A group of cybersecurity specialists has detected a campaign for the distribution of a Remote Access Trojan (RAT) disguised as an alleged sexual video of President Donald Trump via emails.
These messages, which bear the subject line “GOOD LOAN OFFER”, contain a Java file titled “TRUMP_SEX_SCANDAL_VIDEO.jar”. If users download the file, they will actually be installing the malware Quaverse RAT (QRAT), also known as Qua.
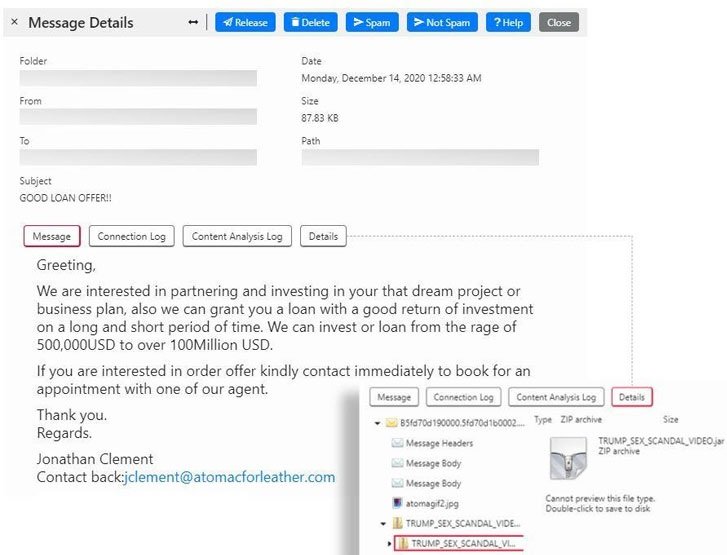
In their report, experts mention that threat actors are trying to take advantage of the anticipation generated by the recent U.S. presidential election, even believe the name of the file was last-minute modified as it has no relation to the subject line in the email. Trustwave experts mention that this appears to be an extension of the most recent campaign linked to this group and detected in August 2020.
It all starts with the spam email containing the attachment or, if not, a link to a malicious zip file. Any of these files retrieve the JAR file (“Spec-0034.jar”), encoded with the Java Allatori obfuscator.
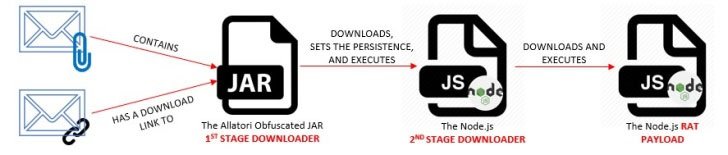
The downloader configures the Node.Js platform on the system and then downloads and runs a second downloader called “wizard.js” to generate persistence and obtain Qnode RAT from a server controlled by the threat actors.
A recent inclusion of this attack is an emerging alert to notify the victim that the running JAR is remote access software used for pentesting. Experts mention that this indicates that malicious activity will begin to manifest when the user clicks the “OK” button on the pop-up alert.
The Trojan has received multiple updates, including the now base64-encrypted code: “This threat has improved significantly since it was first detected,” the specialists add.
Needless to say, users are advised to ignore any suspicious messages, whether sent by an unknown user or to include content that is too attractive to be true. The best way to prevent these infections is to identify a threat before opening the email.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
