The Malwarebytes Threat Intelligence team has identified a new Remote Access Trojan (RAT), which they named Woody RAT, and which has been active for at least a year.
This advanced custom RAT is primarily the work of a threat actor targeting Russian entities through the use of decoys file format and more recently, Office documents that exploit the Follina.
According to a fake domain registered by the threat actors, they attempted to target a Russian aerospace and defense entity known as OAK.
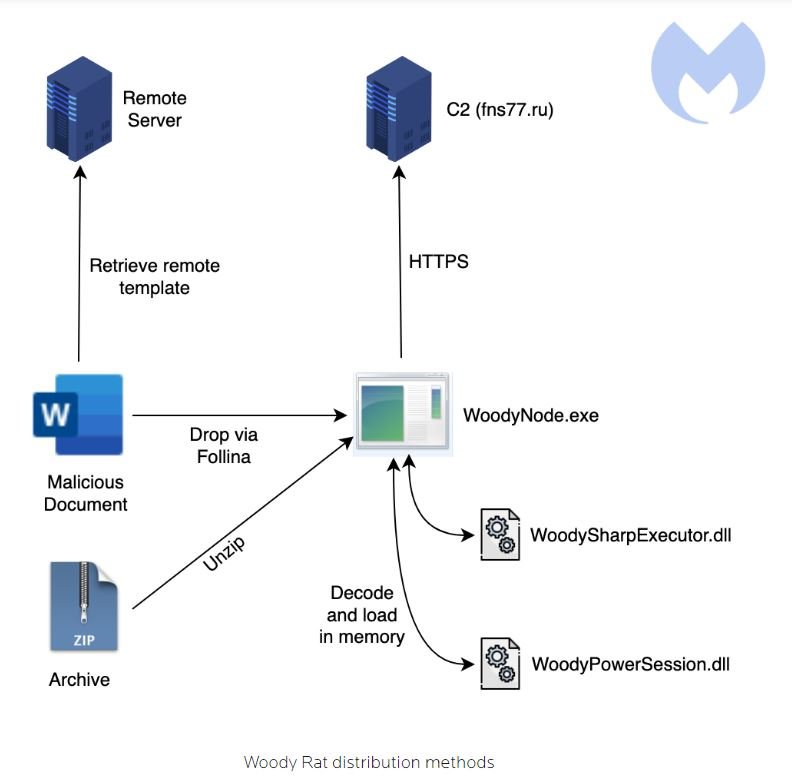
Distribution methods
Woody RAT has been distributed using two different formats: archive files and Office documents using the Follina vulnerability. Early versions were typically distributed in a ZIP file purporting to be a specific document from a Russian group. When the Follina vulnerability became known worldwide, the threat actor switched to it to distribute the payload.
The following diagram shows the general attack flow used by the threat actor to propagate Woody RAT:
Compressed files
In this method, Woody RAT is packaged into a file and sent to victims. These files have been distributed via spear phishing emails and here are some examples:
- anketa_brozhik.doc.zip – Contains the Woody RAT executable with the same name.
- zayavka.zip: Contains Woody RAT masquerading as a valid application.
Follina vulnerability
The threat actor is using a Microsoft Office document (*.docx) that has been armed with the Follina vulnerability (CVE-2022-30190) to download Woody RAT. The lure used in Russian is called “Information Security Memo”, which provides security practices for passwords, sensitive information, etc.

Unknown Threat Actor
Historically, Chinese APTs such as Tonto Teams and North Korea’s Konni have targeted Russia. However, in this case we were unable to collect strong indicators to attribute this campaign to a specific threat actor.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
