A few weeks ago, cybersecurity researchers from Check Point revealed the mode of operation of GuLoader, a tool used by cybercrime groups to deliver various variants of malware abusing cloud services, such as One Drive or Google Drive. According to experts, this attack vector is one of the fastest growing trends in recent months.
A considerable part (about 25%) of the cyberattacks detected on a daily basis are related with the use of GuLoader, which has already been tested by multiple malicious hacking groups involved in more than a dozen attack campaigns.
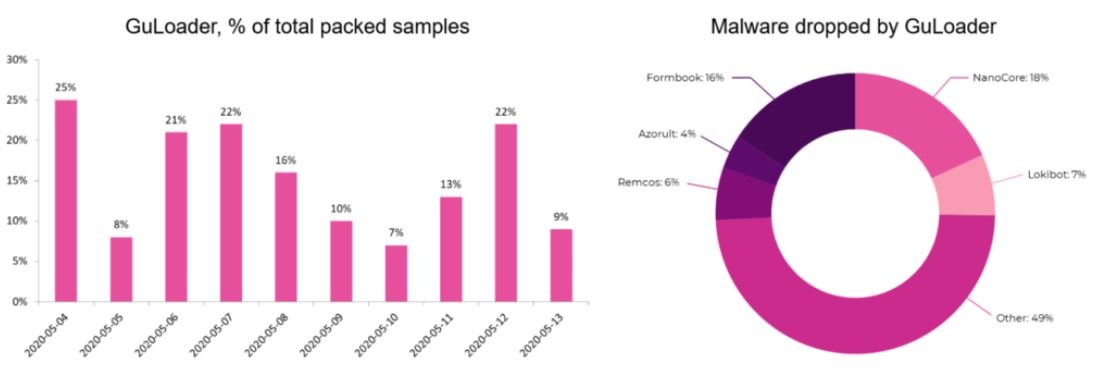
One of the aspects that attracted the most attention about GuLoader is its constant updating process, since the first cases of incident detection this dropper has acquired new techniques of sandbox evasion, code randomization and URL encryption to the command and control server. Because of these features, specialists believe that behind this hacking tool there is a group of people with advanced knowledge and high availability of resources.
Despite these mechanisms, Check Point researchers managed to find the service, discovering that its creation and maintenance was carried out by a legitimate-looking Italian company that could be acting as the front of a criminal organization.
What is DarkEyE?
During the analysis, experts detected multiple samples detected as GuLoader, although they did not have a URL to download the payload. Such samples seemed to be closely related to a malicious development known as DarkEyE Protector.
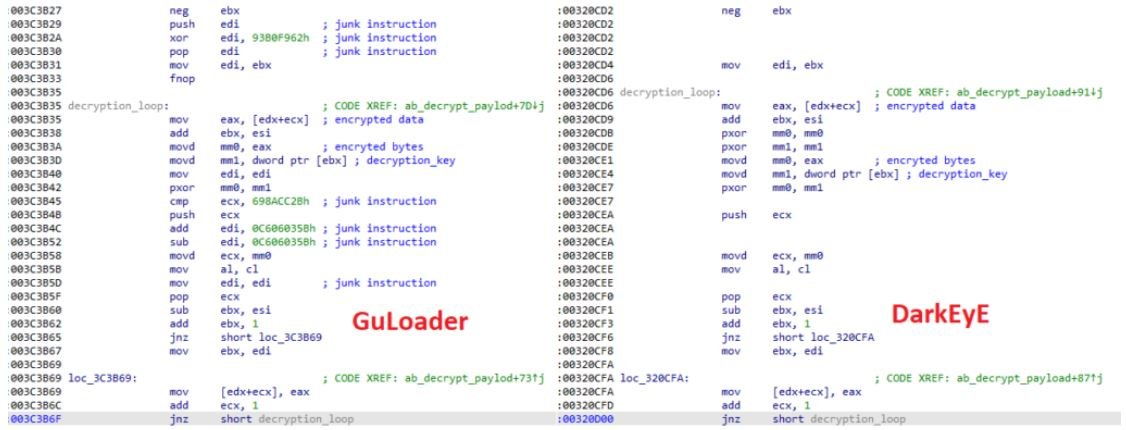
By analyzing the collected samples of DarkEyE and comparing them to GuLoader samples, experts discovered that both were written in VisualBasic and contained a 4-byte XOR-key encrypted shell code. The samples also shared the same payload decryption method.
