When analyzing the most ambitious phishing campaigns, researchers often intuit the deployment of complex techniques and procedures. Nonetheless, the increasing use of the URL forwarding technique for deploying multi-layer phishing attacks has become a simple but effective method for operating powerful phishing attacks.
According to cybersecurity awareness specialists at the International Institute of Cyber Security (IICS), URL redirection involves redirecting Internet users from an originally requested URL to a completely different platform. This is something that all users go through every day, so threat actors don’t hesitate to try to exploit it to their advantage.
This time, we’ll show you the three most common ways this attack is applied, as a way to disseminate information about one of the most common cybercriminal practices. Remember that cybersecurity awareness can be critical for any organization, as most cyberattacks can be detected by a trained user.
HTML files encoded and in JavaScript with redirection to the inside
Cybersecurity awareness experts mention that this is a rare type of attack, as it requires a lot of elements like:
- Emails with HTML files attached
- URL-encoded phishing redirect in HTML file that takes advantage of set-timeout method
- The phishing homepage
These attacks usually start with an email sent by unknown users posing as IT administrators. The content of the message may vary, although the constant is the appearance of an attachment with the apparent URGENT title.
These attachments are actually coded scripts that, when decrypted, display the phishing URL to which the user will be redirected after the setTimeout method is applied. This method is used to execute a function after a default number of milliseconds.
After the file is opened in a browser, for example, the setTimeout method executes the redirect and the target user is sent to a malicious website disguised as the home page of platforms like Office 365, cybersecurity awareness experts mention.
Phishing emails distributed via Adobe open redirection
Hackers also turn to the use of compromised email accounts to trick IT administrators by faking the identity of other organizations, which makes them more likely to fall into the trap. In the following example, cybersecurity awareness experts show us a message received by an IT administrator and allegedly sent by Microsoft to notify you that your Office 365 credentials expire in a day, so they are prompted to change it or choose to click a button that mentions the “Keep current password” option.
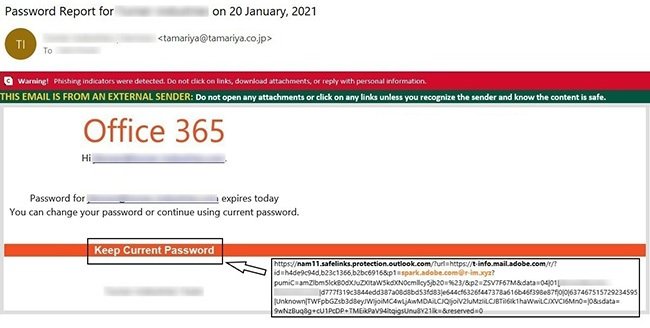
If the user chooses this option, they will be redirected to a fake Office 365 website hosted in malicious domains (in this case, r-im.xyz) through Adobe services. Abusing Adobe’s Open Redirection Services (t-info.mail.adobe.com) adds legitimacy to the URL and increases the chances of email eluding detection, cybersecurity awareness specialists mentioned. Hackers may also abuse the redirection service of other large companies, including Google.
Abbreviated URLs to hide phishing sites
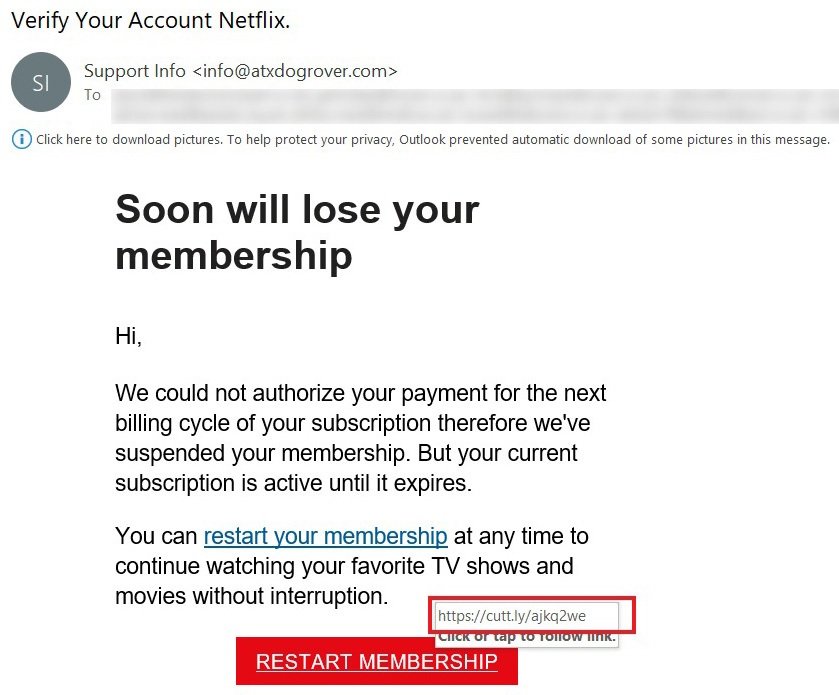
Phishing website operators can also use services to trim URLs such as bit.ly or cutt.ly to hide malicious web addresses used in phishing campaigns. In the following example, cybersecurity awareness experts describe a recent phishing campaign in which threat actors use a fake Netflix login as the theme.
The message received by users includes a “Restart Membership” button, which when selected opens a counterfeit Netflix login page, whose URL (https: //www.propertyoptionsdevelopments.com/netflx20/) was cropped via cut.ly (https://cutt.ly/ajKQ2We). Needless to say, this address is unrelated to Netflix.
Phishing remains one of the most common cybercriminal practices, so cybersecurity awareness is critical to preventing potential security risks associated with sending emails with attachments. For further reports on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses fell free to visit the International Institute of Cyber Security (IICS) websites, as well as the official platforms of technology companies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
