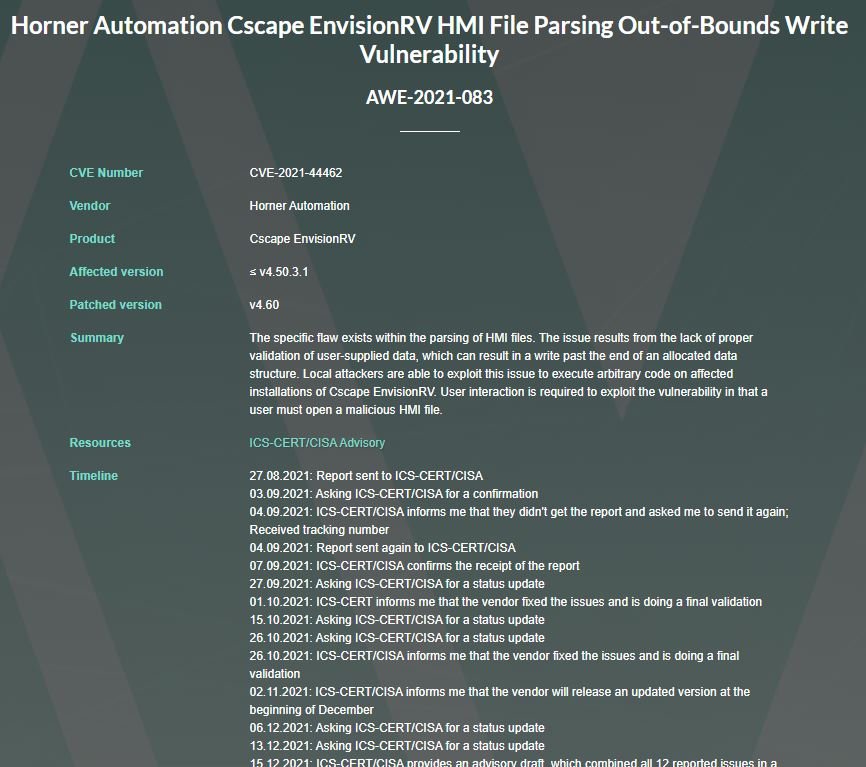
According to the report, the security problem “results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated data structure. Local attackers are able to exploit this issue to execute arbitrary code on affected installations of Cscape EnvisionRV. User interaction is required to exploit the vulnerability in that a user must open a malicious HMI file”
The report adds that this is a solution used on a large scale, mainly in the energy, food, agriculture, water treatment and transport sectors. Figures published by the company itself indicate that its main focuses of operation are in Europe.
Heinzl concluded by mentioning that the affected application runs at system startup with elevated privileges and, by default, listens on TCP ports 80/443 on all network interfaces. Unauthenticated remote threat actors could take advantage of failures to take complete control of the product as well as the underlying system.
The researcher has identified other security flaws in many industrial products this year, including those from Delta Electronics and Fuji Electric.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