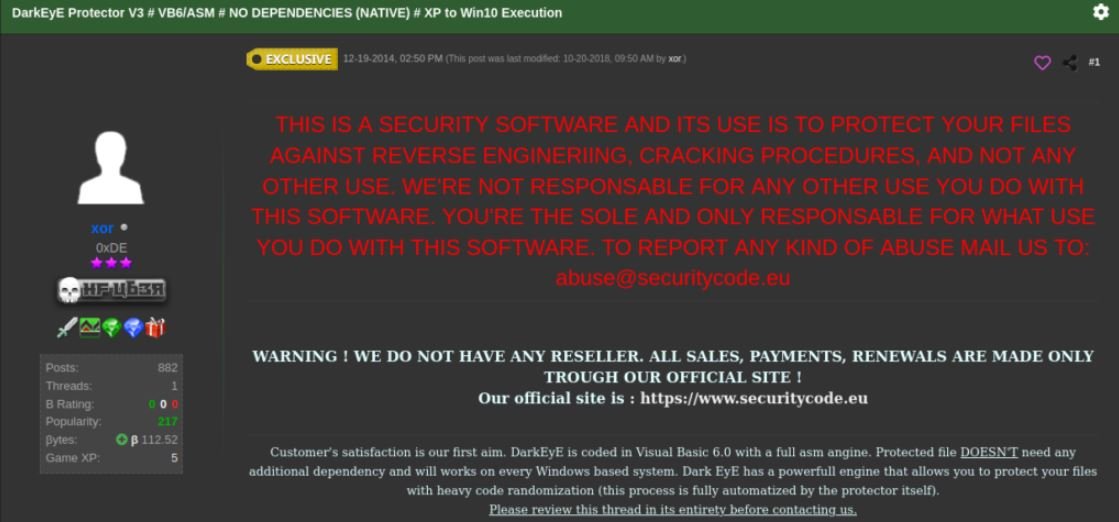
DarkEyE’s appearance dates back to 2014, when user self-appointed “xor” began announcing “DarkEyE Protector” on the Internet.
Other online advertisements about DarkEyE were published by a user known as “sonykuccio“. According to the publications, DarkEyE is a crypter (software used to hide malware using encryption techniques) compatible with multiple variants of malware, such as keyloggers, remote access Trojans, among others.
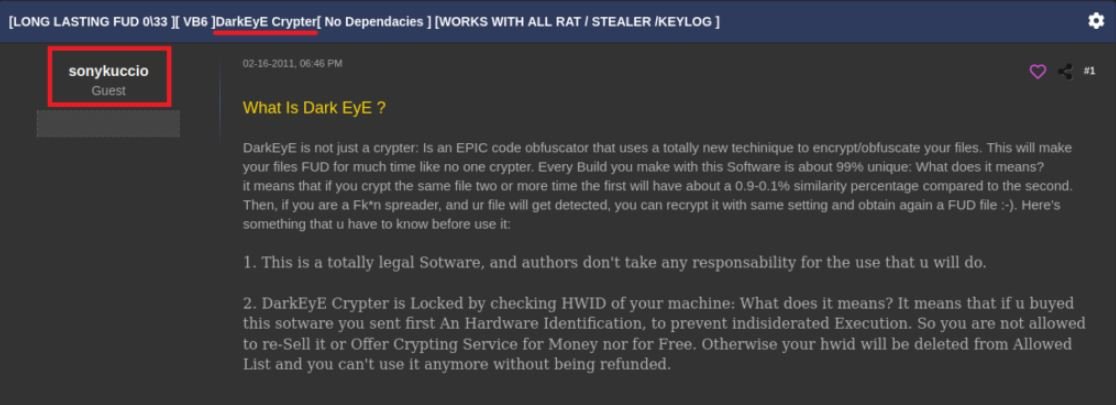
The user “sonykuccio” also published some contact email addresses for users interested in this tool.
DarkEyE Evolution
The analysis led the researchers to the website securitycode.eu, which was linked to DarkEyE since its inception. However, the site now contains information about a development known as CloudEyE.
