Search engines such as Shodan, Censys or Zoomeye are very useful for specialists in ethical hacking, since they allow detecting vulnerable services, exposed devices and other security risks. However, many ignore the existence of other services similar to those mentioned above, such as the recently popular Leakix.
According to specialists from the ethical hacking course of the International Institute of Cyber Security (IICS), Leakix is a new project for scanning subnets and gathering information. This is a free tool and runs in three modes:
- Services: Focuses on search engine results
- Leaks: Services that use weak passwords
- Web applications: This element is still in development, so its operation is about to be improved
In addition to the main functions, Leakix has an API and good statistics. The API function allows you to automatically use the results of the broadcast in your projects. For convenient viewing, you need to install the jq utility.
$ sudo apt-get install jq
The API allows you to filter requests between Services and Leaks, or receive from all sections
$ curl -sqH'Accept: application/json'
https://leakix.net/host/78.47.222.185'|jq
The following query allows you to search among Services:
$ curl -sqH'Accept: application/json' 'Search results for *
This query allows you to search through leaks:
$ curl -sqH'Accept: application/json' 'Search results for *
For a better result, Leakix has search operators that allow you to get much more accurate results. Next, the experts of the ethical hacking course will show you what syntax can be used in this service.
Search operators
- ports 3305 to 3308: You can specify a range of ports. In this example, the search is performed on ports in the range [3305 and 3308]
- timestamp: {* TO 2020-05-01}: Shows all results until May 1, 2020
- timestamp:>=2020-05-01: syntax >, >=, <, and <= can be used to search by time periods
- ip: (>=212.0.0.0 and <213.0.0.0): Search in the IP range
- ip:”212.0.0.0/8″: Search for a specific network
By default, additional declarations are optional if there is at least one request. A foo bar baz search will find any result that contains one or more foo, bar, or baz. There are also logical operators that can be used in the query chain itself to provide more accurate results, mention the specialists of the ethical hacking course. For example, a request as shown below:
apache nginx + index of –authorization
- index of – Must be present
- authorization – Must be absent
- apache nginx – Optional, the presence of these words will improve the quality of the problem
The popular logical operators AND, OR, and NOT (also spelled &&, ||, and !) are also supported, but note that they do not follow normal precedence rules, so parentheses should be used when using multiple operators together. For example:
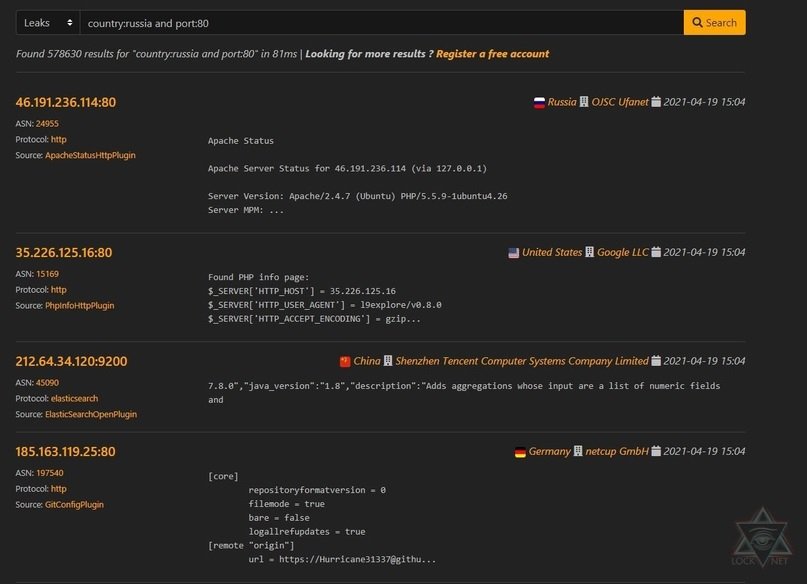
country:russia AND port:80
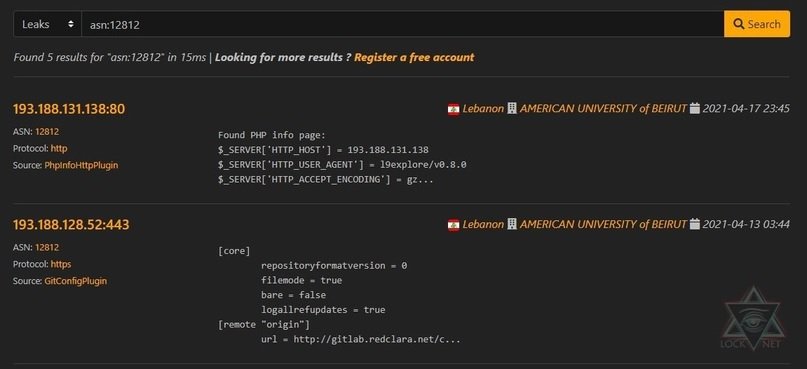
asn:12812
protocol:redis
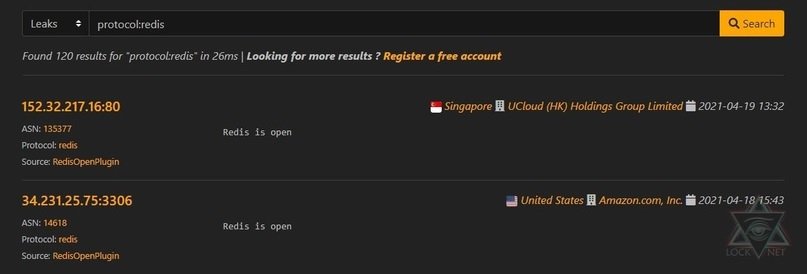
Examples of common requests between Leaks
zookeeper – software that takes care of synchronization and is available without password
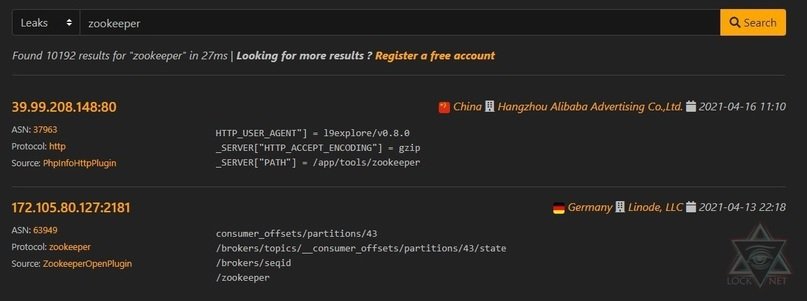
It is worth considering that Leakix is a voluntary project and does not have a paid subscription. While it does not yet have a number of users close to that of giants such as Shodan, Zoomeye or Сensys, specialists in the ethical hacking course believe that the service is quite promising. A big advantage is the availability of the API and Filter mode, in which servers with open databases, configurations, and more appear fairly quickly.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
