QR code (Quick Response) is the name by which we all know the modules to store information in a dot matrix or in a two-dimensional barcode. This matrix is read on a mobile device by using a QR reader/scanner and, in doing so, we are redirected directly to a website, location, email address or social media profile.
Although this technology was introduced in 1994, its popularity skyrocketed with the use of smartphones. Currently we can find these QR codes in restaurants, shopping centers, public offices and any other place where it is required to quickly access a specific web address.
Like other technological implementations, threat actors have devised all kinds of attacks based on the use of QR codes, demonstrating a great capacity for adaptation. Today, specialists from the cyber security course of the International Institute of Cyber Security (IICS) will show you how to hack a device using a simple QR code.
This attack is based on the use of QRGen, a tool to create QR codes very easy to use. Before continuing, as usual we remind you that this material was prepared for informational purposes only and does not represent a call to action, so IICS is not responsible for the misuse that may occur to this information.
Installation
The first step is to download the tool from the GitHub repository, mention the experts of the cyber security course.
git clone https://github.com/h0nus/QRGen.git
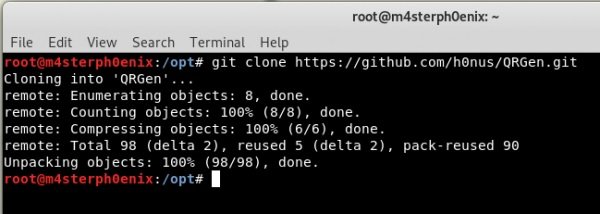
Once downloaded, change the directory with cd:
cd /QRGen
Let’s take a look at the README.md file:
Next, it is required to install some requirements and libraries for the correct functioning of the tool:
pip3 install -r requirements.txt
If this command does not work, the cyber security course specialists recommend trying the following alternative:
python3 -m pip install -r requirements.txt
Creation of a malicious QRCode
After successfully installing QRGen, we will run the tool to generate our payload.
python3 qrgen.py
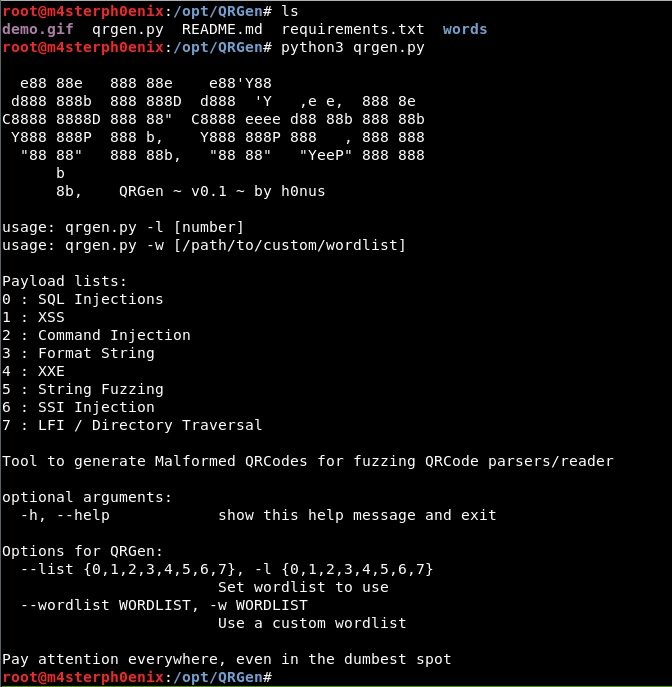
As you can see, generating a payload is really easy.
python3 qrgen.py -l 5
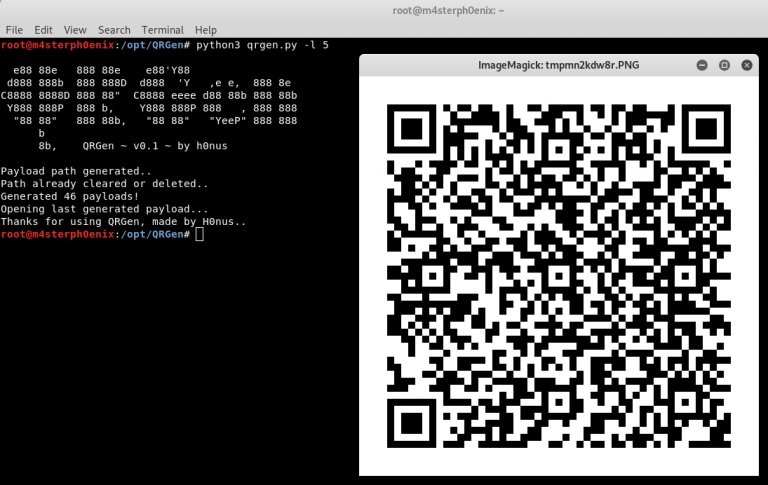
Subsequently, a series of QR codes will be generated and the last one generated will automatically be opened:
cd genqr
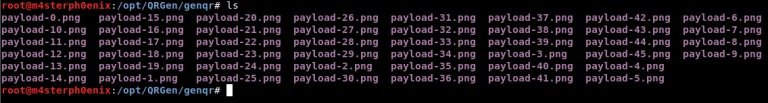
Now scan this QR code, mention the experts of the cyber security course:
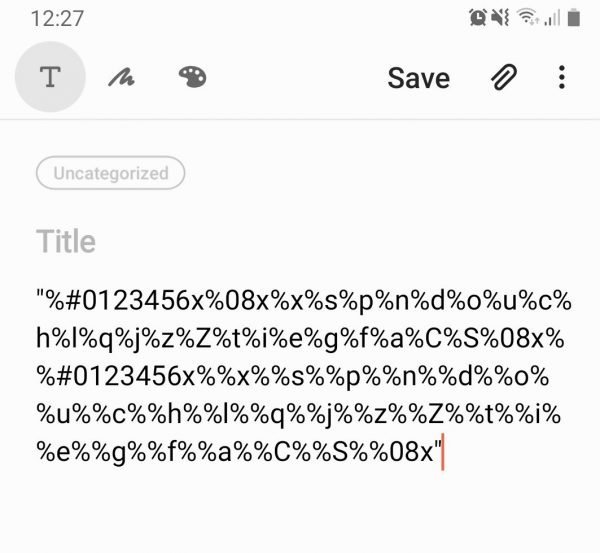
Remember not to test this tool without the prior consent of the administrators of the target system.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