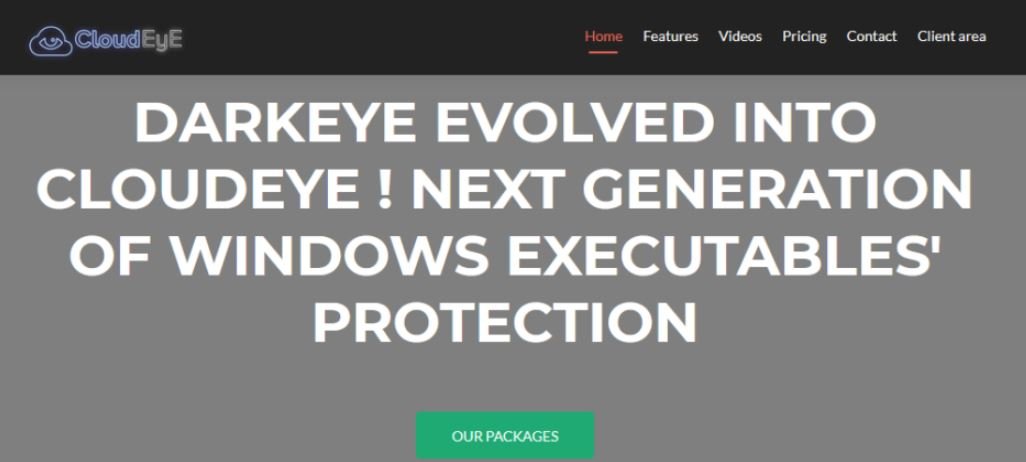
Although this website advertises supposed services for the protection of some Windows applications, researchers found multiple links to tutorials on YouTube about using CloudEyE and some ways to abuse cloud storage services.
In one of these videos, researchers discovered the same URL patterns seen in GuLoader samples. This could be an astonishing coincidence, although the obvious explanation suggests a link between GuLoader and CloudEyE. Specialists decided to purchase CloudEyE to test its effectiveness, which is shown below.
- For testing, experts encrypted the calc.exe application:
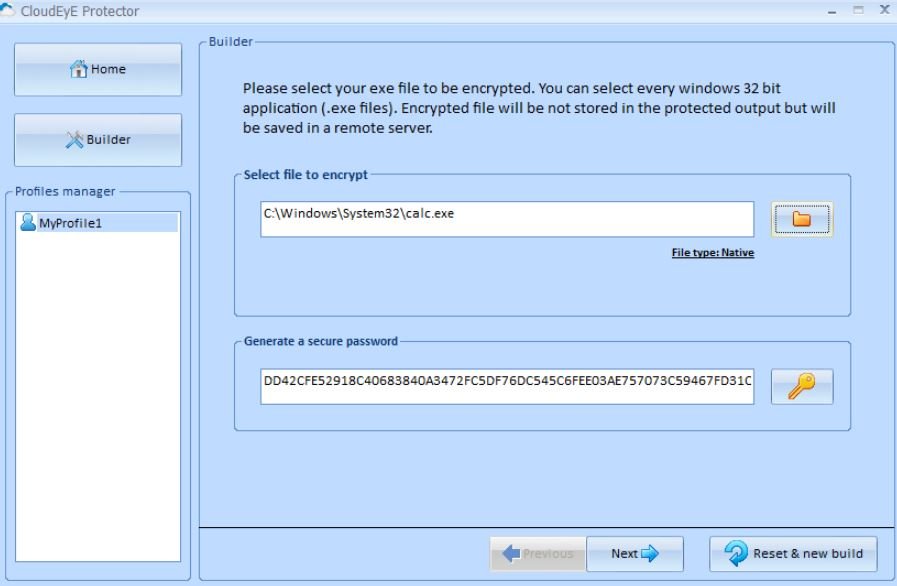
