A recent report details the operation of a financial and electronic fraud operation deployed by a highly sophisticated and stealthy hacking group, capable of compromising bank transaction processing systems and diverting funds to various locations in Latin America.
The group, identified as Elephant Beetle is characterized by its devastating intrusions into banks and retail companies, hiding its malicious activity among legitimate transactions recorded by the affected organizations. This operation seems to share some features with the ransomware attacks detected in Mexico about 4 years ago.
Experts believe that this group has an arsenal of at least 80 hacking tools and unique scripts, so they can gain persistence in the target system and wait patiently for the opportunity to attack to present itself: “The attacks are based on a deep investigation and knowledge of the financial systems and operations of the victims and their persistent search for vulnerable methods to technically inject financial transactions, which ultimately leads to financial fraud.”
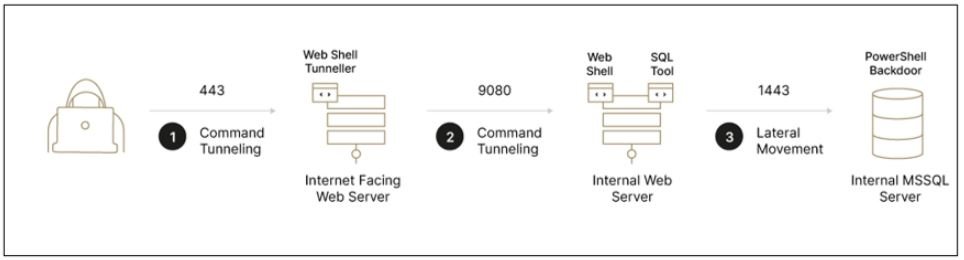
This operation is also characterized by the low profile with which the attackers work, starting with the implementation of a backdoor only to study the target environment and facilitate eventual illegitimate transactions. Eventually hackers start by injecting these transactions, extracting money without drawing the attention of security teams into the affected networks.
Hackers can also efficiently hide their activities in case of emergency; if security teams come to detect malicious activity, Elephant Beetle can interrupt its operations for a couple of months, fully restoring its operations once they believe the detection risk has passed.
Among the security flaws exploited by this group, the following stand out:
- CVE-2017-1000486: Primefaces Application Expression Language Injection
- CVE-2015-7450: WebSphere Application Server SOAP Deserialization Exploit
- CVE-2010-5326: SAP NetWeaver Invoker Servlet Exploit
- No CVE Key: SAP NetWeaver ConfigServlet Remote Code Execution
For security, potentially affected organizations are advised to pay special attention to their payment processing systems, in addition to identifying any potential security weaknesses and applying the necessary fixes before it is too late.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
