Experts at ESET cybersecurity firm have revealed the discovery of a new malware framework with advanced capabilities and many other samples of a complex development process. Identified as Ramsay, experts claim that this malware’s toolkit is capable of compromising isolated systems (known as air-gapped), and can even collect Word documents and other similar formats and then wait for the right time to extract the information undetected.
Ramsay’s discovery is highly relevant to the cybersecurity community, as researchers rarely have the opportunity to analyze malware capable of violating air-gapped systems, which are considered to be the most stringent and effective security implementation, employed by thousands of companies to protect sensitive information.
It should be remembered that air-gapped systems are machines or networks isolated from the rest of a network and the public Internet. Typically, these implementations are located in the networks of government agencies and large private corporations, and safeguard classified documents, such as intellectual property material or national security information.
These are considered “impossible to hack” systems and a potential way to access a similar implementation would be considered a Holy Grail in the world of hacking.
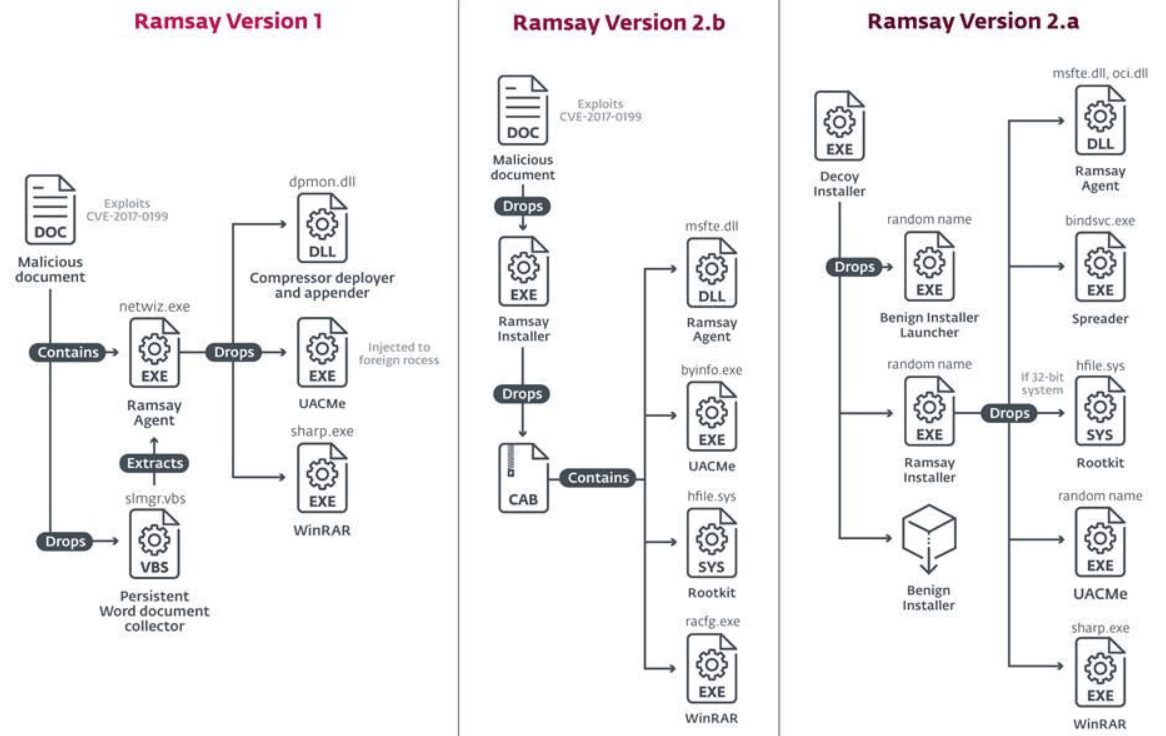
In its report, ESET mentions that this malware variant appears to have been specifically designed to hack isolated networks. In addition, experts point to the finding of three different variants of malware. Each version infects victims via different methods, but in general, the main function of the malware is to scan an infected computer and collect Word, PDF and ZIP documents into a hidden storage folder, ready to be extracted at a later date.
Another detected version also includes a module to spread copies of Ramsay to all portable executables on removable drives and network shares. Experts believe this is the mechanism used by hackers to dodge isolation in the target system and complete the attack.
Experts mention that they were unable to clearly identify the presence of this module, nor determine how malware operators extract the collected information. However, researchers believe they have enough evidence to show that Ramsay attacks have existed in real-world scenarios.
Finally, although Ramsay’s development has not been attributed to any hacking group, ESET believes that the malware contains multiple similarities to Retro, a malware variant developed by DarkHotel, a group of malicious hackers allegedly sponsored by the South Korean government.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