The XOR encryption key (password) is generated automatically and cannot be entered manually.
- After clicking on “Next”, the tool returns the encrypted file. It is then placed on a local HTTP server and the URL is entered in the following window:
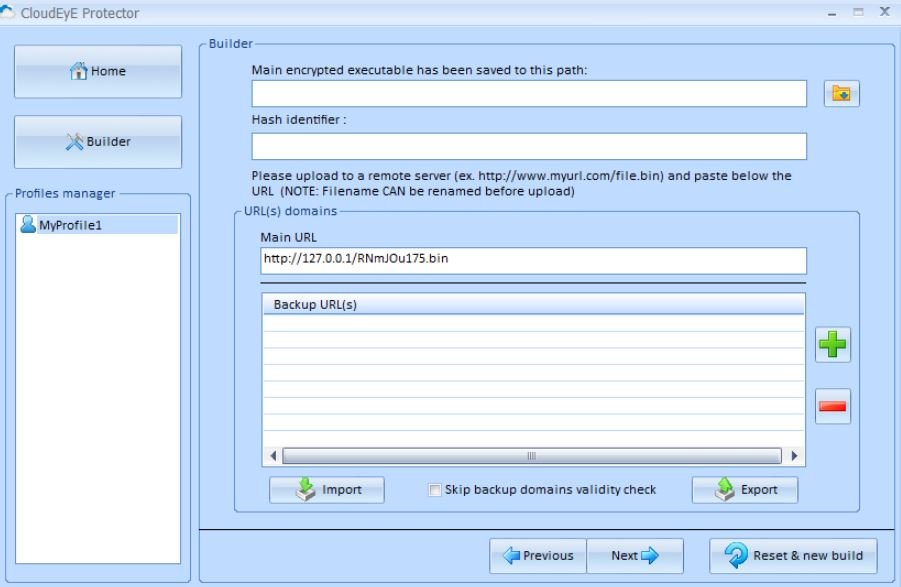
- When you click “Next”, the window with the known URL template appears http://myurl/myfile.bin:
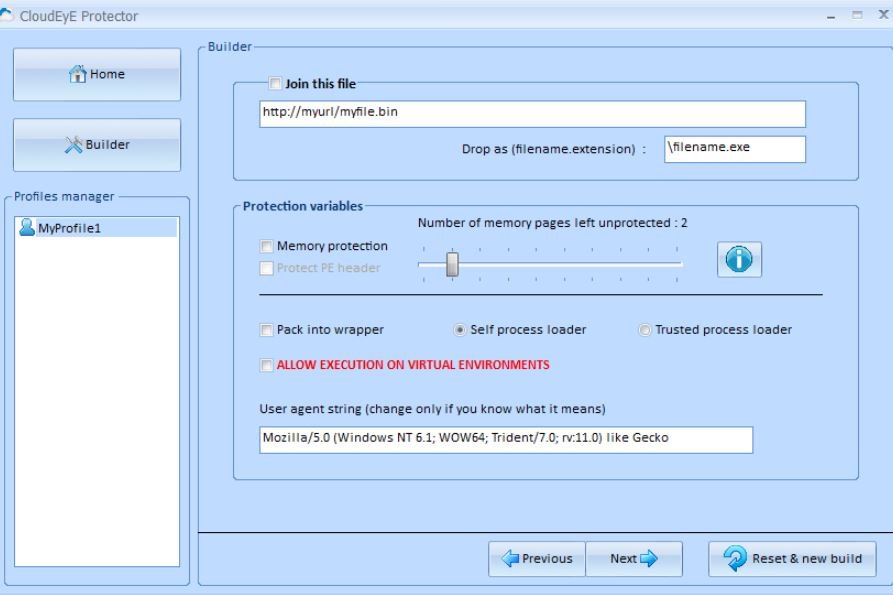
All other options are set by default.
- In addition to encrypting an executable, CloudEyE also allows users to enable other options, such as auto-run mode, choice of a custom icon, file size changes, and even extension changes:
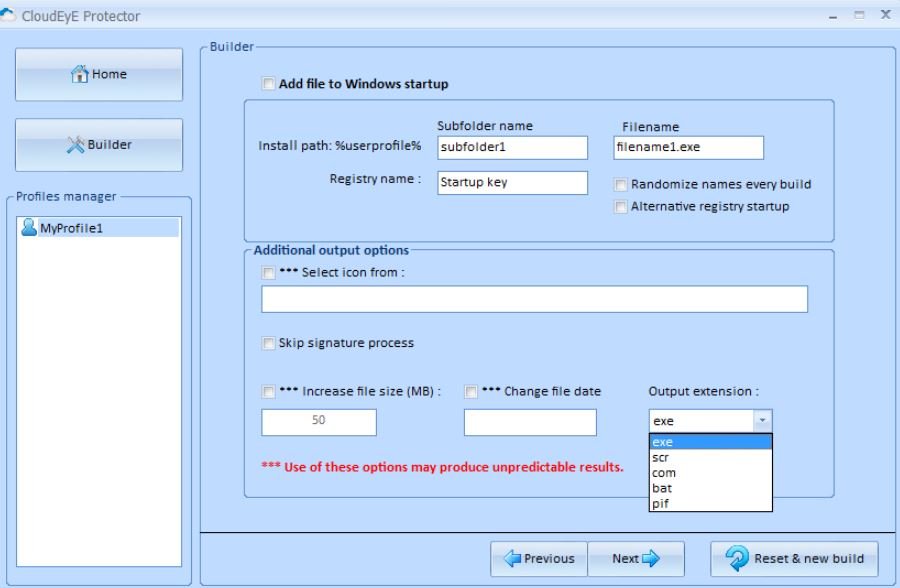
The tool then returns the final build.
