Microsoft security teams identified a malware operation apparently targeting organizations based in Ukraine. Identified in early 2022, this malware appears to be linked to complex geopolitical conflicts in the region, so the company advised potentially affected organizations to stay on top of any malicious activity.
Early reports indicate that the malware, provisionally identified as DEV-0586, is designed to emulate some tasks of the likes of ransomware, although it does not have a recovery mechanism, leaving the affected devices completely unusable.
The first hint of this new malware variant was detected on January 13, when Microsoft identified a malicious intrusion into a Ukrainian organization. Although at first it seemed like another example of information eliminator attacks against Master Boot Record (MBR) implementations, the researchers soon concluded that it was a new malicious utility.
In its report, Microsoft identifies two main attack stages in the DEV-0586 campaign, detailed in its official blogs and briefly described below.
Stage 1: MBR wipe and fake ransom note
Once installed on the affected systems, the malware can be hosted in locations such as C:\PerfLogs, C:\ProgramData, C:\ & C:\temp, receiving file name stage.1exe. Microsoft believes the malware runs through Impacket, a capability exploited by some hacking groups in side-moving and execution attacks.
After execution, the malware removes the MBR on the victims’ systems and replaces the registry with a ransom note; as you may recall, the MBR is the part of a hard drive that tells the computer how to load its operating system. The ransom note contains a Bitcoin wallet and a never-before-seen Tox ID.
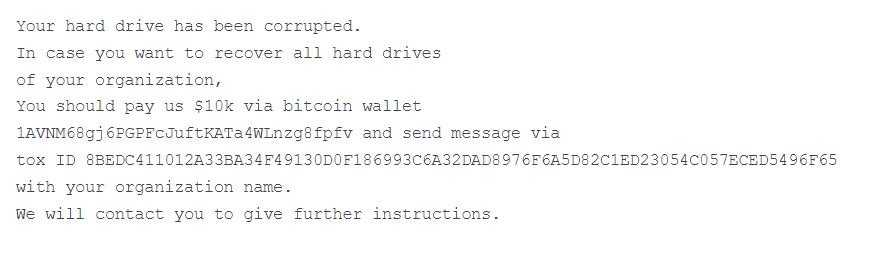
Overwriting the MBR is not ransomware-like behavior, so Microsoft experts began analyzing the attack in depth, finding that the publication of the ransom note is only a trick to divert attention from the true purpose of the attack.
Stage 2: Compromising files in the affected system
This second attack requires stage2.exe, which downloads file corrupting malware hosted on a Discord channel. When executed in the memory of the target system, this malware begins to search certain system directories to identify some file extensions, including:
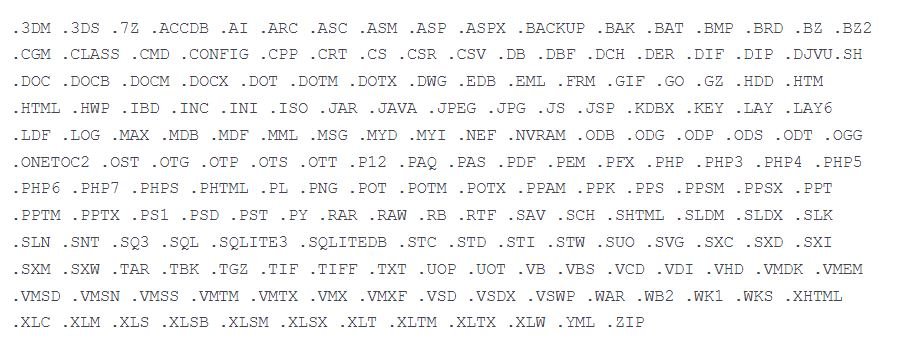
Files with these extensions are overwritten using a fixed number of bytes 0xCC with 1 MB of weight. Upon completion of the overwrite process, the malware renames each infected file with a seemingly random extension.
It is obvious that the hackers behind this campaign do not try to negotiate or reach agreements with the affected organizations, so in the face of an attack as devastating as this, prevention becomes the main resource of the potentially affected organizations.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
