Like many other hacking groups, Maze ransomware operators have their own website, and use it to expose their latest victims. In their latest publications, these hackers claim that they have compromised and encrypted the networks of giant multinational company LG Electronics. Although no additional information has been revealed about the alleged attack, hackers claim that the information extracted includes patents from some projects related to large American tech companies.
A growing trend in cybercrime is the task of exposing some stolen information from companies infected with ransomware on websites operated by attackers as a way to force the ransom payment. In this case, the hackers assured that they will continue to publish sensitive information from LG, including source code for some technology projects.
A few hours ago, an alleged member of the hacker group, in conversations with specialized platform BleepingComputer, assured that Maze extracted more than 40 GB of information from LG’s networks, adding that the company has a 24-hour time frame to contact them; should this deadline expire, hackers threaten to post more confidential details.
Regarding the number of compromised devices, the hacker declined to reveal this data, although he noted that evidence of the attack was published on Maze’s website, such as a screenshot showing a list of files in a Python code repository.
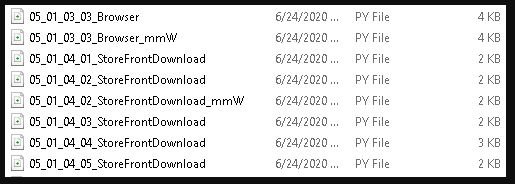
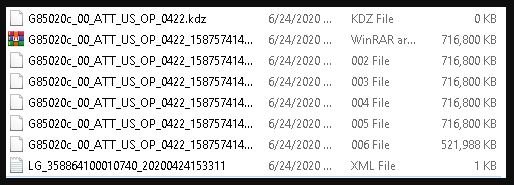
Another screenshot shows a .KDZ, which is the format for LG’s official firmware code; from the details shown by these images, the researchers deduced that the firmware was developed by AT&T.
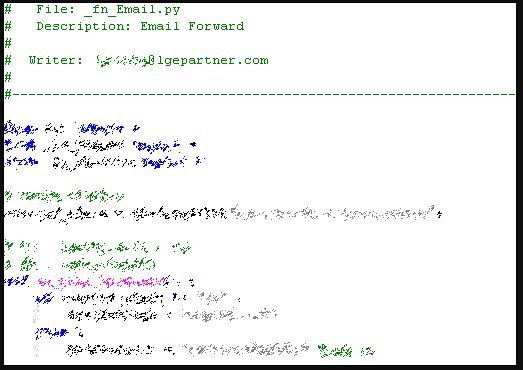
A third screenshot shows a Python snippet for an email forwarding project, as mentioned by cybersecurity researchers.
Since the reports were leaked, multiple members of the cybersecurity community have tried to contact an LG representative, although the company has not responded to these requests for information. For now, LG has only sent automatic emails in response.
There are still no details on how Maze managed to access the company’s networks, although investigators believe the criminals were able to employ remote desktop connection protocols and changes to high-level hosts through compromised administrator accounts. These methods have been identified in previous incidents allegedly linked to Maze’s hackers.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