- This compilation was put under a sandbox analysis, which confirmed the researchers’ suspicions:
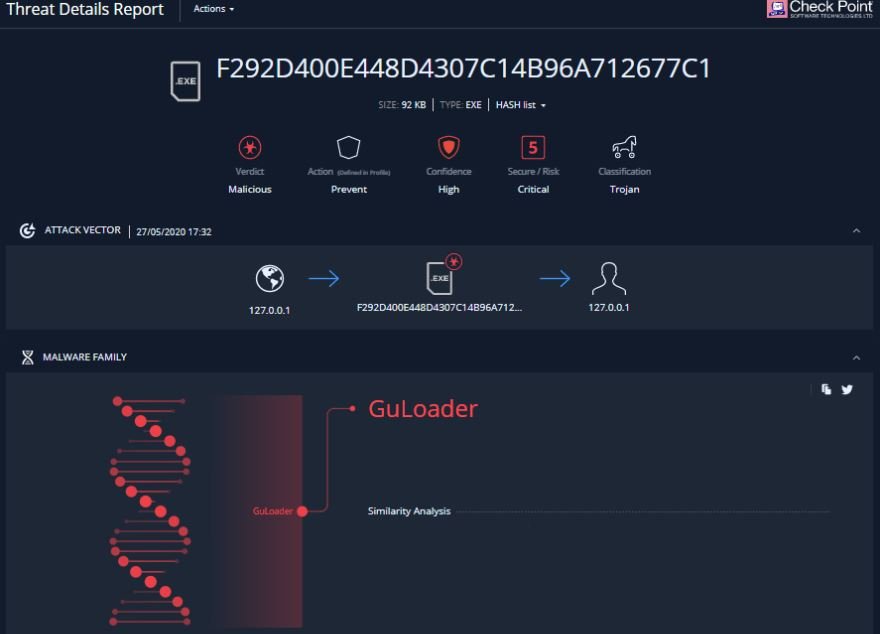
Who is behind these developments?
Two contact email addresses were found in the ads published by “sonykuccio”:
- xsebyx@hotmail.it (Sebyno)
- thedoktor2007@hotmail.it (EveryThing)
The Check Point team searched for these email addresses in all available publicly accessible data sources, finding some links to “sonykuccio”.
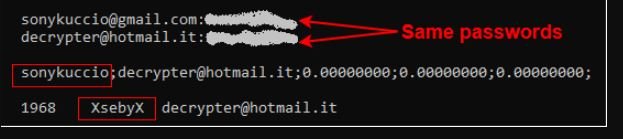
Among the many data that this search produced, a PDF appeared with multiple real personal data of some Italian citizens, mainly from an individual named Sebastiano Dragna.

In addition, the same name is located in the website’s Privacy Policies. Researchers believe this should be an alias, given the nature of the services advertised on that website.
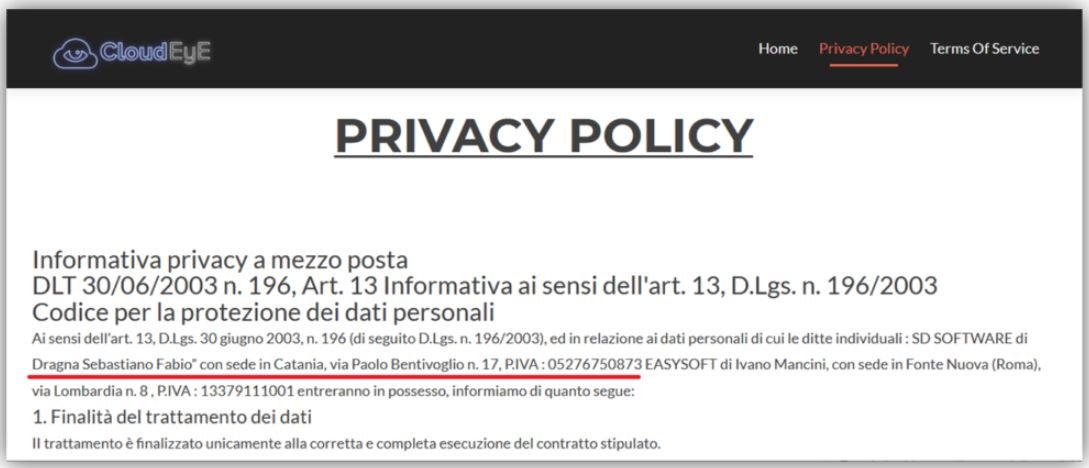
Ivano Mancini’s name also appeared in these advertisements. Unfortunately, Check Point failed to find any link between this name and the information published in various hacking forums.
Although the nickname “sonykuccio” has been frequently appearing on hacking forums offering DarkEyE for at least eight years ago, this user was already involved in multiple hacking campaigns previously.
The website securitycode.eu claims to serve more than 5,000 customers, so researchers believe this front-end company generates revenue of about $500 USD per month.
Even though its operators try to make this tool look like a conventional cybersecurity service, it is really obvious that this is a sophisticated malicious tool that could be linked to thousands of cyberattacks, so the authorities should take a more proactive role towards this company.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
