Nmap is one of the most popular tools for researchers who perform penetration or recognition testing, making it an ideal choice for port scanning. However, pentesting experts from the International Institute of Cyber Security (IICS) mention that there is a considerable disadvantage with Nmap: the time it takes to run a scan on all ports, a process that can take up to 20 minutes.
A tool developed by a group of experts can be the solution to this inconvenience, as its creators mention that this new tool can perform this process in less than a minute.
Pentesting experts will then review RustScan’s installation and execution steps. To get started, let’s see what it takes to use this tool:
- A computer with Kali Linux
- A target to scan. Note that running an analysis of this intensity is likely to block the victim or services, depending on the parameters you use, so be very careful and run it first on machines with permission
Installation
- On your Kali Linux device, go to the official RustScan repository and download the .deb file from the link below
- https://github.com/brandonskerritt/RustScan/releases
- Open the terminal and type the following, note to change the version number to the current one you downloaded:
cd Downloads
dpkg -i rustscan_1.2.0_amd64.deb
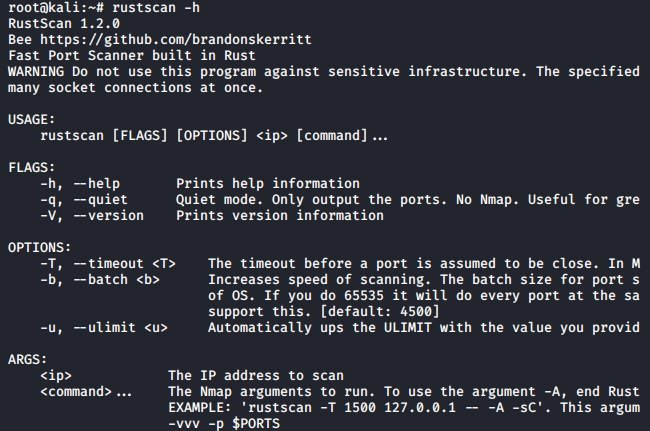
- Run the following help command to ensure that it is installed correctly:
rustscan -h
- According to pentesting experts, the answer should look like the following screenshot:
Using the tool
- To run a basic scan, run the following command:
rustscan -b 500 -T 1500 192.168.0.1
- -b 500 is the lot size
- -T 1500 is the waiting time in ms
The lot size determines how fast RustScan scanning is, IICS pentesting experts mention. If you set it to 65k, it will run all 65 thousand ports at the same time; On the other hand, if the batch size is set to 65k and the timeout is 1000ms, RustScan will scan at 1 second depending on whether your operating system can tolerate it.
The lot size determines how fast RustScan scanning is, IICS pentesting experts mention. If you set it to 65k, it will run all 65 thousand ports at the same time; On the other hand, if the batch size is set to 65k and the timeout is 1000ms, RustScan will scan at 1 second depending on whether your operating system can tolerate it.
rustscan -T 1500 127.0.0.1 -- -A –sC
- Double hyphen indicates the end of RustScan arguments and the beginning of Nmap arguments
For more reports on this and other useful tools for pentesting and more computer security methods, you can visit the official platforms of the International Institute of Cyber Security (IICS).
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
